
Whether activating a cellphone or making an online purchase, the ability to identify ourselves is essential. In the near future, card-based biometrics could be compared with on-the-spot data to certify who we are.
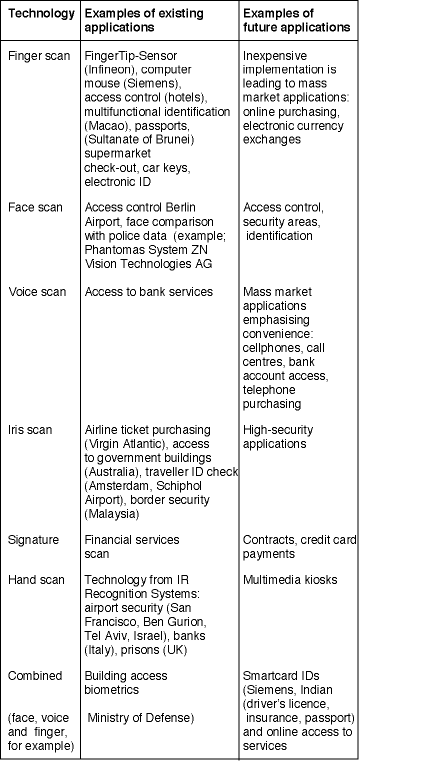
From the anatomy of our vocal cords to the swirling patterns of our fingerprints and the webs of capillaries that furnish our irises with oxygen, each of us is unique. Human beings have used the uniqueness of their appearance to recognise each other ever since the visual cortex began outperforming its olfactory counterpart. But today, the 'places' we wish to enter are as likely to be populated by machines as by people, and the people we meet are more than likely to be strangers. Whether accessing a cellphone or checking into a hotel, the process hinges on a single element: identity. Confirming who we are may require a substantial wait in the lobby or remembering a personal identification number (PIN), or, in the simplest of cases, fishing a key out of a pocket or purse and inserting it in the front door.
Fingerprint check-ins
Soon, all of this may be behind us. To get a feel for the future, just walk into the Hotel Palafitte near Lausanne, Switzerland. If you have reserved a room and been there before, all you will have to do to get in is go to your door and touch a sensor.

First-time guests are met by an employee with a laptop and a Siemens mobile FingerTip reader. Two fingers are scanned (just in case one is hurt, there is always a back-up). Outfitted with a fingerprint sensor chip, the reader produces a digital picture of the surface of each finger. "But no one ever actually sees the fingerprint," says Raphael Henrich who invented the device and is responsible for biometrics at Siemens Building Technologies Security's Product Creation Center in Karlsruhe, Germany. Instead, he explains, the image is transmitted to a Siemens TopSec ID module in the reader. The module digitises the information, reduces it to about 15 'minutia'-key geometric features - and encrypts it. The resulting fingerprint 'template' - basically a unique code - is then transferred to the hotel's database.
Before the guest goes to his room, the template is downloaded (still in encrypted form) to a reader at the guest's door using the hotel's intranet. When the guest touches the FingerTip reader at the door, the reader compares the biometric data generated on the spot with the recorded template, and, if the two match, generates an ID number for the transaction. The ID number is relayed to the door controller, which then releases the lock.
Once on file, the template can be used again any time the guest returns to the hotel. But the technology could go much further. "In the future," says Henrich, "the FingerTip system could be put to use in hotel chains. Then, if you flew to Paris from Lausanne, for instance, you could avoid checking in at the hotel, and go directly to your room because your fingerprint template would have been sent over the hotel chain's intranet."
Hotels are a natural place for fingerprint biometrics to get started because, on average, lost cards and keys cost them about US $2 per day per room. But the technology can just as easily be applied to the home, vehicle and office markets, as well as an adjunct to existing security systems. "Fingerprint biometrics," says Henrich, "is potentially applicable to a vast consumer market." Another area in which fingerprint biometrics is sure to save money and time is government services. In Macao, for instance, all 460 000 residents are scheduled to receive forgery-proof fingerprint ID cards over the next four years. When a citizen uses a card to obtain or update a government service, he or she will have to press a finger on a reader and the resulting data will be compared with data on the card and in a 'trust centre.' The ID cards, which will also display the user's signature and picture, may eventually take the place of a driver's licence, health insurance card, and even be used as an electronic purse.
Phones that know you
Accounting for nearly 50% of biometric technology sales, finger scans are far and away the leading access technology. But an important future growth area could be a technology that now holds a mere 4,3% market share: voice scanning. Among the many biometric technologies being researched at Siemens, voice holds a particularly promising position. "Biometrics will come to market from two directions," explains Dr Stephan Grashey, chief developer for speaker recognition technology at Siemens Corporate Technology in Munich. "The first is through the high-end sector, where security is at a premium. The second is the low-end sector, which is oriented toward comfort. And in that connection, voice is a shoe-in for the vast mobile phone and call centre markets."
Capitalising on the fact that the latest cellphones are already outfitted with voice-recognition technology (for example, you call your husband by simply saying his name), Grashey and his colleagues have developed a technology to generate random two-digit numbers that must be repeated by an authorised user in order to activate a cellphone. A patented technology permits the user to teach the phone what he or she sounds like (enrolment phase) by pronouncing only the numbers 'one' through 'nine' as well as the multiples of '10' up to '90'. These speech components are later used as references against which the user's rendition of double-digit numbers is compared.
Voice scans for phone banking
Speaker recognition technology is already sufficiently advanced that broker Charles Schwab uses voice authentication to allow investors to perform trades by phone, and some banks have considered using it as an access system for phone banking.
Voice scan technology has many other applications. For example, if you have ever experienced the frustration of having your online bank account shut down on a weekend after several fruitless attempts at remembering a password, consider this: voice scan technology would allow you to reopen the account by calling the bank's call centre and repeating random numbers. As with cellphones, the system would compare your voice to a previously recorded voice print. It would then send a new password to you by e-mail.
And Grashey concedes that it might be possible to use the same technology to access the worldwide telephone network. "If you had a voice print with AT&T or MCI, why not pick up the phone anywhere in the world, state your name, and then repeat a couple of randomly generated numbers? The call would be billed just as if you had used a credit card, but without all the usual trouble. It is an absolutely realistic scenario that can apply to calling, banking or shopping."
Biometric desk
As individual biometric technologies evolve, the potential for combining them, and thus further improving convenience and security, will grow. Working at a Siemens subsidiary in Pune, India and in Munich, Germany, Dr Vinay Vaidya, Arun Nair and their team have developed a device called the intelligent digital passport (IDP). The device records a user's voice, takes a digital image of his face, and registers his fingerprint. The data is then compressed, encrypted and transferred to a special smart ID card. Later, to enter a secure area, the same identification process takes place, except that the user also inserts his biometric card into a reader. The reader then compares the currently acquired and card-based biometric data. Since the data transfer is limited to the reader and card, it is exceptionally secure. Says Nair, "With the IDP, the possibility of incorrect identification or identity theft is virtually zero." The system is already in use at India's Department of Defense.
Apart from security considerations, biometric technologies can open up entirely new forms of human-machine interactions. Just ask Stephan Grashey, who, in addition to performing speaker-recognition research, is in charge of Siemens' biometric contributions to Smartkom, a project sponsored by Germany's Federal Ministry of Education and Research. The consortium is developing a multimedia phone booth and a personalised desktop. In addition to voice scanning, both use technology from the SiViT (Siemens Virtual Touchscreen) overhead projection system to recognise the user by the shape of a hand. Outfitted with a camera, the multimedia phone booth and its desktop equivalent would allow users to employ gestures as well as speech to download or send e-mail. "The project holds the potential of transforming the common phone booth and the hotel room desk into a personalised multimedia office," says Grashey. "All you will have to do is provide the biometric key." Then again, the next time you check into a hotel with a fingerprint, your room may already know who you are.
For more information contact Siemens Building Technologies, 011 652 2000.

© Technews Publishing (Pty) Ltd. | All Rights Reserved.