
Enterprise security is a little more complicated than simply stringing a few scanners and alarms together. High-risk, high-value businesses, require professionally integrated, managed security solutions; solutions that offer complete control – allowing administrators to know what is going on everywhere, all the time.
To achieve a system of this quality, one needs a partner who is able to deliver a full spectrum service - from initial process and risk analysis and the formulation of a protection plan, all the way to design, implementation and maintenance of the system itself. Siemens ESS aims to be that partner.
At the heart of its access solutions is Siemens' Autec Babylon NT Kernel - a flexible building management system. This application is completely modular in its design, allowing for a system that uniquely caters to a user's requirements, whilst allowing for easy future expansion, as the security needs of your organisation grow. Babylon is specifically designed to cater for the needs of the security manager who requires one system to monitor and control the whole building from a single interface.
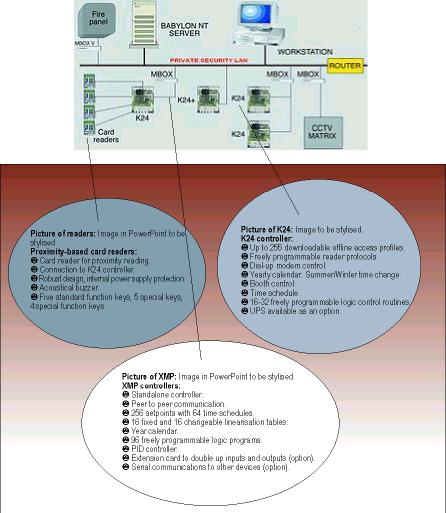
Core system features:
* Access control: online tool that allows/disallows people into and out of areas in an organised manner. Every time a person enters or leaves the building, a 'booking' event is stored in an access logbook, which can be scrutinised at any time. System controllers are also equipped with basic offline functionality, so as to be able to maintain security measures at all times.
* Anti-passback for up to 999 rooms, including two in offline mode. Separate anti-passback is available for parking garages.
- Individual readers and card holders can operate without anti-passback.
- On-line decisions made on the main PC.
- All access transactions logged in the access logbook.
- Four eye control for secure areas.
- 200 access zones with an option of 1000 access zones.
- 256 online and offline profiles available.
- All online profile names are freely definable.
- All profiles can handle up to seven time zones, seven days and nine holiday types.
- Up to 99 card version numbers are allowed.
- Realtime dynamic data can be displayed.
- A separate page for data is attached to each card holder.
- Temporary profiles can be attached to individual card holders.
- Double access control blocking.
- PIN code badging allowed.
- Silent hold-up alarms possible with pin code readers.
- 300 000 card holders possible.
* Time management: complete management of all times generated by employees via card reader bookings. Can be used as a complete shift or time and attendance management system.
* Personal limitation: this feature would be used only where the time spent in a given room has to be limited due to factors such as health hazards. Alarms are generated when the time spent in a room has been exceeded, or when the maximum number of people has been exceeded. Up to 100 rooms can have personal limitations.
* Visitor handling: an electronic solution for keeping track of all visitors entering and leaving a building. The system is able to record visitor name, company and ID number, and offers four different options for the handling of each person. Visitors can be blacklisted on the system. All entries are stored in the visitor logbook.
* Logbooks: every event that occurs within the system, or from one of the attached devices (alarms, controllers, etc) is stored into a digital logbook, from which users can search, sort, retrieve and print events when required. Books are kept within the system for access, alarm, event, time, trend, error, visitor and video logs. The system provides for logbook backup onto any media supported by Windows NT.
* Alarm handling: all 'events' that are required to trigger an alarm are pre-defined in the system, which offers the capacity for up to 26 alarm groups and 100 alarm priorities. When an alarm event occurs, a notification is sent to the operator, who is required to perform certain alarm cancelling tasks (such as the provision of an explanation for the alarm) before it can be removed from the queue. Supervisors have the ability to view logs of all alarm events, in order to monitor the performance and response times of individual guards.
* User passwords: every system operator can be allocated a unique password, to which a profile containing their necessary access permissions can be attached (certain functions can even be set up so as to require two simultaneously logged in users). In sensitive areas, such as publicly accessible operator terminals, the password system can be supplemented with a card reader, ensuring optimal security.
* Operator stations: the inclusion of distributed operator-stations allows for improved management and operation of the system. Any program can be executed from any station, provided that the operator's login profile allows him to do so. Up to 31 stations, connected by RS232 or Ethernet, can be catered for.
* Automatic remote site dialup: this convenient facility allows for the monitoring of remote sites via ordinary dial-up modems. Dial-ups are initiated manually or automatically, from an easy to use graphic screen. Up to 1000 dial-ups are catered for.
* Routines: allow the system to control and manipulate parts of the building or plant. Routines are written in editors on the system and downloaded to the XMP devices while the system is online. Complex control logic is possible.
* Maintenance management: allows the maintenance departments to have an online maintenance and breakdown status of the plant or building. The system allows for 50 000 freely definable data points for daily, weekly or monthly maintenance. Realtime monitoring is possible.
* Tools: tools are provided in order to allow for further system customisation. These include:
- Screen modification program.
- Menu modification program.
- Keyboard modification program.
- Colour modification program.
- Icon menu modification program.
- System monitor program.
- VCI interchange and logbook reset program.
- Graphical font modification program.
- System message modification program.
For more information contact Siemens ESS, 011 652 2000.

© Technews Publishing (Pty) Ltd. | All Rights Reserved.