
Increasingly sophisticated and obviously well-planned physical or electronic breaches of supposedly infallible commercial or industrial security installations continue to create news headlines around the world. South Africa is not exempt in this respect and the current shared wisdom of IT and security professionals is that associated defensive strategies should assume and provide for the reality that attempted breaches – either internally or externally motivated – will be made.

Security officials in most organisations, regardless of size and specific operational risks, are increasingly faced with significant administrative problems. These problems are directly associated with the need to cost-effectively and efficiently acquire, store and subsequently retrieve essential security-related data and information. Organisations that choose to maximise the benefits of having readily available, properly structured and easily accessible data with responsibilities clearly defined, invariably create the ability to provide superior risk mitigation benefits for the organisation by avoiding data and information chaos.
Risk assessment and management
This article assumes that responsible security or risk executives have completed or are considering appropriate first-phase security risk assessments for their organisations and thereafter the second phase installation of well-considered and selected integrated risk management systems.
Modern risk management systems cater for the essential integration of all those components of an enterprise which can and do generate incidents from a variety of security risks impacting enterprise assets. These components can, for example, relate to physical, financial, employees, reputational, stock or IT related assets etc. These components can and do generate risk and losses via criminal behaviour, substance abuse, health and safety lapses, breaches of IT and data/information security policy, internal or external hacking or cyber attacks, labour unrest, general security issues, perimeter breaches etc.
Invariably, a well-considered risk management system provides for the installation of strategically-placed (overtly or covertly or a mix of both) CCTV cameras and physical access-limiting features protecting monitoring screens in a control room – either onsite but preferably offsite – which allow for immediate response procedures to be followed when an illegal incident is observed. Control rooms are usually allied with permanent onsite security guards with handheld communications equipment linking each guard to the others and to the control room. These onsite features are then supported by an external armed, rapid response team.
CCTV cameras are installed because they arguably provide the most efficient and cost effective surveillance tools available and can be installed in a wide spectrum of locations. Equally common, unfortunately, believed to be in as high as 75% of situations, is the fact that when an incident occurs, recourse procedures are typically found to be inadequate because the backup CCTV records have expired or been overwritten or not correctly filed.
Logging and finding evidence
Very often, if the incident record being searched for is historical, it cannot easily be found because of the frustrating and widespread occurrence of incidents being discovered some time after they occurred and no search or audit supporting evidence is available via, for example, a manual system comprised of a diligently and accurately completed logbook, which itself, when full and replaced, is correctly filed for rapid recovery.
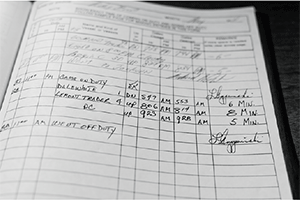
The obvious solution to the inefficient – even when well-maintained – manual logbook procedure is the now increasingly used electronic logbook. The electronic logbook is a database and search engine system which can be standalone or electronically linked to the CCTV camera procedures.
Security professionals managing CCTV control rooms, either in standalone situations or for several clients in one control room installation for cost-sharing purposes, are finding electronic logbook systems essential, especially when tailored in a bespoke manner to match specific client site requirements. This is because, to a significant extent, they avoid the inefficiencies and human dependency weaknesses of now outdated manual systems.
The primary purpose of an electronic logbook facility is to allow for passive CCTV systems to be made proactive or turbo charged. An electronic logbook is not a generic product. It is usually a platform which enables the rapid development of unique bespoke solutions for a variety of client sites, each with different security-related requirements. The bespoke data and information architecture is designed in conjunction with clients.
This design collaboration enables the creation of a personalised Integrated Knowledge Platform (IKP) for each client. By applying analytical data processing to the sourced information in the database, the client is able to identify and select key security features embedded in the information that can be used to mount effective and focused operations. The proactive features are enabled via the real-time online access and reporting features.
Customised IKP
The in-house IKP process enables clients to rapidly develop their own unique security data management solutions – such as investigations’ diaries and security occurrence record keeping, together with many other uses. Although the basic system and search engine is highly sophisticated, the bespoke version for each site is made incredibly easy for the end user to use. A key feature is an initial process to minimise misinterpretation on input and therefore avoid the classic ‘garbage in garbage out’ problem. Continuous data and information capture requirements are enforced by the bespoke design characteristics which prompt required inputs and which, for accountability purposes, log the identity of responsible employees concerned.
Each bespoke system not only stores all required data in a secure environment, but also enables the accurate and timeous recall of historical data at the touch of a button. The powerful search facility allows for the mining of historical data – via a cascading drill down capability – to the exact incident within a specific security category being sought, regardless of when it was originally reported and captured.
All captured records are stored indefinitely. Hard copy and/or online statistical reports are generated providing graphical representations of trends and patterns based on previously reported data and information captured. The use of heat maps and the storage of critical information such as videos, snap shots and voice clips can all be added, providing the user with additional tools to create and implement effective security measures based on actionable and timely intelligence.
Once developed, access to the IKP is typically made available to a select group of approved employees /gatekeepers in the client environment who are thus empowered to both access and encouraged to enter information from a variety of sources – not just CCTV cameras – on a daily basis. These gatekeepers are usually the only authorised individuals given access to the system. However, they do not automatically have overall insight to all the data and information inputted.
For more information contact Security Service Consultants, +27 (0)82 449 0317, howard@sscinfo.co.za, www.sscinfo.co.za

© Technews Publishing (Pty) Ltd. | All Rights Reserved.