

Readers of this edition of the Residential Estate Security Handbook will no doubt be aware of the constant focus on integration. Although it’s nothing new or revolutionary, systems on estates have been integrated for years, or could have been integrated, the need for integrated systems is more critical than ever.
As crime rises and criminals become more sneaky and inventive, the need for a comprehensive, integrated approach to security is essential. This not only means integrating technology, but technology and people as well.
Gallagher SA’s Morne Grobler says that in securing an estate, it is critical for systems to be integrated and managed from a single platform. “This unified approach of integrating CCTV, alarms, PIDS, access control, and visitor and contractor management empowers control room operators through enhanced situational awareness. By integrating all systems into a single security management platform, operators and administrators are trained on one application, and there is a single point for reporting, which saves time, creates operational efficiencies, and reduces cost.”
According to Grobler, the key requirements customers today have is a high probability of detection and low false alarm rate. No one wants to be constantly responding to false alarms that are meaningless, as it costs money and can cause alarm fatigue, running the risk of operators not responding to alarms when they should.
Brian Wynberger from Stafix Security Centres agrees. He says the ‘black screen’ approach is a good example of integrating offering usable intelligence. The operator does not have to watch multiple screens in the hope of spotting something, but only gets pop up alarms when an incident occurs, such as an electric fence being breached or a tripwire is crossed on a camera with analytics.
Focusing on intelligent perimeters
When it comes to integration, one of the most important aspects of estate security is the perimeter. However, there are many technologies and solutions aimed at securing the perimeter, all with their own merits, but integrating these systems into a management console will provide the best defence.
Effective defence of sites needs to start at the perimeter, Wynberger says. He notes that, while he (and Stafix) sells various solutions, he notes that the first step in perimeter security for estates is still a strong barrier. “A strong, high physical barrier such as a wall, palisade or mesh is vital, then intelligent protection can be added through technology such as monitored electric fencing.”

However, he warns that simply ensuring the perimeter is secured by fencing or some sort is not enough. “CCTV cameras provide a constant, watchful eye over remote sites and are especially useful over points of vulnerability. Adding intelligent video analytics then catapults the CCTV defence into a highly sophisticated security system. The benefits would include less fatigue on the operator as they can use intelligence for an intrusion or alarm trigger. Thus the operator is less likely to miss an event as opposed to merely watching a bank of displays with multiple cameras on screen.”
Grobler continues, explaining the value of an intelligent perimeter for estates.
• Firstly, quick intrusion detection and response times without the intruder being aware.
• Secondly, an intelligent perimeter reduces the need for guard patrols, saving money and minimising human error. It also improves emergency management processes and response times.
• Finally, and perhaps most importantly, an intelligent perimeter means there is less time spent responding to false alarms.
He says a secure perimeter consists of a four-tier approach – deter, detect, delay and visual verification – integrated into a security management platform. This integrated approach provides the control room operator with all the information associated with an attempted attack in the right format, at the right time, ultimately assisting with faster response times.
“Using a security management system, estates can have full integration between perimeter, intrusion, access control, and video management systems, as well as powerful reporting on detail such as fence voltage levels, operator use statistics, or specific zone alarm data.”
Solutions for the intelligent perimeter
“To help businesses operating in harsh environments, Gallagher recently introduced a new feature, Adaptive Thresholds in Command Centre from version 8.40 onwards, that allows the monitored pulse fence system to adapt dynamically to environmental changes,” Grobler explains. “Through the application of Adaptive Thresholds, sites can reduce false alarms while still ensuring the correct sensitivity for a highly secure perimeter.
He adds the company’s monitored pulse fence system consists of a grid of energised, high tensile wires that can be constructed inside a new or existing perimeter fence. The monitored wires detect unauthorised entry or exit into defined areas and trigger instant alerts.
Gallagher also has a range of additional products for this market. Grobler explains the company offers a range of advanced perimeter security solutions founded on two core principles: deterrence and detection.
Gallagher’s monitored pulse fence solutions include, F-Series Intelligent Fence Controllers, a fence energiser platform that can be deployed standalone, or as a fully integrated networked fence controller with full capabilities. Z10 Tension sensors, which measure the mechanical disturbance of a tensioned fence wire, raise an alarm when it is deflected during an attack. Z20 Disturbance sensors, which detect vibration or movement of the fence structure, generate alarms when a disturbance meets predefined criteria.
“Configured and controlled using Gallagher Command Centre, our solutions can be managed and monitored across multiple sites from one central location. Command Centre is the powerful software at the heart of Gallagher’s integrated security solutions, and intelligent perimeter protection. It is a centralised platform that gives you unparalleled control of every aspect of your site. Advanced multi-zone protection on single or multiple distributed sites is provided. Perimeters can be integrated with other security systems such as video management, intruder alarm or access control, alarm monitoring and signalling.”
The Site Plan Viewer in Gallagher Command Centre provides full screen, centralised site management visibility and situational awareness for all site buildings and perimeter, whether local or remote. Operators can easily see all activity on site and simply click on a site item to reveal the associated information, giving them the tools to manage any situation that arises and ensuring a fast, appropriate response to identified breaches.
Layered intelligent perimeter security
Shaun Williamson, also from Stafix Security Centres, adds that criminals have become more sophisticated and learned to work around basic high-voltage monitoring. This has resulted in the need for more layers of security in the basic fence structure.
“The JVA VM2 Vibration monitor picks up on digging under or penetrating through the physical barrier. Low voltage monitoring enables the fence to be monitored even when fence maintenance is being done and also monitors the perimeter in areas where the public may have physical access to the fence. Tension devices and tamper switches further pick up any fence tampering.
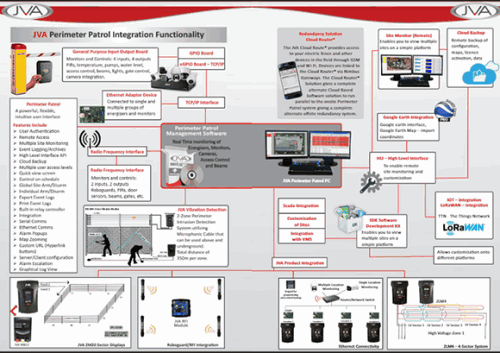
Other solutions Stafix offers for intelligent perimeters include the JVA range in which it supplies the software and hardware to zone and sector a security fence in high and low voltage. “We have fence vibration and dig monitoring and taught wire solutions to monitor for wire tampering. All of this integrates into the JVA management system.

“JVA Perimeter Patrol software which allows a visual map of the site, logs, voltages and coloured lines indicating the sectors or zones on the fence. When a zone or sector is breached this will be indicated by a red flashing line alerting the operator to an alarm. Furthermore, we have integrated Dahua IP cameras in the system to allow a screen pop-up focused on the given zone. A PTZ camera can also be used which will go to a predetermined pre-set focusing on the zone or sector.”
Integration capabilities
Since we started this article noting the importance of integration, we also asked Gallagher and Stafix for more information on the integration capabilities of their products.
Williamson says, “We are able to integrate third-party products with the Dahua Technology IP surveillance solution using API commands, as well as providing SDKs. The API commands are the same for almost all of the Dahua IP camera range. This makes it easier to do the integration as opposed to some manufactures that have a different API command set for each camera range.
“JVA has a HLI (High Level Interface) which allows for integration into other thirdparty products such as the Cathexis Vision IP Video Management Software suite. JVA is able to offer integration development in South Africa with our local engineers and technicians and also at an international level with the help of our engineers in Australia and the rest of the world.”
The power of Gallagher Command Centre allows extensive integration with other systems, with some integrations requiring optional licences, notes Grobler. This enables seamless interaction with third-party
perimeter products or extends the capabilities of Command Centre at the perimeter to provide greater site management value. Integrations include:
• Video integrations.
• Dynamic exit zoning.
• Regulated zones reporting.
• Fatigue and exposure management.
• Visitor management web service.
• ASCII interface.
• Mobile cardholder challenge.
• Competency module.
• REST APIs (Current REST APIs include, Cardholder REST API, Events and Alarms REST API, Inbound Events REST API, Status REST API, Overrides REST API) [Representational state transfer (REST) is a software architectural style which uses a subset of HTTP. It is commonly used to create interactive applications that use Web services. Read more at Wikipedia via the short link: www.securitysa.com/*rest].
• OPC (alarms and events).
• OPC (data access).
• XML import/export.
• Controller API.
• Active directory.
• Video Viewer SDK.
“If businesses want a custom integration or have individual requirements, we have a team dedicated to customer-led development,” he states.
An intelligent perimeter is definitely an integrated solution every estate should have in place, however, the choice of products that make up the solutions should be made carefully. Being able to integrate best-of-breed solutions is an ideal, but often not a reality when products are designed to only integrate effectively with same-brand solutions. As with every decision in estate security, doing your homework is key to seeing the security benefits of an intelligent perimeter.
| Tel: | +27 11 397 3507 |
| Email: | brianw@stafix.co.za |
| www: | www.stafix.co.za |
| Articles: | More information and articles about Stafix Security Centres |
| Tel: | +27 11 971 4200 |
| Email: | sales.za@gallagher.com |
| www: | www.gallagher.com |
| Articles: | More information and articles about Gallagher |
| Tel: | +27 11 543 5800 |
| Email: | malckey@technews.co.za |
| www: | www.technews.co.za |
| Articles: | More information and articles about Technews Publishing |

© Technews Publishing (Pty) Ltd. | All Rights Reserved.