
After experiencing a breach, organisations often realise they could have avoided a lot of cost, pain and disruption if only they’d had an effective incident response plan in place.
“Sophos has developed a framework for cybersecurity incident response planning that gives you the best chance at thwarting an adversary. These recommendations are based on the real-world experiences of the Sophos Managed Threat Response and Sophos Rapid Response teams, which have tens of thousands of hours of experience when it comes to dealing with cyber-attacks,” says Ross Anderson, Sophos product development manager at Duxbury Networking.
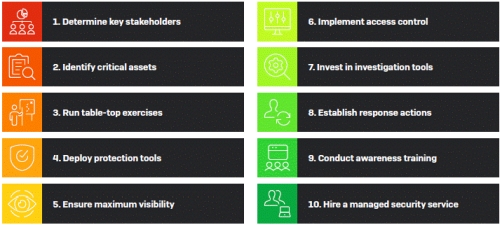
There are 10 main steps to an effective incident response plan.
Cyber-security incident response plan
1. Determine key stakeholders
Properly planning for a potential incident is not the sole responsibility of your security team. In fact, an incident will likely impact almost every department in your organisation, especially if the incident turns into a full-scale breach. To properly coordinate a response, you must first determine who should be involved. This often includes representation from senior management, security, IT, legal and public relations.
Knowing who should be at the table and involved in your organisation’s planning exercises is something that should be determined in advance. Additionally, a method of communication needs to be established to ensure a quick response. This should consider the possibility that your normal channels of communication (that is, corporate email) may be impacted by an incident.
2. Identify critical assets
To determine the scope and impact of an attack, your organisation first needs to identify its highest priority assets. Mapping out your highest priority assets will not only help you determine your protection strategy, but will make it much easier to determine the scope and impact of an attack. Additionally, by identifying these in advance, your incident response team will be able to focus on the most critical assets during an attack, minimising disruption to the business.
3. Run tabletop exercises
Incident response is like many other disciplines – practice makes perfect. While it is difficult to fully replicate the intense pressure your team will experience during a potential breach, practice exercises ensure a more tightly coordinated and effective response when a real situation occurs. It is important to not only run technical tabletop exercises (often as part of a red team drill), but also broader exercises that include the various business stakeholders previously identified.
Tabletop exercises should test your organisational responses to a variety of potential incident response scenarios. Each of these scenarios might also include stakeholders beyond the immediate technical team. Your organisation should determine in advance who needs to be informed when an attack is detected, even if was successfully defended.
Common incident response scenarios include:
• Active adversary detected within your network.
• Successful data breach.
• Successful ransomware attack.
• High-priority system compromised.
4. Deploy protection tools
The best way to deal with an incident is to protect against it in the first place. Ensure your organisation has the appropriate endpoint, network, server, cloud, mobile and email protection available.
5. Ensure you have maximum visibility
Without the proper visibility into what is happening during an attack, your organisation will struggle to respond appropriately. Before an attack occurs, IT and security teams should ensure they have the ability to understand the scope and impact of an attack, including determining adversary entry points and points of persistence. Proper visibility includes collecting log data, with a focus on endpoint and network data. Since many attacks take days or weeks to discover, it is important that you have historical data going back for days or weeks (even months) to investigate. Additionally, ensure such data is backed up so it can be accessed during an active incident.
6. Implement access control
Attackers can leverage weak access control to infiltrate your organisation’s defences and escalate privileges. Regularly ensure that you have the proper controls in place to establish access control. This includes, but is not limited to, deploying multi-factor authentication, limiting admin privileges to as few accounts as possible (following the Principle of Least Privilege), changing default passwords and reducing the amount of access points you need to monitor.
7. Invest in investigation tools
In addition to ensuring you have the necessary visibility, your organisation should invest in tools that provide necessary context during an investigation.
One of the most common tools used for incident response is extended detection and response (XDR), which allows you to hunt across your environment to detect indicators of compromise (IOCs) and indicators of attack (IOA). These tools help analysts pinpoint which assets have been compromised, which in turn helps determine the impact and scope of an attack. The more data that is collected – from the endpoints and beyond – the more context is available during investigation. Having broader visibility will allow your team to not only determine what the attackers targeted but how they gained entry into the environment and if they still have the ability to access it again.
In addition to these tools, advanced security teams might also deploy a security orchestration, automation and response (SOAR) solution that aids in response workflows.
8. Establish response actions
Detecting an attack is only part of the process. In order to properly respond to an attack, your IT and security teams need to ensure they have the ability to conduct a wide range of remedial actions to disrupt and neutralise an attacker.
9. Conduct awareness training
While no training programme will ever be 100% effective against a determined adversary, education programmes (that is, phishing awareness) help reduce your risk level and limit the number of alerts your team needs to respond to. Using tools to simulate phishing attacks provides a safe way for your staff to experience (and potentially fall victim to) a phish, enrolling those that fail into training, as well as identifying risky user groups who may require additional training.
10. Hire a managed security service
Many organisations are not equipped to handle incidents on their own. Swift and effective response requires experienced security operators. To ensure you can properly respond, consider working with an outside resource such as a managed detection and response (MDR) provider.
MDR providers offer 24/7 threat hunting, investigation and incident response delivered as a managed service. MDR services not only help your organisation respond to incidents before they become breaches, but also work to reduce the likelihood of an incident in the first place.
Data forensic incident response (DFIR) services are occasionally also retained after an incident to collect evidence to support a legal or insurance claim.
“When a cybersecurity incident strikes, time is of the essence. Having a well-prepared, well-understood response plan that all key parties can immediately put into action will dramatically reduce the impact of an attack on your organisation,” says Anderson.
| Tel: | +27 11 351 9800 |
| Email: | info@duxnet.co.za |
| www: | www.duxbury.co.za |
| Articles: | More information and articles about Duxbury Networking |

© Technews Publishing (Pty) Ltd. | All Rights Reserved.