

Providing security for hospitals involves more than the best choice of products and features—it also requires best practices.
Security and safety at healthcare facilities are important for both quality healthcare and public safety.
Hospitals and clinics are a safe haven for those in physical or emotional need, and increasingly seen as a place of refuge in the event of a large-scale emergency such as a natural disaster or terrorist attack. For these reasons and others, more and more people use hospitals as their first source for help. Hence, it is essential that healthcare security staff not only consider facility security and safety, but also take an interest in broader public safety.
By applying best practices there are many technologies that can aid a well-trained healthcare security staff in preventing crime and managing security incidents. The key systems of security are intrusion detection, access control, emergency communications, and video surveillance. If each of these systems is purchased separately, administration and training can burden a company or property owner. Intrusion alarms occur on one system, access badges are administered in a standalone database, and intelligent digital video technology runs on dedicated computer equipment. Each system requires service, maintenance, administration, and training.
By integrating these separate security systems under a flexible building automation system (BAS), hospital executives realise a lower upfront investment for a considerably more powerful security solution. Installation and training occur on a single system. Operational costs like administration and maintenance are also reduced. Component devices are used in multiple ways to trigger lighting, video capture, pan-tilt-zoom, higher video resolution or frame rate, door locks, and other aspects of building control. A single system enables greater flexibility to add security components that can be easily integrated into the overall system, keeping the cost of capital expenditures low, and requiring little additional training.
An independent study by Strategic ICT Consulting of a 13 470 m² building shows a system installation cost saving of 24% for an integrated BAS versus separate systems. And after installation, operations and life-cycle savings continue. Project analysis by Teng & Associates shows that training is reduced 33%, IT administration is reduced 82%, and the cost for changes, upgrades, and additions to an integrated system are reduced by 32%. These operational figures are based on experience and measurement, and clearly demonstrate the value of an integrated BAS.
Healthcare security issues
Hospital security departments and staff are especially challenged to provide safe environments for employees, patients and visitors. Hospitals, by their nature, are designed to be open and accessible to the public, which means street crime and other dangers can easily enter through hospital doors if not properly protected.
According to Bureau of Labour Statistics data for 1993, workers in the health care field experienced the highest incidence of assault injuries. One study found that 82% of nurses surveyed had been assaulted on the job, 56% had been assaulted in the year prior to the survey, and many assaults go unreported (Erickson and Williams-Evans study, 2000). The same study shows that the greatest number of assaults (25%) occurred in emergency departments. Medical equipment, supplies, and controlled substances can also be targets of theft; and hospital patients, visitors, and staff can become victims of purse snatchings and muggings.
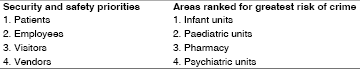
A survey conducted by the American Society for Industrial Security (ASIS) determined that effective security has become a part of the everyday operations of many healthcare organisations, regardless of size, location, or type of hospital. Security issues and concerns are identified and addressed daily by senior and middle management. Top-ranked security concerns are shown in the table.
The challenge of the bottom line
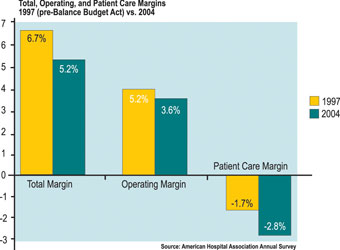
Even as administrators are actively addressing safety issues, hospital executives are challenged by stringent budget demands where shrinking margins can impact investment in security technology (see Figure 1). Hospitals must serve the uninsured public and spend money implementing systems and procedures that allow them to conform to government regulations, such as the Health Insurance Portability and Accountability Act of 1996 (HIPAA) and the requirements of The Joint Commission on Accreditation of Healthcare Organisations (JCAHO) and Centers for Medicare and Medicaid Services (CMS).
In a competitive market, hospitals also face the private healthcare practices of nearby clinics and independent doctor consortiums, which can siphon away high-margin services such as minor surgeries, ultrasound, MRI and CT scan, and recruit staff to a more secure and safe environment. And on the revenue side there is additional pressure from the diagnosis related group (DRG) reimbursement schedule, which regulates how healthcare providers can charge for services.
In this financial environment, it is essential that healthcare institutions seek to proactively and continually reduce operating costs and limit liabilities. Many hospitals are turning to technology to help make the security programmes more productive and effective. New integrated solutions for security, facility and data management enable healthcare institutions to both reduce costs and improve the safety at their facilities.
Moving beyond basic security technology
Regardless of the size of the healthcare facility, its location or the level of security risks that need to be addressed, there are essential components of an electronic security system. These include intrusion detection, access control and visitor management system, and video surveillance. These three systems, in the hands of competent and capable security staff, apply technology effectively to reduce crime and protect people and property. We will examine each system individually, and then in combinations to demonstrate how integrating security into the building automation system leverages these systems in multiple ways, increasing security and reducing operating and training costs.
Intrusion detection
Simple intrusion detection is probably the most familiar concept of security to most people. Intrusion detection involves the use of door or window contacts, glass contacts, or motion sensors, in combination with some type of audible alarm that sounds when a person has forced entry into a building or room. An alert is sent to the police or security station to notify authorities of the time and location of the incident. Security officers respond in person to evaluate the situation.
This method of incident response can be adequate for detecting an event and quickly getting to the scene. But the effectiveness of the response at the scene and subsequent prosecution is dependent on several things: the proximity of security personnel to the incident; whether witnesses were present; the number of people involved; the seriousness of the incident, and other factors. Furthermore, with simple intrusion detection, there is little in place that would deter people from committing a crime in the first place.
More information would be helpful, such as captured details of the situation that could lead to proper response and identification of perpetrators, thereby reducing the likelihood that a similar incident would occur again. Door and window contacts, motion sensors, and other devices already in use for alarming can be put to better use to help gather this information by triggering other parts of an integrated security system.
Access control
Access control is the means by which people are granted or denied access to restricted areas, such as clinics, operating rooms, labs, and parking garages. One of the largest security challenges hospitals face is how to secure a space that is intended to be not only a public environment, but also an inviting one. This means that a balance between permissiveness and control is needed, not just using technology, but as part of the healthcare facility’s culture of security. For example, a hospital may have a sophisticated access control system with picture badges issued to every employee, and card readers, electrified locks, and cameras protecting every door. But a courteous employee can defeat all of these security measures by holding a door open for a ‘tailgating’ perpetrator. A good access control system can detect this, and issue an alarm to the security staff when it happens. Access control could be used to manage non employees – both vendors and visitors – using a ‘visitor management system’. It can also assist with after hours access to areas of the hospital restricting and controlling certain egresses. Also, a single card could be used both for access to the parking garages and hospitals, making it easier of the staff and physicians.
When used as a standalone system, card readers and other electronic access devices offer a cost-effective and flexible way for a hospital to control who has access to the various parts of the building, with the system recording who has gone where, and when. The sequence of operations is for the access device to trigger the door lock, entry is granted, and the event is recorded by the central system. But if a device can trigger the lock, why not use this inherent ability to trigger other security devices as well? As a standalone system, access control does its job, but does not fully leverage the connected sensors for broader security objectives.
Video surveillance technologies
Video surveillance has evolved significantly in the last several years. Older video systems needed banks of video tape for continuous recording, and required manual administration to swap tapes periodically during the day. Record keeping was prone to errors and finding specific incidents on tape was time-consuming.
Digital video recorders (DVRs) made significant advances in features and functions, taking advantage of fast computer processors and high density storage media to digitise, compress and record video from analogue cameras. Newer cameras today have embedded processors that enable video to be compressed within the device and transmitted realtime over IP networks to network video recorders (NVRs) that centrally manage video feeds from many IP cameras.
DVRs and NVRs have many advantages over older analog recording technology. Streaming video can be continuously recorded and discarded in cycles of days, weeks, or months if no security incidents occur. If an incident does occur, disk indexing and time-stamping make it simple to find video from a given date and time. In addition, because the video is digitised, it can be exported and distributed via e-mail or backed up on CD, DVD, or other digital media using common computer backup programs that are widely available.
Digital video surveillance is cost-effective and sold by many vendors in a highly price-competitive market. If purchased as a separate system to meet the needs of a security plan or upgrade, a DVR or NVR may be adequate for immediate surveillance objectives. But if this digital video recorder is integrated with an organisation’s access control and intrusion detection system (as part of the broader building automation system), the user improves surveillance and reduces the need for additional security personnel.
Integrated with access control, video verification, for example, allows a user to see live video as well as the cardholder’s picture when a given access card is presented at a reader. The security staff can verify that the person presenting the badge is the actual cardholder. Another example of video verification effectiveness occurs in identifying individuals who are ‘tailgating’ as noted earlier, when one person swipes their badge and gains access to the facility and another person follows them in without presenting their badge. The integrated system allows organisations to visually identify, verify and capture security breaches at access points.
Video analytics
The advent of video analytics brings additional flexibility and increased productivity of security staff that monitor many cameras or for a non-manned time it can send out alerts to other staff members using mobile devices to respond where needed. Video analytics is a technology applied in software that examines the video camera’s field of view for patterns of movement that match real-life events, such as falling, fence climbing, lurking, and triplines.
Video analytics provides a means by which the user can focus only on what is truly important, managing surveillance by exception events rather than trying to observe all events.
A DVR or NVR can be configured to only display a camera’s video if a specific event or alarm occurs. At a hospital for example, foot traffic in the evening past a closed pharmacy may be considered normal. But lurking video analytics software tracks people or objects, and can alarm on types of behaviour near the pharmacy door may be an indication that a break-in is about to happen. Video analytics can tell the difference. And additional alarms can be generated if video analytics detect more people in the video frame, which may indicate another level of security threat is occurring.
Integrating it all
Today’s access control and video surveillance systems can work together in an integrated BAS to provide an holistic solution for healthcare organisations, keeping intruders out of secure areas, limiting access to infant and paediatric wards, and remotely monitoring critical areas to reduce the risk of crime and security incidents. This is why more and more hospitals are increasing their use of CCTV as part of their overall security plan. Using an integrated system, security staff at a central monitoring station can view live images from surveillance cameras, control pan-tilt-zoom cameras, or search for video clips stored on digital video recorders (DVRs). When an alarm is triggered by intrusion or an invalid access card, the BAS can command the DVR to begin recording, display live video from a linked camera at the location, map the alarm location, and send an e-mail to an administrator all at the same moment.
CCTV cameras are an important surveillance component at vulnerable areas of a hospital, such as entrances, parking garages, pharmacies, and nurse stations. When a duress alarm is activated at one of these locations, cameras can be activated to survey the scene and monitor the emergency, and security personnel can quickly evaluate their response.
Asset protection is also becoming a high priority for hospitals. The hospital needs to track everything from PCs to wheelchairs, to PDAs and phones – not just for the value of the item but also for the data that could be located on it. They are more and more looking to RFID (radio frequency identification) and tagging technologies to assist in this. This system works in conjunction with video and access control to document the movement of assets.
For hospital administrators and security staff, integrating various systems in the hospital offers numerous advantages. Foremost, integration provides for reduced installation and operating costs because it eliminates component redundancy and allows staff to streamline operations. Furthermore, it reduces training and empowers system operators by allowing them to perform their duties more efficiently.
Integration can simplify the operation and control of complex hospital systems, while enhancing security at the same time.
Benefits of integrating the security system with the BAS.
* A site-wide single-seat interface enables one person to be trained on multiple security systems.
* Security components become multi-use. A motion sensor can be used for lighting control during occupied hours, and intrusion detection during unoccupied hours.
* During design, flexibility, efficiency, and economy provide room for additional security expansion or integration at the lowest cost.
* Better response to occupant needs, offering patients and staff greater security and peace of mind.
* More information put to effective use, which gives hospital security staff solid ground to stand on for prosecution and proof of loss. CCTV records also aid law enforcement authorities in finding criminals.
* Vendor independence, allowing the customer to choose among best-of-class security products.
* Single-source responsibility, whereby one integrator is held accountable for the entire security system.
For more information contact Nico van der Merwe, Schneider Electric, +27 (0)11 254 6400, [email protected], www.schneider-electric.co.za

© Technews Publishing (Pty) Ltd. | All Rights Reserved.