
With the number of high profile data breaches on the rise, users and organisations alike are more concerned than ever before with making sure that the sensitive information they handle remains secure. One of the simplest means of acquiring this information, for an attacker, is to enter an organisation with the key to the door itself, users’ passwords.

Authentication is the process of proving that you are who you claim to be. There are a number of digital methods that we use to prove that someone is indeed who they claim to be, but the most common form by far today is through using a secret piece of information, such as a password. This secret bit of information is intended to be something that only the user knows or has access to. However, all too often users choose something that not only isn’t secret to them, but something common that many other users will end up choosing too.
Organisations are responsible for protecting their users’ passwords in motion and at rest. At rest, it is important that the password is hashed using a strong hashing mechanism. Ashley Madison is an interesting case study, because despite their users choosing weak passwords, they had attempted to protect the password with a strong hashing algorithm, bcrypt. It was not until the research group CynoSurePrime discovered a weakness in the way that the developers had stored an alternative version of this password that they were able to crack a significant number of the passwords.
Strong passwords
In order for organisations to better protect themselves against password attacks, as well as implementing two-factor authentication, a strong password policy needs to be implemented. In addition to research being done around compromises like Ashley Madison, MWR have seen a spate of large breaches that began with a password compromise. The iCloud celebrity breaches rose out of a vulnerability discovered in a mobile API that did not limit the number of login attempts an attacker could make. Accounts that were not protected by strong passwords could be guessed by an attacker by exploiting this vulnerability.
The JP Morgan Chase breach is another compromise that was widely reported on, and began with an attack that guessed a single weak password in 2014 (https://securityledger.com/2014/10/hacked_password_behind_compromise_of_75m_jpmorgan_accounts/).
Password guidelines
The CPNI and CESG in the UK have recently released a helpful set of guidelines on how organisations and users can better choose passwords (https://www.gov.uk/government/publications/password-policy-simplifying-your-approach). Traditional wisdom has often said that the more complex a password is, the better. This wisdom has slowly been replaced with experience and practicality, as users have struggled to remember highly complex passwords and resorted to using predictable patterns to choose them.
These patterns, such as capitilising the first character of the password and adding a digit and special character to the end of the password, make the password much easier to guess for an attacker. Instead, long passphrases are now considered generally more secure and can be easier for a user to remember. The passphrase, “Today I walked my dog” is significantly more secure than 'P@$$wORD_1' and easier for users to remember, and organisations should consider choosing length over complexity when they think about password policies.
MWR has spent several years conducting research into how to attack the mind-set of users when they choose passwords. Most recently, MWR collaborated with Carnegie Mellon University in the U.S., where it came out on top in a comparison of attacks against user passwords where they competed against another security firm and independent researchers (https://www.usenix.org/system/files/conference/usenixsecurity15/sec15-paper-ur.pdf).
Perhaps the single biggest take away from the breaches that we’ve seen recently, is that users have not learnt from others’ mistakes. We’re still seeing the same, weak, easily guessed passwords being used across accounts on the Internet. Furthermore, the second lesson for organisations, is that storing passwords securely makes a significant difference in protecting its users. Storing passwords with a strong algorithm such as bcrypt, goes a long way in protecting users in the event of a compromise.
Password shenanigans
By Andrew Seldon
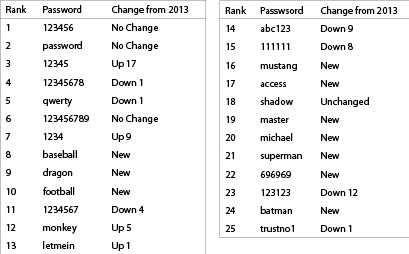
Strong passwords are not the most difficult to remember. Edward Snowden suggests “MargaretThatcheris110%SEXY” would be a good password. Sadly, few of us pay attention to good advice. SplashData published a list of the most commonly used passwords on the Internet in 2014, proving once again that careless users are your most dangerous threat.
SplashData’s “Worst Passwords of 2014” list includes the following:
The UK government has also jumped on the password bandwagon and has published Password Guidance information. The information is available at www.gov.uk/government/publications/password-policy-simplifying-your-approach (short URL: http://goo.gl/T21vuf).
An infographic summarising its advice can be seen in the diagram, and downloaded from https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/458858/Password_guidance_-_infographic.pdf (short URL: https://goo.gl/RRM7CI).
The information is freely available, licensed under the Open Government Licence v3.0. More information on this licence and its terms can be found at www.nationalarchives.gov.uk/doc/open-government-licence/version/3/ (short URL: http://goo.gl/rB82pX).
For more information contact MWR South Africa, +27 (0)10 100 3159, harry.grobbelaar@mwrinfosecurity.com, www.mwrinfosecurity.com

© Technews Publishing (Pty) Ltd. | All Rights Reserved.