
The digital video market has undergone a significant transformation during the past few years. Digital video technology has become popular as a replacement for analog CCTV.
As a result, digital video recorders and standalone systems have become a large and fast growing market segment. Many businesses have spent a great deal of capital on their existing analog systems and associated infrastructure. At the same time, they understand the value and need for digital video technology, and many companies have created budgets for digital video solutions. The technology is still new, and digital video recorder (DVR) devices are introduced to the market almost every day. As a result, the focus has been on the 'box'.
Customer interest should instead be directed toward what digital video technology can contribute to a business' total security environment. There are three market segments in which digital video technology functions as part of a business solution. These include DVRs, nonintegrated digital video management systems (DVMSs), and DVMSs as a seamlessly integrated part of a total security solution.
Standalone DVRs
The most rudimentary of these is a standalone DVR. These devices are typically used as low cost replacements for analog VCRs. Because of high demand and a proliferation of such hardware on the market, DVRs have become price-based commodity items. They have limited functionality and operate independently of other systems, making them ineffective in serving the complex security needs of today's businesses.
Although a nonintegrated DVMS offers substantial improvements over a simple DVR device, it is still limited. It typically has a user interface that enables the system operator to control recording and playback, and to display video in one or more monitoring windows. However, it is only a partial solution, because it cannot link video to related alarms and event information from other systems that are critical to a company's security needs. The system does not recognise that the different events are related, so they cannot be monitored as a single occurrence in a central station monitoring environment. Centralised administration and management of nonintegrated systems is impossible. Information is stored in multiple databases, and because management requires multiple security administrators, such systems are cost ineffective. The fundamental problem remains that there are multiple, unrelated systems trying to behave as one.
Open architecture
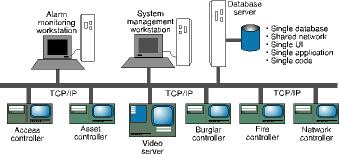
Digital video technology's true value to security is realised when it is seamlessly integrated into a Total Security Knowledge Management Solution. With seamless integration there is a single system based on a scalable distributed architecture, in which various components can be seamlessly plugged through well defined 'open interfaces' and behave as an integral part of this system.
The heart of a seamlessly integrated solution is open architecture. An open system is one that is designed in accordance with accepted standards in use in the computer industry, and one that can easily integrate with other applications and devices. Only a system that is both device and data exchange independent can be considered truly open. Open architecture allows a company to create a security management environment that includes nonproprietary, off the shelf devices and applications, standard operating systems and databases within the existing corporate network infrastructure. For digital video solutions, open architecture provides support for multiple video compression algorithms, video servers and off the shelf, hard disk-based and tape library archival devices. In such an environment, when technology migrates, the customer is not tied to a particular manufacturer.
In a seamlessly integrated system, video can be linked to alarms or events generated by any third party field devices in the enterprise, including intrusion detection, fire, access, asset and any other controllers. A seamlessly integrated system offers centralised management, administration, monitoring and reporting. Its single, centralised database contains all the information that, in a nonintegrated environment, would be distributed among multiple databases. The open architecture design enables a system operator to view alarms and related video simultaneously on the same screen and in realtime. These features provide a complete picture of what happens, where, to whom and when within the enterprise. This information can be critically important evidence when a problem or security breach occurs.
A case in point might be the theft of an employee credential (ie badge). When the credential is reported stolen, the system's centralised database is updated to reflect the new credential status. A subsequent attempt to access the facility using the stolen credential generates an alarm, which denies the thief access and initiates capture of digital video of the access attempt. A guard located in another building or on the other side of the world views both the alarm information and the live video footage simultaneously on the same screen, and can respond immediately. The video clip can be stored and archived for later retrieval.
In another example, an employee carries a notebook computer from Area A to Area B within a building. As the person moves through the doorway, portal readers register the employee's credential information, as well as the notebook's RF asset tag number. The system checks the integrated database to verify whether that employee has permission to enter Area B at the time, and whether the employee has authority to move that notebook from Area A to Area B. If the person has such authority, access is granted to Area B. Otherwise, the system generates an alarm, access is denied and video footage is captured of the person attempting to remove the notebook. The video clip can also be exported and forwarded via electronic mail to management and security personnel.
These two very simple examples illustrate that digital video technology can be an invaluable tool when seamlessly integrated into a total security solution. It offers flexibility, cost effectiveness, centralised administration and monitoring, and instantaneous retrieval of vital information.
For further details contact Phil Mailes, Lenel Systems International on tel: (0944) 1932 874773, fax: (0944) 1932 874551, e-mail: [email protected]
About the author
Rudy D. Prokupets is Chief Technology Officer and Executive Vice President of Research and Development at Lenel Systems International. He holds a MSc degree in Electrical Engineering, and a Masters degree in Applied Mathematics. He is a frequent speaker at industry trade shows and seminars, has been published in books and numerous trade publications, and holds several patents.

© Technews Publishing (Pty) Ltd. | All Rights Reserved.