
The logical transition from today’s typical client/server architecture to third-generation network appliances.
The need for remote access
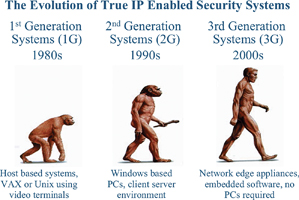
Eighteen months ago, when I was representing a company that was manufacturing and selling a security system based on the typical client/server architecture, I would regularly present product overviews and demonstrations. Although the audiences were generally pleased with the system features, I was continuously confronted by questions from the audience regarding remote access. I was regularly asked "can my authorised security personnel access this system via the Internet in order to evaluate activations remotely?" This was a requirement that would allow them to make informed decisions, based upon this remote access, before taking any remedial actions and so they could decide if a trip to a facility was required or not, which in turn saves time and money. Of course, as these systems employed applications running on a server and were not services running on a network, remote access was difficult and expensive. Systems utilising client server architecture are known as second-generation systems. First-generation systems were host-based and required large machines (hosts) that were accessed by the user via 'dumb' terminals, these were terminals with black screens presenting text only in either yellow or green writing. These have all but disappeared now.
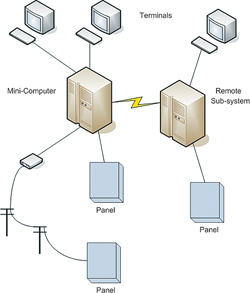
To access a client/server system remotely involves providing setting up virtual private networks (VPNs) for secure access and purchasing and installing the manufacturer's client software on a client workstation. Client software needed to be loaded onto each remote client PC requiring access to the server application so this meant increased expenditure and IT involvement plus an additional limitation in that an operator could only log into their system from a dedicated PC, with client software installed and not any PC.
The more enlightened manufacturers started to employ third party software to enable access to the server via the Internet, however these had limitations. These applications effectively captured the application screen from the on-site PC and transmitted this via the Web thus making the system very slow, additionally full access to the system resources may not be available when using such programs so this provides only a partial solution. These solutions are generally dedicated to monitoring functions rather than setup and other administrative functions.
The latest hybrid systems that are emerging, to try to bridge the gap between client/server and third-generation systems, utilise the Microsoft .Net framework. Although this is better than the previous solution it is still a 'half-way house'. Although a system utilising the .Net framework is web-enabled it is not browser delivered and will still deploy client/server architecture in the background with all of its inherent unreliability thus increasing the overall cost of ownership.
The second-generation system ownership conundrum
Remote access was not the only issue driving the industry to look for new technology solutions, higher reliability and lower cost of ownership were vital considerations.
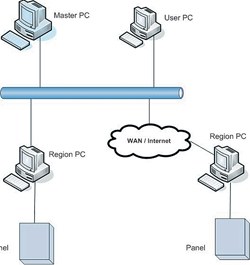
Owning and running a typical client/server security application utilising the popular Microsoft Operating Systems requires considerable effort to support the system. Firstly, the system hardware (PC) has a very low MTBF (mean time between failure) estimated at two years. This is due to several factors, the most significant of which are moving parts within the PC such as hard disk drives, CD drives and fans. Coincidentally, those parts also generate the most heat, and heat is the enemy of longevity in electronics. Most security system servers are not located in a server room with ideal conditions but are mounted within the security control room. The PC has an aperture within the front panel of the machine, ie the floppy disk drive, it also has a fan on the back panel. Dirty air is drawn though the PC thus depositing dust on the internal PC components which, after a period of time, will hinder the fan from operating. At this point internal PC components will overheat and will eventually fail.
This will require replacement PC components or even a new PC itself. If the hard disk drive needs replacing or a new PC is required it will probably require a day's labour for a technician to load the operating system, applying the latest service packs and security patches then add the application software. This is assuming that the customer has backed up his security system thus allowing for the restoration of the database and transaction history. If they have not, then all data will have to be manually re-entered, which will add considerably to the rebuild time and thus the downtime.
As the system is down during this rebuild time, it means that security reporting functions are compromised.
There are several common strategies employed to reduce enterprise system failures. Redundant computers, in which a failed computer's functions are taken over by a second, 'hot standby' computer, are a common method used in first- and second-generation systems. Fault tolerant computers, which contain multiple CPUs, memories, disks, and so on, have also been used, but they are quite expensive.
The above assumes a physical failure of the PC; however, equally concerning is the obsolescence of the PC and its component parts itself. The life cycles of PCs and their internal components are in the region of 18 months, similarly manufacturers and operating system suppliers are continuously upgrading their software to provide greater functionality. There comes a point where a customer will have to upgrade the PC server and client workstations to benefit from any new functionality that an upgrade will provide merely because their existing PC hardware will not support new components, operating systems or application software.
Any of us that use the most popular PC operating systems are now used to continuously downloading and installing patches to increase functionality, reduce the risk of security breaches and fix known bugs. Some of us set our systems to do this automatically in the background and others do this manually. Although most patches will not require a reboot, many will. This presents problems for PCs on a security system for the following reasons. Security PCs are not generally connected to the Internet so they are not updated automatically and are therefore vulnerable to the flaws that the patches would fix. Even if they were connected to the Internet and set to automatically download and upgrade, consider the implication of the PCs automatically rebooting, therefore loosing security monitoring for the duration of the reboot. Once patches have been installed they could conflict with the manufacturer's software and so cause operational problems. Most manufacturers now provide a secure link on their websites where dealers can log in and determine if a patch has been tested and approved.
This relies on a technician logging into the website regularly and if a patch has been approved, then going to each of his customer sites and downloading and installing the patches. This is a daunting task if a company has 20 customers, however most installation companies could not survive in business with only 20 customers. The result is that most installation companies do not follow the preferred patch regime of the operating system producers thus their systems are therefore vulnerable and compromised.
Forrester Research did some analysis on security systems and identified that the average lifespan of the typical security system was 11,5 years. Given the MTBF of PCs and short life cycles of PCs and their peripherals, it can be seen that the PC will need to be replaced several times during the operational life of the system even if it is not due to failure. After all, if we look at a 10-year-old PC, we are looking at a PC that was supplied in 1996 so it would not even be running Windows 98 which has long since become obsolete and is no longer supported by the manufacturer.
The third-generation solution
For the above reasons, a third generation of architecture is making its way out of the IT and telecommunications world and into the physical security industry: thin client, web-based network appliances. As the name implies, third generation systems are thin client systems, using web browsers to deliver their user interfaces. ('Thinness' refers to the lack of need for specially installed - or fat - client software), this is also known as zero footprint software. All of their components are network-connected, and integration among multiple systems occurs over the network that connects them. They are called appliances because they are special purpose computers with embedded software that handles a particular application.
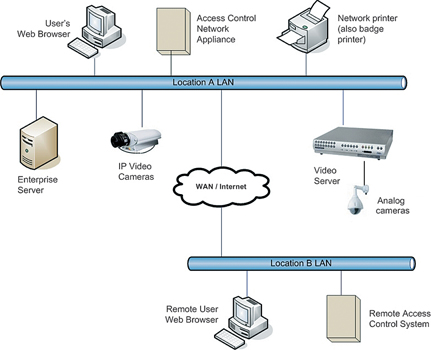
A network edge appliance is a native IP device that processes data and applies business rules at the point it touches the network (network edge), rather than at a central PC server. The operating system required to run the system, the database required to store the data, the application required to apply the business rules and the web server required to deliver the data to the operator in an intuitive user friendly format are all embedded within the appliance. Zero footprint software means that no software has to be loaded onto a PC in order to access the system via a web browser. Within the security industry we have seen this type of technology within IP cameras, to access the camera to set up parameters and view its images, one simply logs onto the camera's web server via a browser. The cameras are at the network edge and the user experience is via a browser. We are seeing more and more acceptance of this technology in the CCTV sector, even though there were many original sceptics originally, now we are starting to see the same in the integrated solutions marketplace.
Therefore, when a third-generation appliance is purchased it comes with no software to install, all of this laborious work has been completed by the manufacturer and so the device is ready to go out of the box.
As a network edge appliance incorporates a web server it means that the system can be accessed from any computer, running any operating system, using any browser from anywhere in the world where Internet/intranet is available. Therefore the users with the correct access privileges can log onto the system, not only from home but from any computer with a browser and with access to the Internet. This could be from a hot spot in an airport lounge for example and as the system has zero footprint software it need not be from their own laptop but any Internet connected terminal within the lounge.
A third-generation product does not include any moving parts, therefore as a solid state device it has a much longer MTBF, in fact it will have been designed to last the life of the system and not the life of the weakest point of failure, the PC.
Their native IP hardware technology ensures simplicity of installation, high speed networking and inherently better data security. The utilisation of SSL between the browser and the solid state server replacement known as a network controller (NC) and SHA-1 MAC Authentication between the NC and the Intelligent Field Devices (NN) add a level of security not seen in second-generation systems that generally utilise RS485 and 'Telnet Converters'). Utilisation of the DHCP protocol for dynamically addressing computers on a network enables a third-generation system to automatically detect and address intelligent field devices (network nodes) within the system.
The third-generation approach to adding complexity places web-based network appliances from multiple manufacturers on the same network. Each is responsible for its own application and communicates with related appliances by means of an application programming interface, or API. The most current APIs are based on XML, an IT standard for complex data communications. This addresses the 'C' word that we hear on a daily basis, ie convergence. Convergence provides the interoperability of disparate systems using a common backbone (network) and is what end-users are demanding in order to reduce their running costs and maximise their return on investment (ROI) in network infrastructure.
There are network appliances out there that provide multiple authentication methods, beyond mere usernames and password, to access corporate resources such as the network, the e-mail system, the CRM system etc. By utilising an XML-based API it is possible to use a persons location as an additional authentication method, thus it is possible to ensure that unless a person presents their access card to a card reader on the front door of a building they cannot gain access to the corporate resources
The legacy problem
So, now you are sold on the idea of scalable, reliable and flexible third-generation systems, but what about the systems you currently have? While the lack of standards in our industry hampers easy replacement of legacy systems, there are options. In the access control world, many card readers support the Byzantine but popular Wiegand data interface, and will connect to new, third-generation devices. The more advanced card access solutions easily support existing card formats so that credentials will not have to be exchanged. In addition, electric locking hardware and alarm points are generally compatible across systems, so these can remain.
In the final analysis, third-generation systems are still young but growing rapidly. They offer the advantages of lower lifetime cost of ownership, scalability, and ease of deployment. And, there are often relatively easy migration paths away from older equipment. Check out network appliance-based systems at the next trade show you go to.
For more information contact S2 Security Corporation, +44 (0) 1483 852181, [email protected]

© Technews Publishing (Pty) Ltd. | All Rights Reserved.