
A Johannesburg company is taking a radical new approach to identity. Lynne Larsen discovered more about the innovative thinking and its practical applications.
With one product already in the market and others set for rollout in the coming months, BioDentity focuses on how identity can be used to accelerate business processes and heighten security in a broad range of commercial activities and environments.
A new concept of identity
Everyday, so much of what we do is identity-related. From credit card payments to entering our workplace, we live in an environment that regularly requires us to prove that we are who we say we are. We carry drivers licences and ID documents with us nearly every time we leave home. We have PINs and passwords for everything from our phones to our bank accounts and computers. We use our identity to safeguard our possessions and to protect them from misuse by others.
However, there are apparently far wider uses for identity. Mark Eardley of BioDentity says, “Identity is frequently used to confirm the validity and integrity of our activities. But our identity relates not only to who we are, it also extends to what we are. For example, our age is a component of our identity. We need to prove our age in order to establish the legitimacy of our behaviour, such as getting married; driving a car; buying alcohol; voting; and claiming pensions or other civil benefits.”
Other components of identity include information relating to authorisations and accreditations. There are many instances where we must be authorised or licensed to perform our work – ranging from nurses and lawyers to machine operators and airline pilots.
Residence is yet another core component of identity. In its broadest sense it defines nationality and citizenship, but also relates to local and national taxation as well as determining requirements for passports, visas and even inoculations. In many countries, residential postcodes are used to profile people by identifying their spending power and preferences. Eardley says he recently entered his old London code on a site called www.upmystreet.com and was amazed by the extent and accuracy of the information relating to the street’s typical residents. Using more than 250 pieces of information from the Census and various market research and lifestyle databases, details include demographics; property type and ownership status; car ownership; typical incomes and the likely popularity of financial products; the most popular newspapers plus general information about holidays and entertainment preferences.
The four dimensions of identity: PLAT
BioDentity separates identity-data into what the company refers to as PLAT: person, location, activity and time.
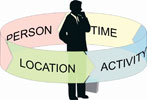
Data relating to a person includes information such as name, age and gender. PLAT methodology then links this data with information relating to a person’s activities and makes still further associations according to location and time.
The methodology around PLAT builds a complete identity based on more than just a name, address, ID number and contact details. PLAT does this so that a person’s identity becomes increasingly distinctive and can be confirmed more accurately and rapidly.
PLAT builds identities by drawing information from a variety of sources. As more data is added, PLAT-based systems build an increasingly detailed composite of the person’s identity. The accuracy of the composite continues to grow with the addition of each identity-based activity, the time it occurred and the location.
Eardley compares the approach to, who, where, what and when. You can analyse a credit card transaction in these terms: who is using the card and where are they using it? What are they using it for and when are they using it? A PLAT system would compile information that not only relates to the identity of the person and the nature of the transaction - the activity, but could also flag anomalous behaviour. If you live in Johannesburg and conduct the majority of your transactions in Gauteng between 0900 and 2300, it would be unusual to see a transaction taking place at 0130 in Dubai – particularly if there was a Gauteng-based transaction only a few hours earlier.”
Layers of identity
PLAT methodology builds layers of information to form an iometric identity. Eardley refers to the process as ‘accretion’ – as layers of data are laid down over time. As data accretes, so the identity becomes more complete and more easily recognised.
Eardley cites the following as exemplifying the process of accretion, “Your date of birth is not unique and does not identify you. However, if you begin accreting information to that date, the identity starts to grow and becomes more distinct. So, we add your gender and your surname, then your first names, then the location of birth.”
By this point the identity has become quite distinct from the vast majority of those people who share your birth date: many John Smiths may have been born on the same day, but not all in the same place at the same time. The distinction can be further enhanced by accreting residential data and a social security or ID number.
Iometrics: a new methodology, not a new technology
In essence, it is this philosophy of multicomponent identities that drives the methodology behind what Eardley terms ‘iometric solutions’. He says, “The premise that identity has several interrelated or associated components is a fundamental principle in our approach to identity. Without association there can be no recognition. We therefore look at ways in which we can build easily-recognised, accurate identities by associating or linking different types of identity-related data. This allows us to use identity in order to accelerate processes and increase their integrity. Iometrics is the term we use to refer to the entire process of building and using identity information.”
The importance of association becomes clearer in the relationship Eardley sees between biometrics (see sidebar) and identity. He does not see biometrics as being the foundation on which to build identity solutions. Rather, he suggests that, “On its own, a physical or biometric characteristic has no value in terms of recognising a person. The physical characteristic has to be linked to other information: it has to be associated before it has relevance. This fact increases the importance of other, more established, means of recognising or identifying a person such as their name or even what they look like. You might not know Hugh Grant, but could probably recognise him from his appearance if you were ever to meet him.”
Before biometric data can be associated or linked to a person, it is essential to establish who that person really is. Eardley sees this as being the critical first step in creating an iometric identity and one which is often skipped over in identity-based solutions. “You first need to establish who the person is before you can begin adding other identity-related information. We think it is important to cross-reference data from a number of sources in order to achieve a positive identification. Within PLAT we have a number of procedures to achieve this quickly and accurately.”
According to Eardley, clearer recognition creates greater speed and security: “The more clearly we can recognise an individual, the faster and more securely we can interact with them. In terms of identity, speed and security are consequences of recognition.”
Public, personal, private and protected: the iometric protocols
In iometric solutions, any type of data can be categorised as either public, personal, private or protected – whether or not it is identity-related. The protocols are rules that typically govern data acquisition, storage and dissemination.
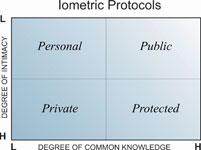
Having categorised data in this way, access to it can be managed according to PLAT – who has access, what can be accessed, when and where. The methodology can be illustrated in the following way:
A company’s e-zine can be opened and read by all 1000 employees, but it can only be:
* Created and edited by Jon on his PC.
* Approved for distribution by Pat.
* Mailed by Jill from her PC after 11:00 on the first Tuesday of the month.
In this example, the e-zine’s content would be categorised as public, while its creation, approval and distribution are protected.
The next example demonstrates how the protocols of private and protected might be applied:
The company’s strategic plan for mergers and acquisitions is available to just eight employees and can only be:
* Created and edited by the CFO.
* Approved for circulation by the CEO.
* Mailed by the CIO from his PC in read-only format during normal working hours.
Confronting Big Brother
George Orwell’s Big Brother would have been appalled by the idea of the protocols because they are used to differentiate and reinforce the importance of the individual. From talking to Eardley, it is apparent that emphasis is placed on the human aspects of identity and that the company’s approach is rooted in these values rather than those of technology and the sinister associations we often make between identity and being watched and being controlled.
“Treating people as individuals is right at the core of our thinking. We believe that recognition is key to interaction and it dictates how we respond to one another in society. How we respond depends on our levels of recognition – the extent to which we know one another. This opens up new opportunities in terms of how we handle identity as a means to improve our commercial interactions and relationships.”
Working with identity: iometrics in action
As an example of how iometric methodology translates into solutions, Eardley says, “Imagine you have many thousands of customers to whom you provide a number of similar services. Managing the relationships with those customers will be an important element of your business and you will have a more or less formalised process in place to perform that function.
“An iometric solution will allow you to differentiate amongst those customers quickly and accurately and allow you to interact with recognised individuals. You can accelerate your response because you know exactly who you are dealing with. This is where we see biometrics playing its role in identity solutions – as accelerated identifiers.”
Eardley considers BioDentity’s strengths to lie in its abilities to formulate solutions that address specific challenges concerning identity, and that are commercially viable and operationally feasible.
BioDentity’s first product addresses a challenge faced by all access systems: how to securely control access for visitors to business premises and residential estates. “We saw a big loophole in how traditional systems deal with visitors. We close this loophole by running an automated identity check on the visitor and capturing a fingerprint ‘signature’. Having your identity confirmed and details registered electronically is not an attractive prospect for the criminally-minded.”
Eardley sees the product as a good example of how the company works with identity, “We look at combining different technologies to produce effective identity solutions. In this instance, we use a combination of fingerprint biometrics; identity-data sources; GPRS and database management technologies.
“The converged result is an identity-based crime deterrent.”
Looking beyond physical access control, the company is working in other areas where it sees a need for securely managing large volumes of identity-based activities. The company is developing two iometric solutions that can be applied in this arena: Cesso and Certica.
Cesso (certified enterprise single sign-on), is intended as a platform for network access control. It applies iometric principles for managing access to devices, data, applications and networks – DANs in iometric-speak.
Certica (certified identity chain architecture) is, in its most simplistic from, a process that positively confirms who did what, when and where. Beyond network access control, Certica has a widely diverse range of applications, from a multitude of business processes to our everyday monetary activities to. Eardley reckons, “In the field of financial transactions alone, there are enormous opportunities and advantages in replacing PINs and signatures with competent biometrics within an iometric solution.”
Identity chains
Integral to both Cesso and Certica are identity chains – sequential activities that are recorded according to PLAT. For example, in the world of logistics, identity chains can be used to track the progression of goods from port-to-shelf: collection, warehousing, batching, delivery, receiving and shelving.
If each person in the chain is assigned an iometric identity, then each activity can be signed-off on handheld biometric terminals.
Identity chains create the platform to leverage the functionality presented by Certica systems, such as highly accurate auditing, monitoring and reporting tools.
The human benefits of iometrics: being positive about identity
Rather than thinking of iometrics as one small step towards being watched by Big Brother, Eardley stresses that iometrics is a giant leap towards enabling positive use of identity.
A great deal of our identity data is already public knowledge. “Unless we choose to be ex-directory, the Johannesburg phonebook alone lists thousands of our names, addresses and telephone numbers,” says Eardley.
In South Africa any of us can use the Home Affairs service that links an ID number to a name. We can also check on one another’s credit ratings through a number of commercial services. The popularity of social websites like Facebook has led to millions of people volunteering their identity data to a greater or lesser extent, and there have been many recent calls for users to be much more cautious about what they divulge and to whom.
The whole issue of identity theft and subsequent fraud is a significant and growing problem throughout the world. Consequently, it is increasingly important for all of us to protect our identities.
By its very nature, iometrics creates identities that are easily recognised and unique. Because they are so distinctive they are difficult to replicate or abuse. Eardley cites the following as being examples of how we can all benefit from developing and encouraging iometric identities.
* Deterrent to identity crime and the associated human negatives that range from stressful inconvenience to potentially lethal.
* Reduces victimisation from financial fraud and other illegal uses of your identity.
* Faster ID-related processes and faster customer recognition.
* Increased convenience of fast track identification processes at ATMs, tellers, payment authentications and credit transactions.
* Account opening and contract authentication.
* Transaction authentication – ranging widely from using your credit card or medical aid, to operational safety checks on aircraft.
How big is identity crime?
A recent article in the UK’s Independent newspaper reported that e-mail passwords and bank account details are being sold on the online black market for up to £200 a time. According to a study by Symantec, bank account details fetch between £15 and £198, while e-mail passwords are sold for as much as £173 or as little as 50p. Criminals are earning up to £4500 a week selling personal data to other criminal gangs, using sophisticated pieces of software to ‘phish’ for the information.
Closer to home, a case study released on the Unisys website in June 2007 states that South Africa’s government and private sector each lose approximately US $200 million annually (a total of R1,4 billion) through health and welfare, credit card and check fraud stemming from false IDs.
In the UK, the Home Office Identity Fraud Steering Committee’s latest estimate is that identity fraud costs the economy £1,7 billion a year. (R24 billion) For an in depth examination of how the problem is increasingly affecting the UK, www.identity-theft.org.uk is well worth visiting.
Who uses visitor management systems?
Electronic visitor management is gaining wide acceptance as an essential part of physical security infrastructure. Visitor management is being adopted across the board in many industries including: pharmaceutical and healthcare facilities, food supply chain, technology R&D centres and manufacturing sites, media and communication companies, government agencies, defence contractors, chemical production sites, utilities, finance and insurance corporate offices and many more. All have a common need to gain better visibility of their visitor traffic through consistent registration and visitor policy enforcement procedures.
In many facilities, despite significant investment in physical security, tracking of visitors is still a manual process in most cases. The registration of visitors in a paper logbook and issuing non-descript visitor tags is often the cause of lobby inefficiencies and is a source of potential security exposures.
The visitor logbook is often inaccurate and incomplete. It does not consistently include the host’s name, visit location or sign-out time and therefore cannot be reliably used in cases of emergencies and forensic investigations. The problem is drastically compounded for facilities with multiple entrances and with separate logs for different types of visitors. In addition, the visitor tags issued to visitors can be easily abused by impostors.
Most of all, this manual process is recognised by many companies as a missed opportunity to collect detailed and accurate information about visitors, encourage visitor pre-registration, consistently check for barred visitors, enforce mandatory visitor sign out policy and proactively track visitors while on site.
For details contact Honeywell Systems Group
Biometrics in iometrics
BioDentity strongly advocates the use of biometrics in iometrics. Eardley says, “We believe that we understand the power of biometrics and that we have chosen the right biometric technology to enhance our solutions – a major component of our management system is the Sagem MT2G mobile terminal.
“We think fingerprints will continue to be the dominant form of biometrics, and that Sagem provides the dominant technology. This is particularly true in South Africa where the big biometrically-enabled civil systems – like the Police and Home Affairs – employ Sagem technology, and because Sagem is by far the leading biometric technology being used for access control.”
Whole new meanings in the world of identity
Iometrics
The methodology of using measurable and certifiable identity-data to accelerate business processes and increase their inherent security.
Accelerated identifiers
Any means that increases the speed and security of identification in iometric-based transactions, eg competent biometrics to authorise an electronic financial transaction.
PLAT
Person, location, activity and time. The methodology for categorising identity-data according its dimension.
Accretion
The process within PLAT whereby layers of data are added to an identity.
Identity chains
Sequential activities that are each related to an iometric identitiy.
Iometric protocols
The rules that typically govern the acquisition, storage and dissemination of iometric data.
DANs
Devices, data, applications and networks.
Cesso
Certified enterprise single sign-on.
Certica
Certified identity chain architecture.
For more information contact BioDentity, +27 (0)11 234 0868, [email protected], www.biodentity.co.za

© Technews Publishing (Pty) Ltd. | All Rights Reserved.