

When it comes to financial services companies, dealing with risk is naturally a critical aspect of their daily business. As regulations worldwide have tightened control over financial institutions, compliance with these rules and the newer privacy laws also place a major burden on these companies.
In addition to that, the information risks these organisations need to deal with are also immense and create the biggest headache for these companies daily. While compliance regulations change, they do not change overnight, allowing financial organisations to adapt as required. However, information risk, a larger risk category that includes cyber risk is something that changes rapidly as threat actors, both internal and external, continually update their methods of attack.
Apart from the obvious cybersecurity risks they face in terms of lost money, reputation and so forth, a cyber breach could also affect their compliance standing and attract the attention of regulators, for example, if private information of clients is lost.
Craig Rosewarne, MD of Wolfpack Information Risk spoke to Hi-Tech Security Solutions about the complex labyrinth these companies need to navigate to ensure compliance and mitigate their information risk.
What are you protecting?
When looking at an organisation with the aim of implementing an information risk management programme, Rosewarne advises the company to look at various components of its business, starting with its assets that need protection, which can include access control to physical buildings as well as information stores. In today’s connected world, IT assets could arguably be assigned more importance than physical assets, although in other industries such as manufacturing, operational technology (OT) would be as important.
Once one has insight into the assets that need protecting, they need to identify the threats they face and the ‘threat actors’ that want to get hold of those assets. These threat actors will look to exploit any vulnerabilities in the business environment, both physical and digital, to achieve their goals and this will naturally have an impact on the business.
Understanding the business impact does not only include tangible assets, but also intangible ones such as intellectual property, brand and reputation, as well as strategic plans. Moreover, organisations will also need to include their strategic stakeholders and customers in this exercise.
To prevent this impact, organisations need to focus on designing risk mitigation controls that will reduce the vulnerabilities or act to protect the business when someone tries to exploit them.
Rosewarne adds that simply buying hardware and software to protect your information assets is not a solution in itself. An organisation can only know what security systems or solutions are needed once they understand what they are trying to protect and who their adversaries are and how they may compromise the business.
Information risk framework
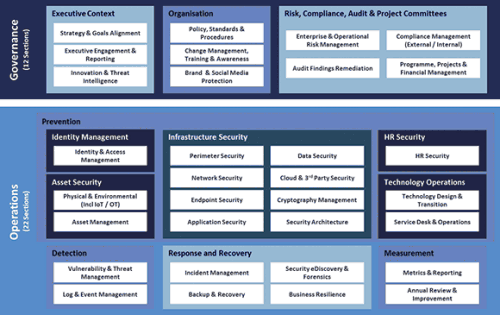
Wolfpack has designed an information risk framework to assist clients in understanding the above, dividing it into two areas: governance and operations. Figure 1 shows the basic framework from which organisations can begin a phased approach to understanding and mitigating risks.
As can be seen, it covers the entire organisation and its operations, from HR to IT to physical security and more. It also includes business resilience in which the company has plans in place to deal with the unexpected, which could mean anything from a fire to a riot or a ransomware attack.
Each of the components of the framework need to be addressed and assigned a priority in terms of the urgency with which they need to be addressed (Figure 2 provides an example of what the prioritisation might look like). In addition, a gap analysis must also be conducted to determine where the company is in its risk mitigation efforts for each component.
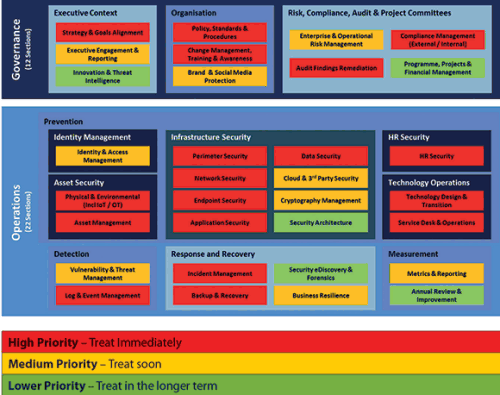
This will enable management to prioritise their requirements and address their risk profile in a phased approach, making sure they have the right tools, systems and people in place to keep the business engine running.
Another key area of risk management is third-party compliance. Financial organisations make use of a variety of partners in their business operations and they need to be sure that these partners are also serious about risk management and information security. A bank, for example, will need to have policies and processes in place that its partners and suppliers must adhere to in order to prevent the bank from being compromised via a company they trust.
More than simply having a policy for information security, they need to ensure that their partners comply by testing their defences to provide everyone involved with peace of mind.
When implementing solutions to the information risk component specifically, there are a number of tools available on the market. Unfortunately, at this stage, there is no single tool that can do it all and although efforts are underway to create dashboards that integrate multiple products into a ‘single pane of glass’, there is no platform that can handle all the components of information risk a financial organisation will need.
As noted above, before one even thinks about products and solutions, expert insight and advice is required to understand the company’s security or risk posture and what needs to be done to mitigate the threats most pertinent to the organisation.
Alert Africa

Alert Africa was established in 2015 to raise awareness of cyber threats, provide victim assistance and unite the cybersecurity community. The site offers a range of services, from education to the ability to report cybercrimes, as well as victim assistance for those who find themselves caught in a cyber trap.
The site is designed to make cybersecurity understandable for everyone and addresses issues in a non-technical and non-threatening manner. The site also caters for businesses with a jobs portal as well as a business directory of companies operating in the cybersecurity space.
Find out more at www.alertafrica.com or watch a 1-minute introduction video at www.youtube.com/watch?v=kYvuUkRiejQ
| Tel: | +27 11 794 7322 |
| Email: | info@wolfpackrisk.com |
| www: | www.wolfpackrisk.com |
| Articles: | More information and articles about Wolfpack Information Risk |

© Technews Publishing (Pty) Ltd. | All Rights Reserved.