
Card Control Systems has been awarded the contract for the installation and implementation of the centralised access control system at the University of Pretoria (TUKS) for the main as well as all satellite campuses. The system installed is the Softcon (Softwin 3) version access control system. The consulting engineer is Pieter du Preez from the company Delport and Du Preez Consulting Engineers.
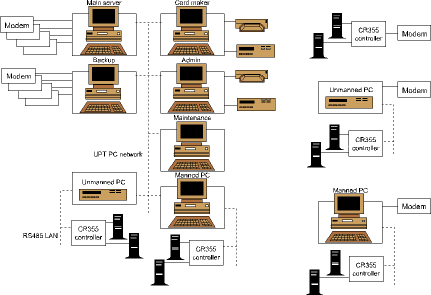
The system consists of 44 PCs, 151 controllers interfacing to 302 readers, 33 Booths, 46 turnstiles, 31 vehicle booms and 53 controlled doors and gates. The main database of the access system is located at the main server. Workstations such as the card maker, admin and maintenance PCs access this data directly. All other PCs (or groups of PCs) in the system contain a copy of the database and function as individual systems, independent of a link to the main server. Links between the main server and the PCs in the system is via on-line TCP-IP links or via dial-up modems (PC networks not available). Data is synchronised via a database distribution program as described below. Where operator access to PCs is not required, monitors are not installed (portable units are used when maintenance is not possible via the on-line or dial-up networks).
Communication to on-line controllers is via RS485 multidrop LAN. Standalone controllers, which contain less than 15 000 active cards, are connected to the server via dial-up modem.
Access control
75 000 cardholders use proximity cards at the student residences (access to residence parking areas and to the hostels), and ISO MAG cards for access to the campuses and buildings. The MAG cards also serve as the student, staff or contractor ID cards and contain a photo. MAG cards contain a 10-digit card number, which includes the student/staff number and an issue number. Access to area zones is granted to cards individually and/or in groups (eg, access to a parking group and to specified zones). Cards can be set to auto expire, resulting in the status of the card changing to disabled or capture and the zones the card has access to can also be set to change (eg, access to parking and into building denied).
Access to area zones is via readers connected to the Softcon CR355 controller that interfaces to two readers. Each controller contains the latest 15 000 cards that grant access via the two readers. When a card that is not in the CR355 database requests access the controller requests data from the PC and if access, is granted, the card replaces the oldest card in the controller database.
When a controller functions in an offline mode, up to 1000 transactions are stored with time and date stamp.
Pay parking control
On entrance to a pay-parking area, a MAG card is issued and the time of entrance is recorded in the system. A free period is set and if not within that period, the card has to be presented to a pay point and after payment, the free period is reallocated. Information readers are provided to show the time remaining or the amount due.
Database distributor
A highly configurable program synchronises databases in the system. Upon operator request, or at preset times/intervals, PCs upload audit files that contain all changes made to databases by operators or via converters, to the main server where the audit files are logged and the latest changes are recorded in the main server database. These latest changes are then sent to all PCs in the system, via the on-line network or via the dial-up modems.
When the communication is via a modem, any of the four allocated modems are used and if busy, another is selected. When none are available, the distributor reattempts after a set time-out.
All activity transactions are sent to the main server, which keeps a log of all transactions in the system. These logs can be sent to select PCs in the system.
When alarm events occur, these transactions are immediately sent to the main server.
Card maker
The card maker is used to enter cardholders data, take a photo and to print the ID/access card. For MAG cards, issue numbers are automatically incremented when a card is programmed. Access to campus areas and certain buildings are set (access to certain areas such as laboratories, computer rooms, etc, are set at the building PCs or via area zone data converters). Photos can be imported from JPG files received as attachments to e-mail received from other campuses. Data changes are distributed between the PCs in the system via the database distribution program.
Data converters
Card data is received from the university administration system in an ASCII file, containing student number, name, department and address information. This data is converted and loaded in to the Access main server database and is distributed to the PCs and controllers via the database distribution program. Data for existing cards are changed and new cards are automatically added.
An area zone converter adds or deletes selected area zones from cards referenced to via ASCII files. Typically, students that are granted access to a lecture room, to a laboratory or to areas in a building, are listed in an ASCII file and are added when access is required (eg, to write a test) and deleted when not required (eg, after the test has been completed).
Maintenance
When telephone networks are not available for the modems, GSM modem modules are used until the networks are restored. SMS and email for certain alarm messages (eg, controller off-line) are being incorporated. The automatic generation of reports and the email thereof can be selected.
A variety of future additions to the system are planned, namely Web, additional integrated email and SMS functions. A link to the existing canteen system has been completed for the integration of vending machines on the campus to allow for cashless vending.
For more information contact Card Control Systems, 011 907 3192 or Softcon, 012 348 7301.

© Technews Publishing (Pty) Ltd. | All Rights Reserved.