
In the alphabet soup of acronyms that surround the world of IP communications, there is one that is potentially more important than all of the others: TCO. It stands for total cost of ownership, and it is the real motive behind the drive toward converged IT and security systems, IP networks and digital video. A lot has been written about how to analyse and set up the technology of a network, but the business case - and TCO is a big part of that - needs equal attention.
The thinking behind the business analysis is straightforward. The total cost of ownership can be written as an equation:
TCO = cost to buy + cost to install + cost to operate + cost to maintain.
For most commercial purchases, the primary factor is the cost to buy. Thinking about the purchase price typically dominates decision-making because budget cycles usually look ahead only one year. When it comes to security systems, the cost to install and cost to operate have traditionally been similar from system to system, and so, apart from discussions centred on labour rates, have not offered much opportunity for savings. Cost to maintain is often calculated as a fixed percentage of the purchase price frequently included for the first year, and so can be easily overlooked.
It is little wonder, then, that the initial purchase price of system components has been so important. In the networked world, though, the terms of the equation change significantly. It is still true that budget cycles run on year boundaries, and that the cost to acquire equipment is thus important, but the installers and end users now have choices when it comes to the other terms in the TCO equation.
Breaking down the costs
The cost of installation is probably the easiest term to understand because it seems intuitive that pulling less wire ought to cost less. Add to that the fact that the cost of installation is usually incurred in the same budget cycle as the system purchase, and the case for network cabling appears to be compelling. But is this really where the savings come from? Working in favour of network cabling is the fact that multiple devices can share connections, but working against it is the fact that the more points of connection there are, the more network equipment is needed.
Certainly network cabling can be less expensive than proprietary twisted pair wiring, but the real value is in the two terms that are so often overlooked: operating cost and maintenance cost. IP networks influence operating cost by making it unnecessary for a system to be operated from the facility in which it is installed. Breaking the bonds of geography this way adds tremendous value by permitting multiple facilities to be monitored from a single location and allowing users to administer their systems from remote offices or even their homes.
But the biggest positive factor in the total cost of ownership improvement seen in networked systems is in their maintenance. We are used to computer systems that have replacement cycles of three to four years. Forrester Research, an organisation that surveys IT trends, estimates that in corporate settings, PCs are replaced about that often. Security systems, however, have much longer lives, typically from 10 to 12 years or more. That means that they spend the vast majority of their lives in the maintenance phase - and the situation is even more pronounced when you consider all of the other equipment beyond the PC. It begs the question: which costs more, the acquisition of a security system or its maintenance?
Forrester estimates that a typical corporate PC costs $120 to $150 per month to maintain. If we say that a system spends 11 years in the maintenance phase of its life, that comes to between $15 800 and $19 800 per PC (it is much more for servers and managed environments). The purchaser of a typical small to mid-sized security system that runs on a PC is adopting this maintenance cost for each PC in the system.
The best advantage comes from IP-based systems that deliver their user interfaces through Web browsers. Such systems have maintenance costs that are much lower than those of traditional, 'fat' client server systems because there is little or no software to maintain on these so-called 'thin' client machines.
The advantage improves further if dedicated PCs can be eliminated altogether, as in the case of the so-called network appliances. Network appliances are purpose-built devices that connect to IP networks and are controlled through Web browsers. While they are, of course, computers, network appliances are not general purpose PCs and do not have the costs associated with operating system upkeep. The situation becomes better, still, if the network appliance uses solid-state design or relies on network attached storage because the MTBFs (mean time between failures) of solid state systems is superior.
Systems from manufacturers such as S2 Security Corporation address resolve these problems, for example the S2 NetBox is the first physical security management system to integrate access control, alarm monitoring, video, intercom and temperature monitoring applications in a small-form factor network appliance. The S2 NetBox utilises a new system architecture that moves advanced physical security capabilities to the network edge, eliminating the need for a separate PC-based server. This architecture makes it possible to deploy systems that scale from single facilities to multisite organisations - all over an IP network. This is what is known as a 3G (3rd Generation) product.

TCO improvement, step by step
Here is a stage-by-stage guide to reducing the total cost of ownership by reducing costs with IP-based systems:
IP network-based systems have been rapidly adopted by the information technology world precisely because of the TCO benefits. With a little planning, we in the physical security world can take advantage of this technology to reap the same rewards.
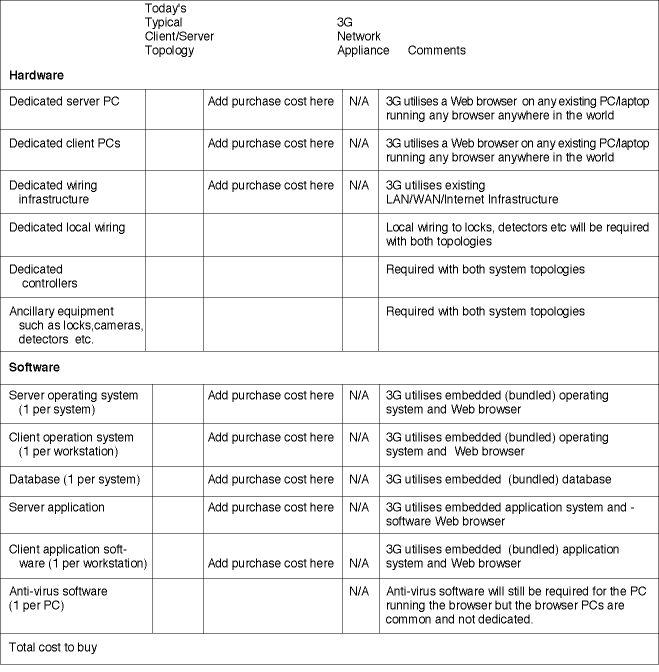
The most common response to the above issues is to state that you cannot put a cost on security - so companies do not and TCO calculations are not applied. However, recent calculations have shown that this lack of transparency has led many businesses to massively overpay for security and to become lax in the management of ongoing costs. A lot of this oversight is down to the difficulty of quantifying the various variable costs such as management of upgrades, on-going maintenance and training etc. To assist the reader to address these considerations we have produced various tables (below), which, once completed will identify the Cost to Buy, the Cost to Install, the Cost to Operate and the Cost to Maintain. Companies considering tendering for security systems would be well advised to ask for responses from potential suppliers in a format that could easily be plugged into these tables so that accurate cost of a potential system over its full life could be calculated thus avoiding the financial pitfalls of ignoring TCO arguments.

© Technews Publishing (Pty) Ltd. | All Rights Reserved.