
For CCTV systems the advent of networked video is perhaps the first big revolution the industry has to experience. For installation companies keen to avoid the guillotine, gearing up for this digital revolution is a major change in concepts and engineering.
Just how do you meet up to the challenge?

Recommended three point plan of action:
1. Do not jump at employing a network specialist, you really need someone with CCTV experience who understands networks.
2. Get your best engineers on a computer course that teaches simple networking.
3. Invest in the tools you need to ensure your key engineers can perform the work you expect them to handle.

Tools
The laptop PC - yes, it is expensive; yes, your engineers will use it to play games/surf the Net/e-mail the world, but these guys will most likely use the company car at the weekend as well.
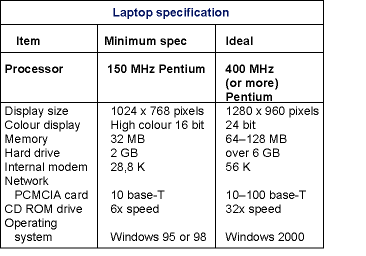
Just like buying the right company car it is important to ensure you purchase a laptop that is up to doing the job. You do not have to break the bank with a state-of-the-art laptop but take a look at the specification table, the minimum requirement will get you up and running for around R4000 while the ideal will let you fly for under R10 000. Second-hand prices can net you the minimum spec for about R1500. Personally, I use the minimum spec laptop and although video network images update slowly (around 3 per second as opposed to 20-plus for a fast machine) it does everything you need to do in an engineering situation.
Although processor speed is at the top of the specification table, it is not the key factor to use when making a purchase. As we are dealing with CCTV images over a network it makes sense to ensure the screen display is adequate.
Display resolution is more critical than screen size. You will pay more for a bigger screen but the resolution is the critical factor. The minimum display resolution, which is measured in pixels, should be 1024 x 768, anything more is a big benefit.
Absolutely critical to viewing CCTV images is the capability of the display to handle a wide range of shades and colours. Many of the older laptops can only reproduce 256 colours with the result that the images received will not be of sufficient quality to render CCTV images on the screen. High colour 16 bit is adequate but 24 bit will give excellent images.
Next is the working memory, or RAM. 32 MB is the minimum to run Windows efficiently, 64 or 128 MB will speed things up.
Hard disk storage on the machine might be critical if you want to store video images. 2 GB will suffice for most needs, a 6 or 12 GB hard drive will give you large archive capability. (Your engineers will need the space for all those games.)
Most video servers presently run on Ethernet 10 base-T networks. Some newer laptops have this facility built-in but more likely you will need to buy a PCMCIA network card. This fits into a slot on the side of the laptop. Do not buy a laptop that has not got at least one PCMCIA slot. (Most have two). 10baseT PCMCIA cards are readily available but for very little extra outlay you can buy a card that works with 10baseT and 100baseT. It means you can link into the faster 100baseT networks that are often the backbone of 10baseT networks. It is a bit of future proofing that is well worth the few extra rand.
An integral CD drive is mandatory as most of the software you need will be on issued CD ROM.
Integral MODEMs are fitted to most laptops, nowadays 56 K (speed in bits per second) is fairly standard but a 28,8 K will do if you can suffer longer update times for images across PSTN lines.
Most of us are familiar with the Windows operating system, the laptop should have Windows 95 as minimum, Windows 98 preferable. The next generation is Windows 2000 or XP, set to be the future business standard. All of these are good operating systems, earlier or domestic type systems are not suitable.
Finally, an available RS232 port, COM1 on most laptops, finishes off the specification. At this point can I mention that grateful engineers with new laptops can send me a bottle of scotch next Christmas.
That was the expensive part, now for the basics.
Cable crimp tool
This is the magic whatsit that puts RJ45 plugs on the end of network cables. The cable universally used on most networks is usually CAT5 and can run to a maximum of 90 m from one network device to another.
CAT5 cable
CAT5 consists of four twisted pairs, each wound at a different pitch of twist to prevent interference from its neighbours. It is inexpensive so do not use substitutes like CAT3 or 8 core alarm cable.
Wiring CAT5 into RJ45 connectors
Each pair in the cable consists of one solid colour and one similar colour striped with white. By convention the pairs are: blue white/blue, orange white/orange, green white/green and brown white/brown.
CAT5 pairs are arranged in the RJ45 plug as in the diagram. Only pairs 2 and 3 are used by the network.
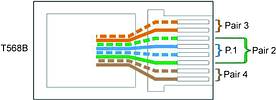
Note that pair 1, located in the middle of the plug is blue and white/blue. This is not used by the network and by convention, when RJ45 plugs are used for telephone connections, this pair carries the telephone signal. So no worries when you plug the right plug into the wrong socket. (see diagram 1)
There are two specific ways to wire CAT5 into RJ45 plugs, T568A and T568B. Provided both ends are wired as T568A or T568B the cable will connect a video server to a hub. If one end is wired as T568A and the other end wired as T568B the cable is a crossover type which can be used to connect a PC direct to a video server.
Care must be taken that the pairs are wired correctly, the standard cable is a pin for pin connection, a crossover cable swaps over pairs 2 and 3.
Whether you use T568A pinouts at either end or T568B pinouts at either end is not important. The cable will still work. It is best to decide on one format and stick with it, in our examples we will use T568B which seems to be the preferred standard.
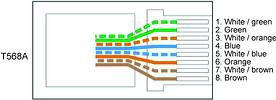
To make a standard cable, wire up both ends with T568B pinouts. To make your crossover cable, wire one end as a T568B and the other as a T568A. (See diagrams 2 and 3)
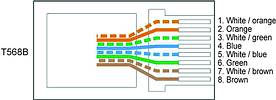
Your toolkit should now include one standard cable to connect your laptop to a network hub, and one crossover cable to connect your laptop direct to a video server.
Cable test box
Once you have made your cables you will need to verify that they are wired correctly and operationally sound. The best way to do this is with an RJ45 cable test box. From between R400 to R1000, depending on features, you may think this extravagant, but believe me it will save you hours of heartbreak when eliminating gremlins from your system.
Conclusion
So now you have got the tools, all you need is a bit of network knowledge. For many people this seems an insurmountable challenge, but if you want to get the knowledge, you will have to tune in next month.

© Technews Publishing (Pty) Ltd. | All Rights Reserved.