

In the past, the network perimeter provided a hard outer shell around all of its data and applications. This kept everything contained, enabling security and IT teams to easily manage employee identities internally. However, as employee numbers escalated, virtual private networks (VPNs) became part of the perimeter and took over the job of authenticating employees when they were off-premise.

But with the increasing popularity of cloud, infrastructure as a Service (IaaS), Platform as a Service (PaaS) and Software as a Service (SaaS), in recent years more applications have moved outside the firewall. What is more, external partner and customer users are now accessing both on-premise and cloud applications, some behind a firewall and some not, thereby creating additional identity management challenges outside of the traditional perimeter.
With the traditional perimeter disappearing and the increased use of cloud applications, business managers can now purchase cloud services on the spot – all they need is a credit card. In some cases, organisations have informal infrastructures of servers, applications and data that have been acquired in this manner. When this happens, the central IT group usually has little control over the service, which creates significant security challenges for the content in the cloud.
What’s lurking in the shadows?
When shadow IT components become part of the infrastructure, users create new identities to access them, possibly using the same username and password as they do on the enterprise systems, which multiplies the security risks. In some instances, users will generate new usernames and passwords for each service, collecting a variety of 'shadow identities' that must be managed alongside their enterprise credentials.
The challenge for IT security is that the more fragmented these shadow components are, the more difficult it becomes to manage identities and access. For example, if identities are not being centrally managed, it can become impossible to remove access when an employee changes job roles or leaves the organisation.
The concepts of 'inside the network' and 'outside the network' have no meaning anymore. The traditional perimeter is gone, so organisations have to change how they manage security and user identities if they want to keep their data and applications secure. In this new landscape, identity must become the security perimeter.
How can ID and access management help prevent intrusions?
Identity risk analytics can prevent the next intrusion. As your organisation expands, roles and entitlements can start to overlap and proliferate. And as 'entitlement creep' occurs, policy violations and overall risks abound. Identity risk analytics can provide key information to help you identify and remediate these threats quickly.
These analytics can be static, such as an offline role discovery and analysis process, or real-time, highlighting segregation of duties violations at the time of assignment. A comprehensive approach to identity risk should include both approaches.
Good identity analytics help minimise risk by enabling businesses to:
• Collect data, correlate access rights to their owners and perform a basic clean-up of unnecessary entities e.g. orphan accounts, excessive access, etc.
• Formulate an identity compliance model, including mapping of regulations to written policies – in the form of control objectives – then mapping these control objectives to an implementation of IT controls, such as segregation of duties constraints.
• Verify IT controls in real-time as part of privilege clean-up, certification, provisioning and other identity processes.
• Periodically test the IT controls by conducting business/IT reviews or certification.
• Correct entitlements that are out-of-pattern relative to other.
• Identify users with the same roles.
• Detect overlapping or redundant roles.
• Detect and prevent segregation-of-duties violations during provisioning.
Identity risk analytics
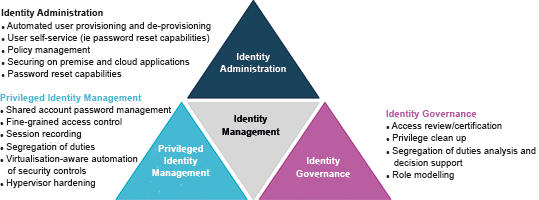
Identity risk analytics addresses governance, identity compliance and role management challenges with an integrated lifecycle approach based on a centralised entitlements warehouse, process automation and powerful analytics engine. This approach can deliver rapid time-to-value, enabling organisations to establish a role model quickly, in weeks rather than months, with better access rights coverage, often 70 to 80%, and better alignment to business needs and preferences.
Identity compliance
Identity compliance activities focus on verifying that the access maintained by users is in adherence with regulatory requirements and internal security policies.
Are South African companies doing enough to safeguard their corporate data against illegal access? In order to implement safeguards South African security teams must find a way to manage identities and authenticate all users via their identity services before they access the applications they need. This approach can simplify access management for all user types.
• Employees can still be authenticated against the corporate directory. However, contextual, multi-factor, risk based authentication should be available for high-value transactions or access to sensitive applications. For example, if a user normally logs in from the office or his/her home in South Africa during normal business hours, but a log-in attempt is made from Europe in the middle of the night, the service should refuse the authentication or demand step-up authentication.
• Privileged administrators can be a challenge, because they often have more access entitlements than they need, and they share the use of a common account (e.g., root or administrator). To combat this, a central authentication service should act much like it does for employees, but when a privileged user logs in; he/she will be given a single-use password for that individual session – eliminating the lack of accountability that is endemic to shared account use.
Organisations must manage ongoing IT security challenges and changing regulatory requirements that necessitate them to control and govern the actions of privileged identities.
Failure to govern and control privileged identities could result in data loss or destruction, malicious or inadvertent damage, fines, and even lawsuits. The processes for reviewing and approving administrators’ access rights and policies are often manual, labour intensive and inefficient, making real-time adherence to segregation of duties and other compliance policies very difficult.
Dangers of not having an adequate ID and access management solution
The new open enterprise makes managing user identities and entitlements more difficult than in the past. Robust perimeter security used to be sufficient. Now, the increasing number of users, many of whom have been granted excessive privileges, creates an entirely new set of vulnerabilities that can be more easily exploited from remote locations than ever before.
Among the immediate identity management challenges facing IT organisations is determining how to:
• Eliminate 'privilege creep' through ongoing automated certification of all users.
• Automate identity processes to replace costly, error-prone manual processes.
• Simplify identity lifecycle management through increased automation.
• Improve employee productivity by eliminating time-consuming, paper-based certifications.
• Simplify the user experience by streamlining access to apps, enabling self-service and supporting mobile users.
• Support both cloud and on premise environments while using a single authentication credential.
Can biometrics be used to protect corporate data?
The use of biometric technology is no longer a futuristic concept. Consumers are unlocking their smartphones with their fingerprint, and biometric devices are also being implemented in hospitals to reduce the risk of medical identity fraud. Smartphones are thought to be the next big driver for fingerprint biometric authentication.
For more information contact Michael Horn, CA Southern Africa, +27 (0)11 417 8765, [email protected]

© Technews Publishing (Pty) Ltd. | All Rights Reserved.