
Although IP video surveillance solutions are still often referred to as CCTV (Closed Circuit Television), analogue CCTV systems with a central matrix and video recorders with very large single points of failure are thankfully a thing of the past. The industry now expects all the benefits of what should be called an IP video surveillance solution.
These include much higher-definition cameras and advanced analytics; integration to access control, building management, fire, LPR and POS systems; remote monitoring and management to name just a few. IP video surveillance solutions typically have two distinctive surveillance architectures: centralised and distributed.
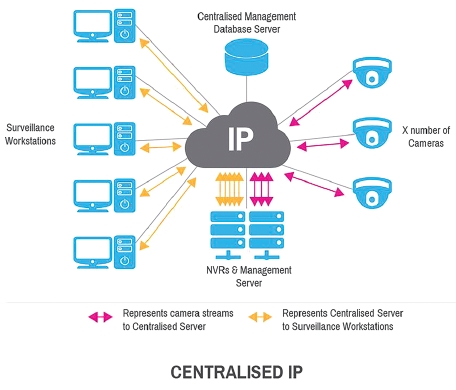
A centralised architecture operates with a central server and typically with centralised recording. All processing (including logins, viewing live and recorded footage, alarm notification, etc.) must be returned to the central server from any external site.
The advantages of a centralised architecture potentially include security, administrative overhead, less backup complexity and risk from outside interference. Centralised architectures potentially suffer from scalability problems, network outages and a single point of failure.
Certain measures can be taken to ensure there is no loss of video with centralised architecture (Centralised with Redundancy) but these measures can be expensive to implement and difficult to scale. These include installing a backup server, adding dual network cards and implementing secondary NVRs (NVR failover).
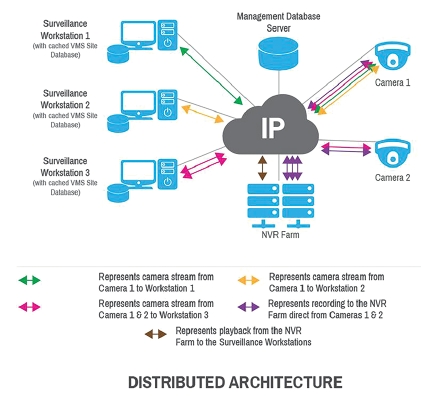
Distributed architecture isn’t solely reliant on a central server, allowing data to be kept close to where it is produced or needed. When cameras, surveillance workstations, NVRs, alarm servers, integration gateways all participate in a distributed architecture, data bottlenecks are minimised as all processing doesn’t need to pass through a centralised server. As there is no central server there is potentially no single point of failure. Advantages of a distributed architecture are reduced network traffic, scalability, increased reliability and resilience.
Different types of scaling
Vertical scaling occurs in a centralised architecture when resources are added to a central server in a system; this typically involves adding CPUs or RAM/storage.
Advantages of vertical scaling are easier implementation and administration; there’s a single server to manage, and that’s it. Setup is also straightforward and running costs (in terms of space, cooling and power) are lower.
Vertical scaling is often limited to the capacity of the central server. Scaling beyond that capacity often involves downtime and has an upper limit. Further disadvantages can be high hardware costs, as you have to purchase ‘high-end’ servers. There is limited scope for upgrades as a server can only be so big. What happens when your database can no longer fit on the largest available server?
Often there’s the issue of vendor lock-in or being locked-down to a proprietary solution. You can be tied to a single database vendor and if you decide to switch this could be a very difficult migration. Or worse, result in having to start again from scratch.
Horizontal scaling occurs in a distributed architecture and means adding more machines to a system; typically distributed or at the edge to deal with the increased workload.
An important advantage of horizontal scaling is that it can provide administrators with the ability to increase capacity on the fly. Another advantage is that, in theory, horizontal scaling is only limited by how many machines can be connected successfully.
Adding inexpensive machines to a distributed architecture might seem to be a cost-effective solution at first glance, but it’s important for the administrator to identify the setup and running costs. A disadvantage could be the licensing costs for additional servers.
Understanding the different surveillance architectures and implementing the correct architecture for your site will help address your immediate security challenges and facilitate your long-term operational goals.
| Tel: | +27 11 543 5800 |
| Email: | malckey@technews.co.za |
| www: | www.technews.co.za |
| Articles: | More information and articles about Technews Publishing |

© Technews Publishing (Pty) Ltd. | All Rights Reserved.