

Most electronic physical security solutions are now network-based and incorporate multiple IoT (Internet of Things) devices. This means that they should be logically protected against exploits and vulnerabilities which could quickly escalate to far more serious system wide or even domain-wide risk. If you are serious about minimising risk for your customers and protecting your clients’ assets, then logical-physical convergence is a necessary step for all Internet and network connected systems.

Many electronic security companies claim to be experts in electronic security yet often their major nerve centre appliances and servers are accessible using the default web interface on port 80 and the default OEM user name and password via their guest Wi-Fi. Is this really true security? Do security industry captains understand the above three lines? If not, then we have a serious problem and questions need to be asked around why are they not costing and planning in expert ICT security specialist advice?
Is being competent in terms of selling electronic security solutions but failing to secure these systems against cyber attacks not ultimately opening more rabbit holes of risk? Dark web mining risk, privacy invasion risk, intelligence gathering for malicious intent, to name but a few.
Imagine surveillance cameras that cover the movements of sensitive or high-risk subjects and assets being maliciously and silently accessed by criminals. Safe? Definitely not.
By 2020, over 25% of identified attacks in enterprises will involve IoT, even though IoT will account for less than 10% of ICT security budgets¹. A worrying statistic, especially when one researches the devastating potential of cyber attacks via exposed or vulnerable IoT devices. Furthermore, Gartner predicts the number of connected things will reach 6.4 billion this year, hitting 20.8 billion by 2020 and IDC predicts that the global IoT market will have grown to $1.7 trillion by then. Are you seeing where this is going? The IoT industry is mushrooming and in the quest for revenue and marketshare we appear to be forgetting basic cyber risk mitigation and the fact that these devices are potentially creating gaping black holes in the Internet.
New vectors for attack
Top cyber-trend analysts go as far as saying that the next world war will be fought on the Internet, and leading cybersecurity thought leaders believe that nation-sponsored malware and backdoors have already been built into many OEM components at chip, processor and MCB level and are just waiting for the right time when the infamous button is pushed. While this may sound far-fetched, it only takes a basic Google search to find hundreds of examples online of attacks on key components and facilities.
In 2015, a couple determined they could hack a ‘smart’ sniper rifle and change its target. A few months later, the FDA issued an alert about a connected hospital medicine pump that could be compromised and have its dosage changed. Earlier that same year a cyber attack on a German steel mill left a blast furnace running with no perceived means of shutting it down.²
The Internet of Things (IoT) has the potential to create numerous benefits for businesses and consumers in terms of big data and new levels of automation, but it also creates new vectors for cyber attacks.
These days, objects as innocuous as your toaster or alarm clock can be collecting, using, or sending data. This creates a whole new world for hackers to exploit, and you’d better believe they’re doing just that.
If you are not convinced, simply type “IoT attack sewage treatment plant” into Google. The results will leave you viewing IoT differently.
Crosstalk between industries
Ten years ago, while working with an ICT company which was attempting to penetrate the physical security and intelligent building market, I realised how much terminology is shared between the ICT and the security industries.
Intrusion detection was the first word which I stumbled on which overlapped and had dual meaning. In the security industry I came from, the words ‘intrusion detection’ had always referred to burglar alarms and peripheral components, such as detectors, contact relays and seismic sensors and the word ‘intruder’ had referred to a trespassing criminal who was gaining access to a private property without consent and with malicious intent. In the ICT industry, however, an intrusion detection system is an intelligent ecosystem of software, algorithms, devices and applications which monitor ICT networks and computer systems for policy violations and malicious network activity.
The next was the word ‘firewall’. Where I came from, a firewall was something the fire system techies discussed with the builders during construction site visits and project meetings and it had to do with delaying or preventing the spread of a fire. In the ICT world I soon learnt that a firewall was a network security system with intricate inbound and outbound traffic rules (not the spiet kop type of traffic), application filtering (not a Google Play Store type of application), port blocking (not the ship type), MAC address4 filtering (not the Apple one) and all sorts of other interesting propeller-head talk (above average IQ engineers whose conversation is so intellectually advanced that it flies straight over my head).
To be honest, there were many other examples which I stumbled on. Words such as switches, access control, access tokens and keypads to name but a few which have a dual meaning.
One of my then colleagues within the group, a great guy by the name of Jonathan Kropf, was heading up the computer hardware division. Jonathan was sharp as razors and extremely humble despite having a few million ZAR of specialists in his downstream reporting structure. He used to help me out whenever I was battling with a personal PEBKAC issue (Problem Exists Between Keyboard And Chair). I would call him and say, “Hey Jono – The guys are talking about a VPN certificate for the instance? We don’t have a certificate for VPN competency. What is that? Is it like a CPO for a VIP?”
He would normally laugh patiently and talk me through opening my Internet browser and typing in www.google.com and then typing in the question I was asking him, and say “there we go Mark, next time remember Google is free”.
Jonathan introduced me to their ICT security team who were tasked with the network and appliance security for their sizeable national client base. The ICT security team’s vocabulary was a whole new language. When I heard them discussing smurf attacks, grey nets, phishing, vishing and “Dee Dos” teardrop attacks, I gave up trying to understand for the time being and I glided quietly back to my safe zone of PIRs, NVRs, CCTV, RFID and PTZs.
I began to grasp, however, that there was an uncomfortable but sizeable and distinct overlap between ICT and traditional physical security. I realised that cameras, DVRs, NVRs, intrusion alarms, fire alarms and access control readers were all forming part of what was becoming known as the IoT or Internet of Things.³
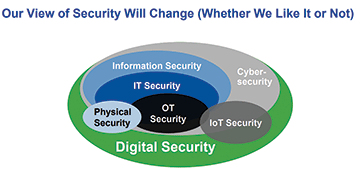
You can’t separate them
Fast forward to 2018 (more than a decade later). IoT becomes a very real core part of the physical security industry, experts are asking what will be done to plug the gaping logical security vulnerabilities around cameras, access readers etc. This has gone so far that The US House of Representatives has passed H.R. 5515, a bill that includes a ban on the US government’s use of Dahua, Huawei and Hikvision. This follows growing US awareness that Hikvision is controlled by the Chinese government (https://ipvm.com/reports/heres-what-really-sets-hikvision-apart, https://ipvm.com/reports/hikvision-influence), plus last year’s disclosure of Dahua and Hikvision security vulnerabilities.
The technology and innovation curve of convergence between logical and physical security systems has grown evermore vertical and the symbiotic relationship between IoT and physical security intensifies daily.
Some of the most interesting examples of logical and physical security convergence are found around identity management, policy management, BYOD frameworks and intelligent traffic management. As data leaks become a daily occurrence and data privacy is being discussed in every major technology company, encryption policies and methods also begin to overlap and converge with physical security.
A few examples of this obvious overlap are:
• JFK airport in the US has been testing fully autonomous ‘Patrolling Robots’ from Knightscope Technologies (https://www.knightscope.com). These robots have extensive IoT capabilities for biometric facial recognition, gas detection sensors, noise detection sensors for gunshots or distress screams, surveillance sensors and cameras, thermal vision, odour detectors and scanners, and the ability to broadcast recorded and live messages in the event of an incident. The main role of these Knightscope robots is to register any suspicious activity and alert the person responsible on duty. When they are on duty, they are moving around according to the GPS and lasers, which helps them measure and calculate distances and also LIDAR – light image detection and ranging. A robotic security guard. Operator login is managed by password and user name or biometrics.
• Drones/UAVs from SAPS airwing linked to shot spotter technology which enables high altitude UAVs to be dispatched to the location of a gunshot and track the perpetrators using GPS technology along with thermal and standard video feeds which stream live to ground support units and policing operations centres.
• Biometric and smartcard login systems for networks and workstations – A UID token management system which integrates with packages such as Microsoft Active Directory makes passwords a thing of the past and instead forces all passwords through a biometric fingerprint reader and manages the backend password cycling and updating automatically using maximum security policies. People cannot share, lose, forget or steal them. They simply sign on with a smart card or their biometrics. At the same time, a system like this prevents and deters fraud by creating Identity Chains that link users to their transactions, compiling an audit trail of who did what, where and when.
• An increasing amount of physical-security systems are IP-enabled, offering a way to merge with existing networks, or establish a separate IP network.
• A converged employee badge for physical access to buildings and access to computers is possible and sets a course in establishing a common identity-management system.
• Businesses, especially in retailing environments, can benefit from advanced IP-based video surveillance that allows for integration of findings about shopper traffic, displays and relative effectiveness of sales when combined with business data.

Advice for system integrators and installers
Some basic logical tips to help minimise the risk of smart device infection:
• Physical security systems are becoming technically sophisticated and it is wise to involve the IT department in their installation and management. Information gathered from physical security systems can often be merged as risk and threat factors with logical IT security.
• Reboot devices periodically – especially routers – and if viable, set the device to reboot periodically at quiet times. Ensure device redundancy/failover is present if the device is a key component to the security system. Rebooting will often get rid of malware already installed, however, in most cases it will remain therefore this should be merely one weapon in your arsenal.
• Understand the DMZ portion of your network and use it wisely to keep possible non-essential IoT culprits off the safe side of your network. If necessary, tier the firewalls with a double router configuration.
• Close ALL unused ports. If there is no option for this, consider implementing a secondary router/switch to manage this. For example, if you do not use Telnet (port TCP:23) to connect to the router then it is a good idea to disable it so as to close off a potential loophole to intruders.
• One of the safest and most foolproof weapons against cyber attacks is to blacklist all MAC addresses except those of devices which are authorised and allowed access to the system.
• Always change the manufacturer passwords at initial setup even if the device does not prompt you to do so. If you are running an intelligent system wide password cycling tool such as SuperSign, then integrate this into as many IoT endpoints as possible.
• Ensure you use complex passwords of at least eight characters long, including numbers, special characters, upper and lower-case letters.
• Check often for new firmware versions and patches and install as soon as possible. If feasible, set up an auto-script configuration to run update alerts from the OEMs listings.
• Don’t allow external network access to the device unless absolutely necessary.
Electronic security appliances and components are IoT devices and need to be more strictly regulated. This will put the onus on OEMs to ship IoT products which are designed around cybersecurity instead of purely around usability and revenue.
For more information, contact Terpay Group, +27 74 566 3663, [email protected], www.terpaygroup.com
1. IoT-OT and IT Security Convergence - Ruggero Contu - Research Director Gartner.
2. Conner Forrest for ZDNet – Internet of Things. The Security Challenge.
3. IoT– A term first mentioned by Kevin Ashton, of MIT during a RFID presentation he made to Procter & Gamble (P&G) in 1999.
4. Media Access Control address (MAC address) of a device is a unique identifier (UID) assigned to a network interface controller (NIC) for addresses. Not to be confused with an Apple MAC or a MacBook.

© Technews Publishing (Pty) Ltd. | All Rights Reserved.