
This is a shortened version of a blog by Dr Khomotso Kganyago on SA’s cybercrime status.

On Thursday, the 30th September 2012, Police Minister Nathi Mthethwa announced the South African Police Services’ (SAPS) crime statistics for the period between 31st March 2011 and 1st April 2012.
When one listens and reads through the debates on this release, this quote from an unknown author – “Facts are stubborn things, but statistics are more pliable” – brings solace to their pliability, but still reminds us that cybercrime statistics are still not part of this release. This is a fact that will remain a growing, stubborn stain on a white cloth as we continue to see a wave of technological penetration in a form of devices and services (cloud) into our homes, workplaces, schools, churches, stadiums, shebeens, etc.
The defence goes on about how difficult it is to do cybercrime statistics based on the intricacies involved. Surely, if you cannot define it, you cannot measure it. Will measuring cybercrime in Mzantsi provide us with the basis of understanding improvements in the lives of the poor and ensuring that all people in South Africa are and feel safe? Crime prevention and safety is a high priority of the SA government, and Statistics SA has begun with the Victims of Crime Survey (VOCS) 2012 and will produce a VOCS series annually.
The VOCS released by Statistics SA showed that South Africans are feeling less safe in their homes despite reported decreases in house burglaries. Objectives of VOCS are to determine:
* The nature, extent and patterns of crime in South Africa, from the victim’s perspective.
* Victim risk and victim proneness, so as to inform the development of crime prevention and public education programmes.
* People’s perceptions of services provided by the police and the courts as components of the criminal justice system.
In the quest to fill the gap left in these reports, Craig Rosewarne, MD of Wolfpack Information Risk, presented the findings of The 2012/3 South African Cyber Threat Barometer report in September 2012. The event was hosted at Microsoft SA together with SecureData. The report is a strategic public–private partnership (PPP) research project to support initiatives to address the growing cyber threat facing our nation. The official sponsor of this research was the British High Commission.
Financial institutions attacks
The 2012 SA Cyber Threat Barometer is a research project with the intention to provide ongoing strategic insight and opinion in support of Cabinet’s recently approved National Cyber Security Policy Framework for South Africa. In summary, this policy framework outlines policy positions that are intended to:
a) Address national security threats in terms of cyberspace,
b) Combat cyber warfare, cybercrime and other cyber ills,
c) Develop, review and update existing substantive and procedural laws to ensure alignment,
d) Build confidence and trust in the secure use of information and communication technologies,
e) Establishing trusted forums for information sharing,
f) Developing a cyber security curriculum,
g) Raising cyber security awareness, and
h) Encouraging the ICT security industry to increase research and development.
The key issues identified by the research are:
* Denial of service, economic fraud and the theft of confidential information were cited as the main concerns for SA.
* The top cyber services targeted are Internet banking, e-commerce sites and social media sites.
* Criminals are typically mainly after logon credentials, bank or credit card information and personally identifiable information.
* The most common attack methods are still phishing, the abuse of system privileges and malicious code infections.
* The internal monitoring of suspicious transactions and the general use of internal and third-party fraud detection mechanisms are still the most effective means of detecting cybercrime.
The common top cyber vulnerabilities are:
* Inadequate maintenance, monitoring and analysis of security audit logs.
* Weak application software security.
* Poor control of admin privileges.
* Inadequate account monitoring and control.
* Inadequate hardware/software configurations.
The research pointed out that, of the R2,65 billion lost in SA in the reporting period, about 75% was recovered. “Based on the government’s average recovery rate of 75% and similar case study recoveries, the estimated loss figure would be approximately R662,5 million,” noted Rosewarne.
Figure 1 shows that Internet banking clearly stands out as the most targeted cyber service in SA followed by e-commerce web sites. That includes enterprise web portals (Internet facing corporate websites) which are being targeted as more organisations and systems are dependent on the Internet.
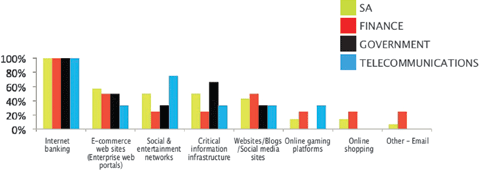
Bank customers, according to SABRIC, reported phishing related losses of R92,4 million in approximately 10 000 incidents reported industry wide. A conservative loss estimate based on other known incidents, makes up the balance. With no other reliable industry statistics, this is considered to be the minimum loss for this sector. See the blogs: Can the financial sector bank on Cybersecurity? (www.securitysa.com/*nov12bank) and Microsoft Security Intelligence Report v13–South Africa’s Perspective (www.securitysa.com/*nov12microsoft).
It was also reported during the Justice, Crime Prevention and Security (JCPS) cluster media briefing on the 25th June 2012 that a total of 155 cybercrime matters were finalised during the past financial year. They noted that the majority of cases appear to involve unlawful electronic fund transfers/fraud etc, where the password of the complainant was obtained or cloned cards being used. The conviction rate on average stands at 89%.
It is evident from Statistics SA data and the South African Cyber Threat Barometer 2012/13 report that the criminals are now focusing on the weaker link – the citizens.
Output 8 of the JCPS talks to cyber crime being combated. Cyber security remains key priorities for JCPS as it has a detrimental effect on the economy and most vulnerable people of the country. A clear view of the cybercrime statistics will help us in understanding this emerging crime in SA and enable us to plan for its reduction.
Awareness, training and proper management of security controls would therefore reduce the financial impact firstly at a corporate level, government and ultimately then for the national economy.
The developments around the establishment of the National CSIRT by Department of Communication in partnership with members of the JCPS are very encouraging. Collaboration with private sector establishment like SABRIC, ISPA, telcos, ITA, etc will help in ensuring that we have a coordinated security incidents picture for South Africa. Awareness and skill development across the board is key and it is good to see some tertiary institution already contributing to this course.
Hopefully we should be able to 'define this problem so that we can measure it' and enhance law enforcement capabilities to curb this scourge. Lastly, we need to learn from international lessons quickly on taking down of botnets and start contributing effectively.
So you think social media is fun and nobody can glean any information from your (or your kids) online and social presence that is openly and freely available to the world? Watch this video for a different opinion: www.securitysa.com/*nov12psychic. And if you are really brave, log in with your Facebook account at this link http://www.takethislollipop.com/

© Technews Publishing (Pty) Ltd. | All Rights Reserved.