

This article gives an overview of different biometric technologies that can be applied in physical and logical access control to secure a corporate environment. Issues such as privacy are also addressed.
Recent reports in the media have put the spotlight on the security of on-line banking, and specifically on how secure authentication mechanisms such as passwords and PINs actually are. Biometrics provide an accurate authentication mechanism, which will allow corporates to effectively secure their internal networks and access to company-confidential data.
In terms of information security requirements, biometrics display a number of advantages above more traditional authentication mechanisms such as passwords. Increasingly biometrics is being applied as the secure option to physical and logical access control solutions in corporate environments. This article will explore biometric technologies a bit further, specifically in reference to its use in a corporate environment.
Biometrics is the science of measuring unique physical or behavioural characteristics of individuals, such as the tiny swirls etched in the skin of a fingertip, micro-visual pattern on the iris of the eye or the geometry of the hand or a finger. There are a number of biometric technologies in use, with the most common being fingerprint, face and voice.
Biometrics vs traditional security systems
The traditional operating paradigm for security systems used to be a combination of something you have, such as a token, and something you know, such as a password or PIN. The addition of biometrics extends this paradigm to someone's unique physical attributes - something you are. Some of the main features that are required for a person to be uniquely identified are universality, uniqueness, permanence and measurability - attributes shared by most biometrics.
Benefits
Some of the benefits that biometrics have over other authentication technologies include the fact that it cannot be lost, stolen or forgotten, and it can also not easily be shared. There is no need to carry physical tokens around, no need to remember a whole host of passwords, and resultantly there is a major reduction in administrative effort required for password maintenance.

Choosing a biometric system
Research done by the International Biometrics Group (IBG), a leading independent integration and consulting firm to the biometric industry, highlights four main criteria considered to be the most important when choosing which biometric technology to go for and how the different technologies compare. The first two criteria focus on the end-user of the system and are the level of intrusiveness and the amount of effort required from the user. The other two criteria are aspects that relate to the technology - the cost and the accuracy of the systems. Comparing different biometrics technologies according to these criteria indicates that there is no one 'ideal' biometric, and that there is typically a trade-off between these criteria.
* The finger scan is the most widely used biometric, and is based on the unique pattern of ridges and valleys visible on the fingertips. Fingerprints are relatively accurate and easy to use, but there is a potential negative social perception around the use of fingerprints through association with criminal applications.
* Hand geometry is a relatively 'simple' biometric based on the size and shape of the hand, which requires a bit more effort from the user than fingerprinting.
* Face recognition is becoming more popular, especially for immigration control and anti-terrorism applications, and the technology is based on the spatial features found in a face image. The accuracy of this technology is steadily improving, but the cost is still relatively high.
* Iris and retina scans are typically used for access control in a high-security environment, but these are both relatively costly and also intrusive technologies. A retina scan uses the unique pattern of blood vessels on the retina for identification, while an iris scan analyses the random pattern visible in the retina.
* Voice recognition is typically based on a frequency-domain analysis of a person's voice, which depends on both the physical and behavioural attributes of an individual. The accuracy of this technology is steadily improving, and one of the major factors counting in its favour is the prevalence of voice 'scanners' ie, microphones, which is often a constraint in rolling out biometric systems. There are definite advantages to combining different biometric types, and this could be a way to enhance security while combining the positive attributes of each technology.

How it works
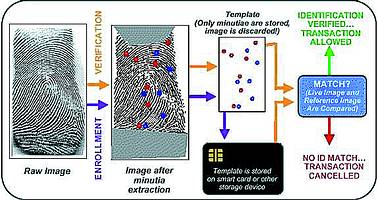
The three main processes encountered in any biometric system are enrolment, identification and verification. During enrolment the original reference sample or training set of samples is captured and stored in a database or other media. This step is crucial to the overall accuracy of the system, and care must be taken that high quality samples are obtained during this step.
During identification the system needs to try and find a match for a provided sample from the database of reference samples through a one-to-many search. The system would typically try to apply some form of filtering or binning to reduce the candidate list of reference samples before attempting a match, which is a resource intensive task. Verification is a relatively simpler task, as it requires the system to attempt to match the presented sample with the reference sample of a claimed identity, ie, a one-to-one match.
Biometrics and privacy
Some of the fundamental principles governing the information security aspects around e-commerce are privacy, authentication, authorisation, data integrity and non-repudiation.
Biometrics can enhance a person's privacy through making sure that only I can access my own private data. Conversely my biometrics is considered to be part of my private data, access to which is protected by law, such as in Chapter 8 of the ECT Bill. Generally the obtaining of biometric data requires the consent of the individual subject, failing which the right to privacy is invaded.
However, no consent is required where a statutory provision obligates persons to disclose certain information that may otherwise be regarded as private. The Census Act and Income Tax Act are two such examples, and the Identification Act of 1997 makes specific reference to the capturing of fingerprints.
The issue of privacy has been a major concern to specifically civillibertarians, who argue that technologies such as biometrics could be used to track their movements and activities - effectively creating conditions conducive to the setting up of an Orwellian state employing the structures and technologies of surveillance for normalisation and discipline of citizens. The debate basically comes down to Balancing the Bs - Big Brother vs Benefits via Biometrics? What level of intrusion will be tolerated to allow this technology to solve problems such as identity-related fraud or identity-theft?
The Liberty Alliance
The Liberty Alliance is a broad-based industry body aimed at identity management, and the market's need for a global standard that is open, interoperable, and decentralised. Its vision is one of a networked world in which individuals and businesses can more easily interact with one another, while respecting the privacy and security of shared identity information. For the 'federated identity' vision put forward by the Liberty Alliance to be implemented effectively, there needs to be trust established between all parties involved. In their view, advanced trust credentials include smartcards and biometric data such as fingerprints or retinal scans.
"The key to preventing the loss of our liberty and autonomy is not to prevent the spread of technology, but rather to ensure that it is used properly and in a transparent nature," says the Liberty Alliance.
Authentication is the primary role of biometrics, and, other than solutions such as smartcards or digital certificates, it identifies people rather than devices or entities such as companies. Biometrics on its own cannot ensure data integrity, but in combination with digital certificates this can be ensured. The X.509 certificate format already takes biometrics into account. It is feasible that your biometric template could be codified to be used as private key in non-symmetric encryption schemes. Biometrics puts one's personal seal on a particular transaction, therefore the individual cannot claim that a particular transaction did not take place - non-repudiation! This has huge potential as a deterrent to fraud!
The market/opportunities for biometrics in SA
The biometrics market in South Africa seems to be shifting from mainly physical access control applications to logical access control applications, such as single sign-on applications for corporate networks and e-commerce. A prediction for the future is that the market will also shift towards more service-based offerings with biometrics at its core. This is also in line with the current prevalence of Web-services in the Internet domain; biometrics-based Web services will become more prevalent.
Logical access control
Authentication is one of the most important steps in providing corporates with logical access control to internal computer networks and sensitive data, and biometrics would be an elegant solution in securing access to these environments.
E/m-commerce
Research suggests that biometrics could have a huge impact not only on the e-commerce market but also on the mobile (m-commerce) market. With the convergence between cellphones and PDAs increasing the power and functionality of these devices, there will be a resultant increase in the need for secure and accurate authentication of the individual using that device. A huge bonus is that the first biometric sensor, ie, the microphone, is already built in by default!
In on-line transactions such as electronic funds transfer (EFTs), biometrics could play a role in authentication, typically in combination with smartcards or a public key infrastructure (PKI) environment. In an off-line environment, a biometric smartcard would be an ideal solution, whereas biometrics in combination with PKI would be a good solution in an on-line environment. This could be one of the technology drivers for a move towards a cashless society, which has many benefits associated with it.
E-government
Biometrics is currently in use in a number of e-government applications, and there are a number of other applications that could also benefit from this technology. Existing applications include the Home Affairs National ID System (HANIS), pension payouts and the Criminal Justice Systems (CJS). Examples of other applications where biometrics could be used for authentication include government procurement, SARS e-filing and the taxi re-capitalisation project. The recent Bill on Electronic Communications & Transactions (ECT Bill) does provide a legal framework for the use of biometrics, and it touches on various e-government services, secure transactions, authentication service providers and consumer protection, which includes non-repudiation. All of these aspects could have an element of biometrics involved.
The HANIS project is considered to be one of the government's flagship projects where biometric technology is employed, and the aim is to provide each eligible citizen with a smartcard-based national ID document that includes the user's fingerprint biometrics. The card will be used for visual, off-line and on-line identity verification. The aim is to have a number of government applications resident on the card, which will also include an e-purse application.
Biometric standards
One of the major drivers for the use of biometric technology is the convergence of standards at an international level. A number of bodies such as ISO, IEC, ANSI and NIST are actively involved in the development of international standards. South Africa is represented on a number of standards bodies such as ISO/IEC JTC1 SC17 and SC37, which focus specifically on the use of biometrics. A local expert group has been established to review work items coming from these bodies and to adopt, adapt or contribute to them from a South African perspective.
For more information contact Dr Nick van der Merwe, CSIR Information & Communications Technology, 012 841 4355, [email protected]

© Technews Publishing (Pty) Ltd. | All Rights Reserved.