
Many schools in South Africa may have considered biometric access control as a means of combating truancy and ensuring learner safety and security.
In the UK, an estimated 30% of all schools are using biometric access control. Although concerns have been raised over privacy and the collection of fingerprints into national data sets, the Data Protection Act (1998) of that country allows schools to record fingerprint biometrics without the consent of the parents.
In South Africa, however, the almost to be promulgated Protection of Personal Information (POPI) bill prevents the collection of personal information without the written consent of the individual, or that of a legal guardian in the case of minors. (See section 25 – Prohibition on processing of special personal information.)
This would imply that, even if a school’s governing body agrees to the implementation of biometric access control at a school, the individual learners would still be able to reject this notion through the refusal by the parent/legal guardian to record the learner’s biometric information.
It is thus imperative that schools, and governing bodies in particular, manage the decision-making process around biometric access control in such a way that the potential legal stumbling blocks are taken care of as early as possible.
Preferred biometrics?
From an affordability, accuracy, and usability perspective, the primary options for biometric access control at schools would be fingerprint, palm vein, and face metrics.
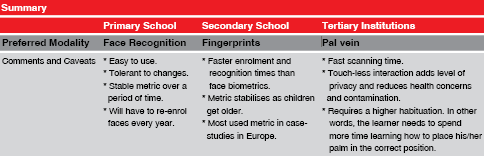
Fingerprint biometrics is by far the most popular, but does suffer from a few practical limitations. Young children, up to the age of 8 years, have notoriously unreadable fingerprints. In March 2009, the European Parliament has consented that children under the age of 12 would not be required to have their fingerprints recorded as part of their visa applications. This would thus exclude fingerprint biometrics from use in primary schools.
Another challenge with most fingerprint biometrics, is the vulnerability towards ambient temperature. Although a device may have operating specifications that are way below zero degrees Celsius, any person subjected to an outside temperature close to that temperature, even for short periods of time, will undergo physiological changes where blood vessels contract to retain heat, and in doing so, altering the ratios and distances of various minutiae points on his/her fingers.
In short, it has been noted that fingerprint biometrics can be challenging if kids have to walk to school in cold winter months.
Face recognition is another metric that is gaining in popularity and affordability. From a usability perspective, face recognition has the advantage of not having to put your school-bags down in order to present a hand/finger to the identification device. This can be a convincing argument in extreme cold conditions.
The disadvantage of most face-recognition systems is scan and processing time. Should a child need access granted to the school premise, he/she needs to walk up to the face-scanner, stay immobile for at least 2 seconds, not say a word, not moving, not making faces, and not talking on his/her cell phone. Although this is an easy feat for adults, it can be quite a challenge for juveniles and teenagers alike.
Palm vein biometric systems make use of infra-red technology to create a profile of the subcutaneous veins of a person’s hand. This is a relatively universal metric that is as easily recordable for toddlers as it is for grown-ups. Recent trials with contactless palm vein biometric systems have shown promising results. With identification speed of less than 1 second, and a price-tag that competes favourably with quality fingerprint scanners, this technology would be the author’s preferred technology of choice when implementing biometric access control at primary and secondary schools.
Costs
In general, the biometric technology is the least of your concerns when it comes to implementing access control at a school. At the top of the list of expenses would be the purchase and installation of perimeter control. Without proper fencing, no access control system would be worth anything. Similarly, turnstiles (devices used to allow one person through a gate at a time) can be quite costly and one would normally need a number of these to allow acceptable entrance rates into/out of the school premises.
A general rule of thumb for biometric devices would be to allow for a maximum of eight learners per minute through a turnstile. This means that if you need to grant access for 500 children onto the school terrain between 07:10 and 07:30 am, an average of 25 children would arrive at any minute during that time. We know that this is not the case though. Of the 500, 350 would probably arrive within the last 10 minutes before the school starts. To allow 350 kids access through biometric controlled turnstiles within 10 minutes, would require 3–4 turnstiles to be installed.
(Number of Learners: Children that need access to the school at peak times, spread over 20 minutes)
(Number of Turnstiles get calculated at an average access rate of eight learners per minute)
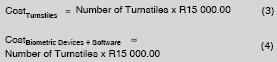
* The variance on pricing on turnstiles and biometric devices is large. These costs have been based on the average costs of reliable proven technologies. One may be able to get devices cheaper, but make sure that they are IP65 rated (water proof and dust proof).

© Technews Publishing (Pty) Ltd. | All Rights Reserved.