
Sophos has released its annual international survey and review of real-world ransomware experiences in the State of Ransomware 2022. The report shows that 51% of South African organisations surveyed were hit with ransomware in 2021; and 49% of the organisations that had data encrypted paid the ransom to get their data back, even if they had other means of data recovery, such as backups.
The report summarises the impact of ransomware on 5600 mid-sized organisations in 31 countries across Europe, the Americas, Asia-Pacific and Central Asia, the Middle East and Africa.
“The survey shows that, globally, the proportion of victims paying the ransom continues to increase, even when they may have other options available,” said Chester Wisniewski, principal research scientist at Sophos. “There could be several reasons for this, including incomplete backups or the desire to prevent stolen data from appearing on a public leak site. In the aftermath of a ransomware attack there is often intense pressure to get back up and running as soon as possible. Restoring encrypted data using backups can be a difficult and time-consuming process, so it can be tempting to think that paying a ransom for a decryption key is a faster option. It’s also an option fraught with risk. Organisations don’t know what the attackers might have done, such as adding backdoors, copying passwords and more. If organisations don’t thoroughly clean up the recovered data, they’ll end up with all that potentially toxic material in their network and potentially exposed to a repeat attack.”
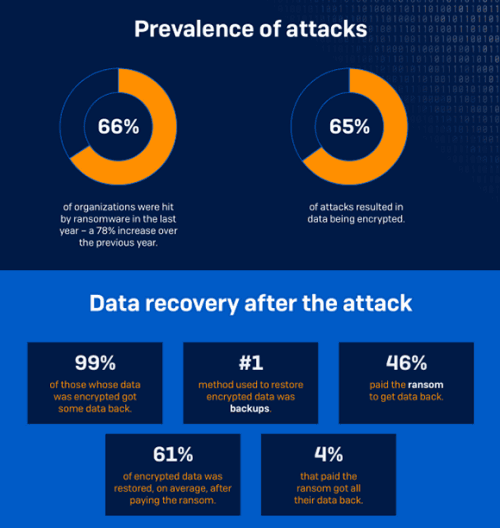
The main findings for South Africa in the State of Ransomware 2022 global survey, which covers ransomware incidents experienced during 2021, as well as related cyber insurance issues, include:
• A significant number of victims are paying the ransom.
• The impact of a ransomware attack can be immense. The average cost to recover from the most recent ransomware attack in 2021 was US$ 710 000. It took on average one month to recover from the damage and disruption. A huge 95% of organisations said the attack had impacted their ability to operate, and 92% of the victims said they had lost business and/or revenue because of the attack.
• Many organisations rely on cyber insurance to help them recover from a ransomware attack; 77% of mid-sized organisations had cyber insurance that covers them in the event of a ransomware attack and in 99% of incidents, the insurer paid some or all the costs incurred.
• A substantial 93% of those with cyber insurance said that their experience of getting it has changed over the last 12 months, with higher demands for cybersecurity measures, more complex or expensive policies and fewer organisations offering insurance protection.
“The findings suggest we may have reached a peak in the evolutionary journey of ransomware, where attackers’ greed for ever higher ransom payments is colliding head on with a hardening of the cyber insurance market as insurers increasingly seek to reduce their ransomware risk and exposure,” said Wisniewski.
“In recent years, it has become increasingly easy for cybercriminals to deploy ransomware, with almost everything available as-a-service. Second, many cyber insurance providers have covered a wide range of ransomware recovery costs, including the ransom, likely contributing to ever higher ransom demands. However, the results indicate that cyber insurance is getting tougher and in the future ransomware victims may become less willing or less able to pay sky high ransoms. Sadly, this is unlikely to reduce the overall risk of a ransomware attack. Ransomware attacks are not as resource intensive as some other, more hand-crafted cyberattacks, so any return is a return worth grabbing and cybercriminals will continue to go after the low hanging fruit.”
Sophos recommends the following best practices to help defend against ransomware and related cyberattacks
1. Install and maintain high-quality defences across all points in the organisation’s environment. Review security controls regularly and make sure they continue to meet the organisation’s needs.
2. Proactively hunt for threats to identify and stop adversaries before they can execute their attack. If the team lacks the time or skills to do this in house, outsource to a managed detection and response (MDR) specialist.
3. Harden the IT environment by searching for and closing key security gaps: unpatched devices, unprotected machines, open RDP ports, etc. Extended detection and response (XDR) solutions are ideal for this purpose.
4. Prepare for the worst. Know what to do if a cyber incident occurs and keep the plan updated.
5. Make backups, and practice restoring from them so that the organisation can get back up and running as soon as possible, with minimum disruption.
Read The State of Ransomware 2022 report for the full global findings and data by sector at www.sophos.com/en-us/content/state-of-ransomware

© Technews Publishing (Pty) Ltd. | All Rights Reserved.