

Electronic security and information security as individual, non-integrated sub-systems can create security gaps in your organisation. It is commonly acknowledged that 30% of intrusions within a company's computer system are from outside hackers; 70% are from people associated with the company, so finding the common ground where physical security and IT security systems meet will undoubtedly bring significant enterprise-wide benefits by leveraging areas of similarities within the two domains.
Identifying and exploiting these similarities can bring substantial cost-savings while streamlining your security policies. In a typical business environment, physical and IT security meet in any number of ways, including:
* The use of 'doors' to control access to restricted areas (physical and logical).
* Administrators managing PC-based network applications.
* The use of credentials (physical badges or PIN/passwords).
* Same users: company employees, contractors, visitors, etc.
* The same person to access a restricted area in the facility is accessing a restricted area in the network, PC and other IT applications.
* The use of a common network infrastructure.
Whilst not routinely done, integration can be as simple as sharing common cardholder data between physical security and IT systems. Integration can extend far beyond this, to tighter seamless integration with many of the sub-systems shown above, such that events in one domain create actions and alarms in the other domain.
Solutions through integration
Of course the real beauty of integration is that a single solution can be utilised for managing people, assets and information. Lenel has pioneered this market for convergence in the security industry, most notably with its intro-duction in 2002 of OnGuard OpenIT, which has long offered an advanced application integration service that allows realtime, bidirectional data exchange and seamless integration between OnGuard and external IT applications. As the diagram (Figure 1) shows, OpenIT is designed as the foundation for many of the integration points between physical and IT security.
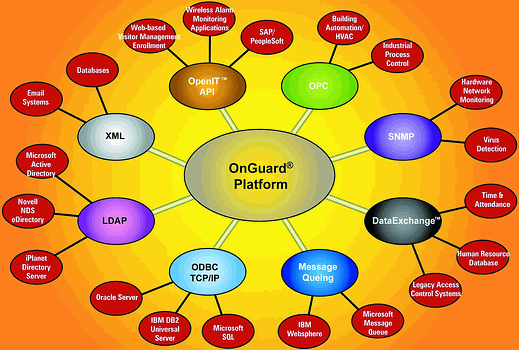
This flexibility allows many unique business applications to be solved by leveraging existing available data. The integration possibilities are endless. Some of the more important areas include:
* LDAP/active directory linkages.
* Integration with SNMP.
* Digital certificate management services through PKI integration.
* OPC - OLE process control, and more.
LDAP application examples
Using OpenIT type solutions, system administrators can develop scripts and applications that allow events in one domain (security or IT) to cause appropriate actions in the other. For example:
* Login access (activation of LDAP accounts) to computers in a lab can be controlled based on whether that person's card was used to access the lab. If they did not use their card to access the lab they will be denied access to computers within the lab.
* Leaving the building by swiping the person's credential at a building egress reader will automatically deactivate the person's LDAP account; thus, preventing unauthorised use of that account.
SNMP application examples
Using SNMP, system administrators can automate delivery of alarms to e-mail systems, pagers, PDAs, etc; when any number of network-based activities occur, including notifications to the security solution of:
* A DDOS attack on the corporate network.
* A virus detection on a PC or LAN segment.
* An access denial into the company's virtual private network (VPN).
PKI application example: smartcards
Administrators can now issue smartcard logon certificates (which provide authentication) from a single cardholder enrolment workstation. Employees do not need to type CTRL+ALT+DEL and remember a user name/password. They simply insert their smartcard into a smartcard reader attached to (or integrated into) the keyboard or PC, and they are prompted for their personal identification number (PIN), thus providing a more secure way for system logon. Removing the smartcard from its reader will automatically log out the existing user.
OPC - application example
Using an integrated security solution as an OPC Client, administrators can automate their response procedures based on an alarm generated from their building automation system. For example, in a multitenant property environment, where the tenants are not managing or monitoring the activity at the premises, property managers can be notified if there is a change in the room temperature in a server room. An automatic page or e-mail can be sent to the officer in charge of the area so immediate action can take place. The system can link video to provide live surveillance, and in sophisticated environments, where wireless networks are in place, it can be sent to the officer's wireless PDA device. Because the system provides a comprehensive audit trail, critical events can be quickly investigated; thus, a consolidated report could be run showing all activity in the server room including all credential holder activity prior to the alarm.
The bottom line: finding the common ground where physical security and IT security systems meet will bring significant enterprise-wide benefits by leveraging areas of similarities within the two domains, and identifying and exploiting these similarities can bring substantial cost-savings while streamlining your security policies. In other words, the bottom line is that true convergence will have a positive impact on your bottom line.
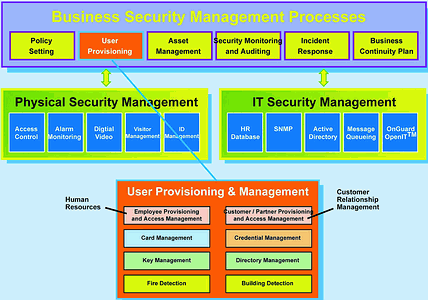
The value of true integration with IT convergence
* Centralised physical and logical identity management.
* Unified security policies for physical and IT systems.
* IT and security departments maintain control over their domains.
* Eliminates the need for multiple credentials/tokens.
* Decrease chance for errors during enrolment/termination.
* Automate business processes.
* Reduced total cost of ownership.
* Comprehensive audit trail for investigations.
* Increase return on investment.
* Realtime monitoring of disparate systems using one user interface.
For more information contact Phil Mailes, Lenel Systems International, 0944 1483 815230, phil@lenel.com, www.lenel.com

© Technews Publishing (Pty) Ltd. | All Rights Reserved.