

In the mass data storage and communications industries, security and dependability are at the forefront of customers’ minds. But, firewalls and encryptions are only part of the solution. If somebody breaks into the facility and steals the server, everybody is in big trouble.
A data centre is a centralised repository, either physical or virtual, used for the storage, management, processing and dissemination of data and information organised around a particular body of knowledge or pertaining to a particular business, usually treated as a mission-critical operation or facility. Just about every company has its own data centre. A small local insurance agency calls it a computer system. The insurance conglomerate might call it the computer room. In many instances, the data centre is part of a company that provides data services to its customers.
The data centres market is an important prospect base for building contractors with growth estimated at 11% through 2014. When building their infrastructures, the design needs to provide the ability to scale and adapt to support future needs with near-zero downtime. It involves integrating IT, HVAC, lighting, fire and safety, and communications monitoring and control systems and algorithms to process and monitor data. Lastly, data centres require real-time access to local vendor technical expertise with strong reputations.
The layout of most large data centres is similar (Figure 1). There is a security/reception area that the user enters to gain access to their system. Upon check-in, they go to the lobby. From there, they go through a sally port to get into the secure common area. What this means is that, at the end of the lobby, they must be identified as authorised to enter the sally port room. Upon entering it, the door is closed. At the end of the sally port room, there is another identification authorisation performed before they can go through that door to the secure common area. At this point, they can go to their own cage or vault, where they will again be identified as authorised before going through.
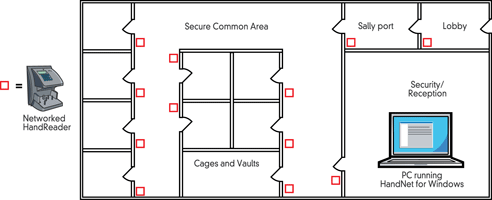
Most data centres also have similar customer needs. First of all, because of their mission-critical nature, they need a high level of security. They typically have a large number of infrequent users. This is especially true of independent data centres which have large numbers of customer users who only occasionally visit the site. Therefore, the system has to be easy to use but cannot rely on cards which can be easily transferred from person to person.
For offsite storage facilities, the challenges are even greater. They require remote enrolment and multifacility management in which customers need immediate access but the security level must remain quite high.
What is meant by a security level? They range from high to low with the lowest being something you have, such as a card. Perhaps, it is an employee card that can be swiped through a magnetic stripe or proximity reader, just as at the entrance to many companies. Can another use this card? Of course, as at this level, you are only checked for what you have.
The second level of security is something you know, like a PIN number or password. It could be your mother’s maiden name or where you were born. The theory is that only you would know this. But, if you wanted to, you could tell another what your PIN or password is and they could use it. And, they would get entry, because, at this level, you are only checked for what you know.
The third level becomes trickier to fool. It checks for what you do. The most common application at this stage is to write your name and have it verified that it indeed matches the signature on file. Can your signature be forged by someone who really wants to share your access credentials? Of course!
That is why the highest level checks for things you are…in others words, a biometric. Biometrics identify people by unique human characteristics, the size and shape of the hand, a fingerprint, the voice and several aspects of the eye are some of the unique attributes that make you you and me me. A biometric access control reader compares a person’s unique characteristics against a previously enrolled image for the purpose of verification.
Since the challenge in such offsite storage and information handling facilities has been to provide employees and customers with immediate access while at the same time producing a level of security commensurate with the value of assets being protected, clearly a simple card-based system, where cards can be lost or stolen is not the answer. PINs, passwords and signatures do not help either.
Therefore, it is no surprise that, for data industry leaders, when addressing the questions of physical access control, the overwhelming answer has been biometric technology, which provides a level of security beyond that of conventional card systems by verifying the identity of the person. Hand readers and fingerprint scanners provide a level of security beyond that of conventional card system by verifying the identity of the person.
At the same time, they eliminate the burden and expense of a card-based system. Cards generally cost several dollars each and reissuing them takes time. In addition, forgotten and misplaced cards degrade the effectiveness of a security system. Today, Internet data, telecommunications and co-location facilities around the world are using biometrics for their physical access control because they offer high security and convenience.
How do biometric devices work?
For instance, the hand geometry reader simultaneously analyses more than 31 000 points and instantaneously records more than 90 separate measurements of an individual's hand, including length, width, thickness and surface area, to verify the person’s identification. In conjunction with a PIN number or swipe of a card, the registered individual can gain access to the facility.
However, the authentication process involves a one-to-one search. A live biometric presented by the user is compared to a stored sample, previously given by that individual during enrolment, and the match is confirmed. The hand geometry or fingerprint of the user is not stored in a database or on an ID card. Instead, a mathematical equation, or algorithm, is performed with points measured on the finger or hand. The template that results from this equation is all that is stored.
When the user presents an ID card or enters an assigned PIN, only that template is transmitted. When the employee presents his/her hand or finger, the reader runs the authentication process to determine if the template that is stored matches the biometric being presented. If there is a match, the person is authenticated.
Hand geometry is selected for many reasons, including:
* Easy to install and maintain.
* Field-proven in high volume applications, such as San Francisco International Airport with its up to 250 000 transactions in a day.
* Easy to enrol people and easy to use.
* Best combination of high speed and accuracy.
* Good for all population sizes and high volume applications.
* Eliminates privacy concerns.
* Integrates into existing card and access systems.
The most common way to integrate biometrics is through ‘card reader emulation’. This method is especially effective when integrating into existing card-based systems. The wiring is identical to the card reader’s wiring.
In this mode, the biometric device essentially works with the access control panel in the exact same way that a card reader does. The ‘card reader output port’ of the biometric is connected to the panel’s card reader port. When a person uses the biometric, it outputs the ID number of the individual if, and only if, they are verified.
The format of the output is consistent with the card technology used by the access control panel. Once an ID number reaches the panel, it is handled as if it came from a card reader. The determination of granting access is made by the panel. The access control panel, not the biometric, handles door control and monitoring.
Which biometric fits your application?
Hand readers and fingerprint readers cover 80% of biometric access control applications. They are complementary, as each meets specific needs in the market. When using these two technologies under a single platform, dealers, integrators and users can create technology alternatives, fitting the appropriate biometric technology to each access point.
Fingerprint readers bring biometric security to low volume applications. Fingerprint readers complement hand readers by being a low-cost biometric that is best used on doors accessed by less than 100 people. Such small user populations are where most fingerprint readers are being used successfully.
In these applications, the total number of transactions tends to be fairly low. Therefore, issues generated by the higher error rates exhibited in fingerprint technology ends up being a minor inconvenience rather than a major hassle. Yet, adding the biometric technology provides a huge increase in security over a ‘card only’ system.
For these low volume openings, cost is a key consideration and fingerprint products meet that need. For instance, a fingerprint reader is ideal for sensitive document and high value storage locations accessed by 10, 20 or 30 people. This has been a major growth area for fingerprint products. They will also squeeze into small areas, like at the door to a medical cabinet. They are best when used indoors.

© Technews Publishing (Pty) Ltd. | All Rights Reserved.