
The way we use identity is changing. In a continuing assessment of these developments, Lynne Larsen looks at how identity is being used to extend the benefits offered by secure access systems.
Last August, Hi-Tech Security Solutions spoke to Mark Eardley about BioDentity's approach to identity, including the company's PLAT methodology and the ways it associates data according to Person, Location, Activity and Time. The premise that identity has several interrelated or associated components is a fundamental principle in this approach to using identity as a business tool that accelerates processes and increases their integrity. In this issue, we look at solutions that are doing just that.
Linda Glieman, divisional manager of time and access solutions at Business Connexion, agrees with Eardley's thinking around the methodologies of working with identity. Business Connexion is currently rolling out its new access validation module (AVM), which extends how the company uses identity to produce solutions that are more capable of managing authorised access.
Glieman says, "It is no longer acceptable to simply grant access based on a single identifier linked to a name and employee number. We need integrated solutions that tell us much more about a person before granting access. For example, many organisations need to know if a person has received the correct induction training and that it is still valid; that the right medical clearances are in place and up to date, or that the person is appropriately licensed or accredited to perform certain tasks."
Glieman sees the traditional role of access control changing to encompass risk control, thereby delivering benefits in relation to operational health and safety issues. She says this is particularly relevant for organisations operating in inherently hazardous environments, citing the mining, petrochemical and heavy industries as pertinent examples, "We are working with companies in all these sectors to reduce the risks created by unauthorised access. It goes way beyond the usual security constraints of preventing illicit access and the criminal activities associated with it.
"Obviously, security remains a cornerstone of AVM, but it is not its sole motivator. Highly competent, proven biometric systems are now available to authenticate identity. Such biometrics also eliminate the inherent weaknesses of card or pin-based systems - positively identifying someone is no longer the challenge it used to be. For us, the next step is to work more smartly with that verified identity."
Identity in logistics
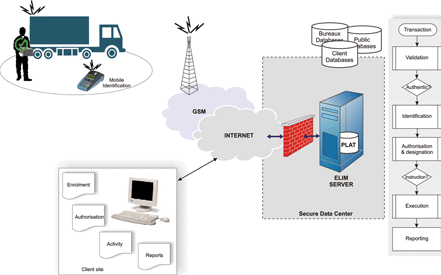
Electronic Logistics Integrity Management ELIM exemplifies how the traditional thinking around identity is evolving. Eardley refers to this evolution as 'extended identity'. He explains that, within the world of access control, "We are accustomed to thinking of identity as primarily relating to individuals. The principles of 'extended identity' are being applied within ELIM to include other types of identity such as vehicle registration numbers, waybills, package barcodes and POD certifications."
From opening a container at Durban docks, right through to placing an item on a retailer's shelves in Johannesburg, ELIM can record the location and time of each activity involved in the process. In itself that may be nothing new. What is new is the fact that ELIM uses fingerprints to authenticate and record the identities, activities and locations of each person in the chain. "Essentially, ELIM uses fingerprints to authenticate who did what, where and when throughout a supply chain."
According to ELIM's developer, Marius Coetzee, managing identity is critical within the logistics industry. "We have spoken to a number of logistics companies and have found a commonality of identity-related challenges amongst them. Being able to monitor activities based on identification is central to many of these issues. The system extends identity management beyond personnel to include items such as trucks, containers and the goods within them," he explains.
"We will be ready to take ELIM to market in May this year, and are working towards this with one of South Africa's major access control and T&A solution providers. The official launch will take place at the SAPICS Supply Chain & Operations Management Conference at Sun City from 29 June to 2 July."
The hardware component of ELIM is Sagem's MT2G mobile biometric terminal. Coetzee says, "The unit's combination of fingerprint biometrics and GPRS communications is particularly significant. It enables us to manage identity accurately and to deliver diverse functionalities to the terminal from our servers."
As examples of these functionalities, Coetzee explains that, "We can capture weighbridge readings and the identity of the person who entered them, and then auto-link this info to time and location. On the same basis, we can record who cartonised a shipment, who packed it on a truck and who received it at a retailer. All of these types of functions can be run from the mobile terminals."
Identity in action
Stanley Blick already has many years' experience of providing access and T&A solutions to the logistics industry. Blick's Chris Thompson introduced Value Logistics to EVIM (Electronic Visitor Identity Management) some months ago and after on-site trials the company has ordered four EVIM mobile terminals to control access at its Isando depot.
Thompson says, "Our clients in this sector were quick to realise the advantages of biometrics for highly accurate access and time management and were already comfortable with the efficiencies delivered by the technology. The EVIM platform represents the next generation of practical solutions that can deliver a new set of commercial benefits to our logistics clients, based on processes and technologies that are well-proven."
In addition to capturing visitor information and confirming their identities, Value is extending its use of the system to record various data relating to trucks as they enter and leave the group's main Johannesburg depot. Rory Greene, the company's national loss control manager explains, "We first capture the details of the vehicle, tractor, trailers, containers and their seals. We then allow the driver to capture his own ID number and to sign off the details by scanning his fingerprint. All of this is done on the portable terminals which then print a numbered exit or entry permit with the name of the driver printed clearly on the slip."
Web-based identity reporting
All of the identity data relating to the truck is uploaded in realtime via the GPRS-enabled terminal to BioDentity's central servers at Verizon. Greene accesses his information through EVIM's Web-based functionality, giving him complete, time-based reporting on every visitor to the site.
He sees the system as delivering a number of distinct benefits. "First of all, it is far more secure and far more accurate than the old paper registers. Quite simply, there is nothing else like it on the market. Our four terminals handle over 400 visitor transactions a day. Previously, we used traditional visitor books to register who was coming onto the site. Now, we do not get people entering their name as Peter Pan or Patrick Swayze like we got in the old registers. Neither do we have to live with the problems the books created in terms of accuracy, storage and retrieval. Now it is all available at the push of a button - and the identities are verified."
Greene goes on to say that Value's multiple business units can access the information: "For instance, our operations and warehousing staff are able to use the data for their own, task-specific purposes relating to the arrival and departure of trucks and the containers they are carrying." He also likes the flexibility the system gives him, saying that, "To cope with foreign nationals who do not have a South African ID number, our system now includes a field for passport numbers and is able to validate their authenticity."
For details contact QData DynamiQue (Business Connexion), +27 (0)11 266 5287, [email protected], www.bcx.co.za or BioDentity, +27 (0)11 234 0865, [email protected], www.biodentity.co.za

© Technews Publishing (Pty) Ltd. | All Rights Reserved.