
Contactless access technologies quickly evolved from ‘nice-to-have if you have the money’ technology into must-have solutions when the pandemic struck and (some may say for the first time) people actually had a good reason to be wary of touching biometric readers. While contactless biometrics have been with us for some time, their use has not been as widespread and popular as traditional fingerprint technologies.
Some of the contactless technologies in use today that have been around for a while include iris or retina, facial and palm vein readers. More recently we saw contactless fingerprint readers appearing and these quickly became popular (even before the pandemic, but they are much more popular nowadays). Covid-19 has also driven the adoption of facial recognition, although this technology has also been with us for some time, however, the pandemic and the increased reliability of and trust in facial readers seem to have converged at an opportune moment.
While we will no doubt spend more time addressing the various contactless technologies available in the Access & Identity Management Handbook 2022, which will be finalised at the end of the year, residential estates have also had to ‘make a plan’ when it comes to access control to avoid the hassles of dealing with people who don’t want to touch public surfaces – like biometric fingerprint readers.
Some have reverted to traditional access cards since only your card touches a public surface, others have made the move to mobile access credentials where your smartphone contains your credentials and waving it near a reader grants access. Still others have opted for contactless facial or fingerprint readers, even allowing additional analytics to run on facial systems as added security precautions.
To give our estate security operatives some insight into the latest in contactless technologies for access control, Hi-Tech Security Solutions spoke to three leading players in the access game:
• Ariel Flax from ATG Digital.
• Nicolas Garcia from IDEMIA.
• Walter Rautenbach from neaMetrics, local distributor of Suprema.
Hi-Tech Security Solutions: Many residential estates are moving to contactless access control technologies, what systems and solutions can you offer in this regard for access at gates and entrances to buildings (such as golf clubs or conference centres)?
Flax: We offer a touchless gate access control system called At The Gate for vehicle and pedestrian traffic at access points. Then we have a touchless, self-service visitor registration solution called At Reception, which is ideal for use at reception desks, guest check-in counters and more.

At The Gate comprises a customisable digital scanner that retrieves data directly from vehicle and driver’s licence or ID card, and captures any information you require upon sign in, such as ‘reason for visit’. Security guards need only ‘point and shoot’, so to speak. It’s 100% PoPIA-compliant, secure and fast, alleviating congestion at the gate.
At Reception is a self-service tablet solution with customisable software to allow for a seamless check-in/out. Guests can receive an invitation via WhatsApp or our mobile application with a QR code or a link to register for verification on arrival. The host receives an instant notification that their guest is onsite.
To make Covid-safety protocol enforcement easier, our pre-screening feature enables offsite pre-visit screening for Covid or any other pre-visit induction requirements.

Garcia: We have been working closely with residential estates over the past three years to present the advantages of contactless biometrics to them and we continue to do so today. Through our solutions, we offer a full frictionless experience with contactless fingerprint scanning (MorphoWave) and/or facial recognition (VisionPass). Both solutions are very robust and performant, so it comes down to the user’s needs and preferences. Our solution adapts to the user needs and not the other way around.
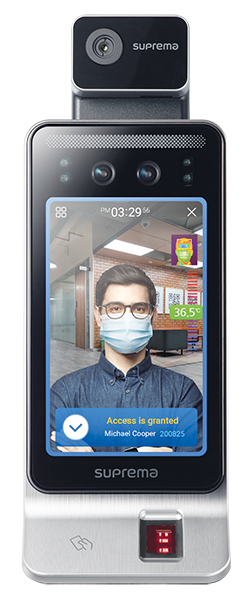
Rautenbach: Contactless options have always been available on Suprema’s access control terminals and devices. For example, our biometric fingerprint devices also offer RFID card and mobile credentials which make use of your mobile phone for access at the terminal. Facial recognition is also not new to Suprema and there are a few options to choose from, with the FaceStation F2 being the latest release. This terminal features walkthrough face recognition and offers remote enrolment for even less contact. Suprema also recently released a new RFID terminal X-Station 2, which adds QR codes to the mix of contactless options.

On the software side we have BioStar 2, Suprema’s web-based open, integrated security platform. It offers a plethora of features within access control, time and attendance management, visitor management and video log maintenance. One can say that BioStar 2 provides true contactless access control for both the system owner and user as no physical contact is required from registration all the way to using the particular credential for access. Contactless credentials such as face, mobile, card and QR code are entered into the system and shared with the user remotely for access, encouraging social distancing and eliminating the need for physical contact usually required in typical system processes.
When looking at controlling access to facilities like golf clubs, squash courts, conference centres etc., BioStar 2 can be used to effectively manage who is allowed access by pre-registering the details of expected guests and controlling the validity period of such access.
Hi-Tech Security Solutions How can this technology be integrated with other solutions to allow for individual verification (such as with Home Affairs or other government authorities) to allow the estate to know that contractors, for example, are who they claim to be?
Rautenbach: Suprema BioStar 2 software along with its hardware have several ways in which they can integrate with other systems. We have software development kits (SDK) and an API (application programming interface) available for integration to enable seamless exchange of information with third-party platforms. One thing to remember is that while access control systems generally opt not to store images, but rather only biometric templates as part of personal privacy and the irreversible nature of this method, Home Affairs utilises biometric images and not templates. With this it is always a question if one should look at storing the images for access control or not as there is PoPIA-compliance to be considered. One might say that for contractors we will store images and then try to explain to residents that their images would not be stored, but this is challenging at best.
What we have found worked best for this, supported through BioStar’s various integration layers, is to follow a separate route for contractors and those that need special clearance. This does not mean separate systems or disjointed data, but merely that contractors and parties that need to be cleared are enrolled through a separate channel which will have its own data type (like images, driving licence and ID document etc.) as well as a set retention period.

A subset of this data (biometric templates generated from images) can then be seamlessly sent to BioStar to enable access. At the same time, it is best practice to not retain sensitive and private images, biometric and financial clearance information and these can therefore be removed from the ‘clearance’ system while the access can continue to function for a stipulated time, until clearances need to be repeated, if at all.
We have seen very intuitive solutions implementing the above. Some solutions might want to use high speed equipment for data capture with dedicated workstations and others prefer to use some of our mobile BioRugged terminals, equipped with FBI-certified Suprema fingerprint readers to achieve the same on the fly. For BioStar, or any other enterprise access solution that uses Suprema readers, it can be implemented through a variety of integration methods.
Flax: At The Gate integrates with TransUnion enabling ID verification, vehicle verification and flagging vehicles involved in crime or reported as stolen. Our in-house research and development team are working on numerous future integrations with similar databases and parastatal organisations.
Garcia: We offer different levels of integration. By default, our solutions are designed for private access control/time and attendance and therefore we do not communicate with any external entities. However, our products can also be integrated with specific applications, allowing for integrations such as electronic visitor management, for instance. In this case, it is possible to check the identity of visitors or contractors within the respect of relevant legislations and regulations.
Hi-Tech Security Solutions: Are your solutions PoPIA-compliant? What do you do to ensure the security of personal information (fingerprints, facial templates, as well as the data that accompanies these, like names, ID numbers, cellphone numbers etc.)?
Garcia: Privacy and data protection are central to our solutions. Without trust from the user, no system can be used sustainably. Therefore, we made sure our solutions take these elements into consideration even before regulations came into play, from the early design stage of our terminals.
The first thing to note is that IDEMIA develops and provides solutions to manage the identity of users, but IDEMIA does not store nor has access to any of the users’ data. Everything remains under the control of the user. Secondly, the solution is designed to give full control to the system administrator. The data can be reviewed, modified and deleted while respecting relevant regulations and procedures such as PoPIA in South Africa or GDPR in Europe.
All our solutions also ensure that you only use the system when you deliberately intend to use it. When you use our MorphoWave terminal, you can only use the device if you wave your hand through it. For our VisionPass, we designed an ‘intention area’ which only triggers an identification if you are within a 70-centimetre ‘privacy bubble’ of the reader. It also has the ability to differentiate between two people coming close to the reader to open only to the right person.
Finally, all our solutions include end-to-end data encryption following state-of-the-art international methodology.
Rautenbach: Suprema products have advanced security measures in place to ensure the secure exchange of data with other systems and the protection of this data. Personal information entered into the hardware and server is encrypted while in storage and in transit. Raw fingerprint/face image data is never stored in the device or server and templates are stored as encrypted files. Suprema also safeguards against transaction, malware and data breaches through the use of TLS 1.2 (including SSL/HTTPS) to secure TCP communication and to ensure that no sensitive data is compromised during the communication between the devices and the central server. Trusted or self-managed certificates, based on industry standards, are used to achieve this. This default measure of security was implemented by Suprema before GDPR became the buzzword in protecting private information.
All Suprema devices are equipped with a secure tamper feature so that if a device is removed from the wall and tampered with, the secure data (biometric templates, user ID, logs) within the device will automatically be deleted.
The latest version of BioStar 2 allows system administrators to restrict access to personal data information according to their organisational requirements. BioStar 2 also delivers comprehensive audit logs. What’s more, it can be configured to automatically delete event logs and data stored in the server after a certain period of time. This is in line with the ‘right to be forgotten’ concept. For those who do not want personal data and credentials stored on servers or devices, Access-on-Card (AoC) technology is provided as an option so that users hold their credentials in their own possession on a smartcard.
It is important to note that encrypting data, although the default, is an option and that end-users need to ensure they are working with reliable installers and integrators to make use of this and that, as part of compliance, the end-user is the owner of the certificates used to ensure no one else has access to their data. It is easy to relax knowing your system is PoPIA-compliant, but end users should realise that data encryption is just one part of PoPIA and that other procedures, such as maintaining access to the system, removal of redundant employees and how system printouts and reports are maintained is something that remains a responsibility to be dealt with by the custodian.
Flax All of our solutions are PoPIA-compliant. They are, therefore, the first choice for numerous companies and establishments that need to improve their compliance.
As a start, all personally identifiable information is collected digitally, which already eliminates the risks of paper-based records that are vulnerable to prying eyes, theft or loss. Our devices encrypt all the electronic data and upload it to a secure cloud instantly. Device controllers cannot access the information once it has been captured, securing against breaches.
Each client (entity) holds a private cloud account for back-end access to their data records and analytics dashboard. Only authorised personnel (designated by the client) receive login credentials, where two-factor authentication is required. The client can also specify access levels. For example, operations team members can view dashboards and pull analytic reports, but only the security manager may access ‘on site now’ visitor details.
Hi-Tech Security Solutions: Can your solutions be integrated with third-party applications to create a complete solution (for example, recording entry and exit along with LPR to record the vehicle associated with the personal identity data), or even to track visitors in the estate?
Flax: Yes, our products were designed to work as a standalone solution or augment an existing solution to bolster security. A few solutions were even born out of collaboration with clients based on such requests. One such example being our ATG Cam, an IoT camera that compares the licence disc to the licence plate, flagging irregularities.
ATG Facial, on request, can integrate with payroll systems and has proven invaluable in time and attendance monitoring. We have several more examples, but what’s noteworthy is that we pride our products on customisation and innovation. If there’s a system with which customers want to integrate, our APIs and experienced development team can make it happen.
Rautenbach: Suprema makes integration easier through its development platforms for both hardware and software. The BioStar 2 device SDK and Suprema G-SDK allow developers to incorporate Suprema devices and terminals into third-party software. The BioStar 2 API, on the other hand, provides the tools for developers to create new applications that use Suprema devices and terminals or to integrate BioStar 2 into existing third-party systems such as visitor management, VMS, LPR etc.
An example of an existing integration is the iVisit visitor management solution, which integrates with BioStar 2 via the API. Residents are able to preschedule visits and share precleared access codes with their visitors, which, on arrival are entered into a Suprema reader for access. Our SA-based development and support team provide customisation services to clients requiring bespoke solutions as well as expert support to developers integrating Suprema into their solutions.
Garcia: This is actually one of our strengths. Identity should be the cornerstone of every solution. We use our 40+ year expertise in biometrics and identity management to ascertain the user identity and we pass this information to an access control system which ensures that all the relevant business rules are enforced for the user. This could be, for example, that for each user entering a parking lot the number plate of the vehicle is recorded and linked to the identity.
Hi-Tech Security Solutions: What visitor management features does your company offer, and/or what integration capabilities do you offer for companies producing visitor management solutions?
Rautenbach: Our visitor management system, iVisit, provides hosts with the ability to pre-schedule visits through a progressive web app. Hosts can then share a pre-cleared PIN with their visitors who then use this for access on arrival. It provides an easy and convenient way to process visits. For residential estates, residents and visitors share the same multifunction terminal where residents use the biometric function and visitors use one-time access PINs.
What we normally see, when it comes to visitor management companies, is a preference to integrate with software that already exists from the security product providers such as Suprema’s BioStar 2, which already has a fully-fledged access control module to manage access control requirements. This is because the platform encompasses all of the capabilities required to manage and use the hardware. An integration of this type is done using the BioStar 2 API. Through this method, the visitor management application is able to post visitor information back into BioStar 2, which is then transferred to the hardware to prepare it for the visit. The benefit here to the visitor management provider is that no development work is required to manage hardware as the application for this already exists and they will use the API only to exchange information with BioStar 2.
An alternative option when visitor management system providers want to have their system manage the biometric portion of the solution is to integrate with Suprema hardware through the device SDK. This means there is no other application between the hardware and the visitor management application and everything is done directly.
Flax: With the exception of On the Container, all of our products fall under the access control and visitor management banner. They are:
1. At The Gate is a gate access control system that provides positive visitor identification for corporate office parks, lifestyle estates, complexes and gated communities. Unique customisation capabilities include scanning accurate data directly from vehicle and drivers’ licences or ID card, capturing any custom data required (such as ‘reason for visit’ or ‘person visiting’), alerting hosts of the guest’s arrival or automating access for pre-authorised guests.
2. At Reception is a simple, self-service visitor sign-in solution. In tablet form, the system registers visitors, prints ID badges and announces guest arrivals with a few simple screen taps.
3. ATR Web is a visitor management system created in response to Covid-19. It is a touchless solution that allows a business to screen visitors for possible infections conveniently. More so, you can quickly alert all clients, employees and suppliers if a risk is detected.
4. ATG Facial is the ultimate access control and clock-in system. Here, advanced facial recognition technology enables touchless visitor, employee and contractor management.
Garcia: While we keep our focus on biometrics and identity management, we do offer some specific features, such as the possibility to read QR codes. The integration potential is limitless.
We team up with the best international and local access control specialists to offer the best solutions. In the current pandemic situation, for instance, a popular scenario is that for every person entering the building, the temperature must be checked and recorded. Of course, both MorphoWave and VisionPass terminals are also fully efficient with sanitary masks.
Another one is to allow visitors to pre-register, take a selfie with their smartphone and to use our VisionPass facial recognition device to be identified on the day of the visit, saving time and avoiding clogging of reception area.
Contactless face and palm recognition with temperature and mask detection
The SpeedFace-V5L Series from ZKTeco takes touchless biometrics to the next level by using advanced recognition algorithms and the latest computer vision technology to recognise faces, palms and fingerprints against a large capacity database at high speed.
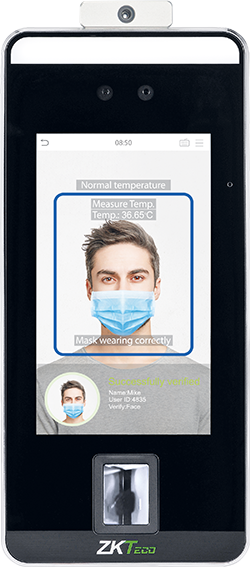
The SpeedFace-V5L [P] also has mask detection function built-in, while the SpeedFace-V5L [TD] adds a thermal detection module to read the user’s body temperature against an acceptable temperature range. These products are also equipped with anti-spoofing against almost all types of fake photo and video attacks. The 3-in-1 palm recognition (palm shape, palm print and palm vein) is performed in less than 0.4 seconds and the palm data acquired will be compared with a maximum of 3000 palm templates.
The system can also operate in an unsupervised mode when screening for body temperature and face masks. This means that any person accessing an area can be screened first to verify they have a mask on and then that they are within the prescribed temperature range. This all happens without an individual needing to be pre-enrolled on the system, so no recognition is needed.
This feature is aimed at public access areas like corporate buildings, schools, shopping centres, hospitals or any public area where temperature and mask screening needs to be done. The feature can also be used in conjunction with any access control barrier.
For more information contact ZKTeco (SA),
For more information contact:
• ATG Digital,
• IDEMIA,
• Suprema,
| Tel: | +27 11 601 5500 |
| Email: | [email protected] |
| www: | www.idemia.com |
| Articles: | More information and articles about IDEMIA |
| Tel: | +27 11 784 3952 |
| Email: | [email protected] |
| www: | www.suprema.co.za |
| Articles: | More information and articles about Suprema |
| Tel: | +27 11 543 5800 |
| Email: | [email protected] |
| www: | www.technews.co.za |
| Articles: | More information and articles about Technews Publishing |
| Tel: | +27 12 259 1047 |
| Email: | [email protected] |
| www: | www.zkteco.co.za |
| Articles: | More information and articles about ZKTeco |

© Technews Publishing (Pty) Ltd. | All Rights Reserved.