
Comfort, safety and security in commercial buildings are not 'nice-to-haves'. They are essential to worker satisfaction and demanded for commercial buildings everywhere.
Architects, developers and building owners expect efficient, cost-effective solutions in new and existing buildings that provide flexible and integrated building information technology.
Building information management and control is expected to have lower cost installation and life cycle costs, self-contained information management systems and reduced risk.
Only when businesses understand the risks they face in terms of their building management and security systems will they be able to protect themselves against potential physical and personal damage or financial loss.
One precaution companies can take is to deploy electronic systems to help them manage their security requirements more effectively.
The office of the future is here
Systems are available that provide the scenario where an employee swipes an ID card to enter the building. Once the system knows he is at the entrance, the heat and electricity in his office are turned on and his computer is booted up. A window sensor will adjust climate control and ventilation when the window is opened during office hours, and then switch to an alarm system when the window is opened after hours.
A facilities manager monitors all building system activity and usage from a remote desktop PC, and is able to make adjusts on-the-spot, on-the-fly. The manager can be sitting in an office working, waiting for an electrician to call and announce that he has arrived at one of the company's buildings on the other side of town. He can watch him via a web cam connected to the Internet to verify that it is the right person and open the front door by a secret code entered from the computer.
Using a combination of biometrics, card reader and PIN code only employees authorised to access extremely sensitive areas are able to do so.
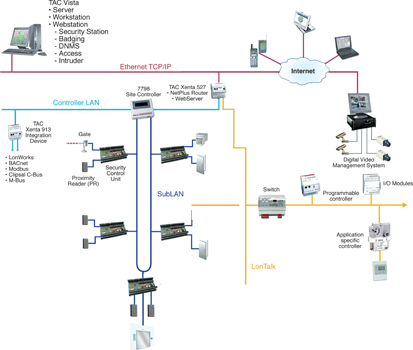
Building management
Buildings are controlled from one single user interface, accessed via the Internet. It can be taken a step further with the company not needing to install software on their site, where it stands the risk of being tampered with.
When investigating your security partner, ensure that the solutions they provide can help you to secure your facilities through such means as alarms on a need-to-know basis, dynamic event and alarm views, powerful event and alarm filters, anytime, anywhere access, using industry-standard technology and providing administration and reporting facilities.
They should be able to offer a broad range of security devices and systems, including, comprehensive access control, user and card management and optional video badging.
The ideal partner should be able to offer a complete, integrated building management solution that goes over and above managing all of the facility's environmental systems and gives the capabilities to keep your people safe and your buildings and assets secure.
If you take a single, integrated approach to building management and security, each system leverages from the other and gains power and functionality by being part of a total approach to building operations.
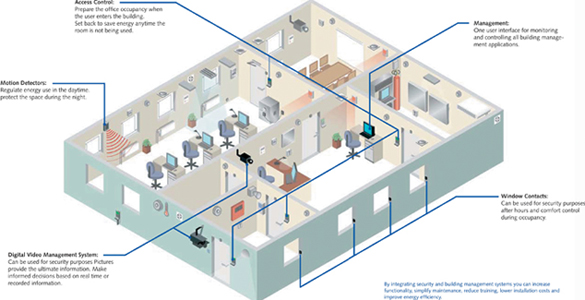
Importance of integration
It is important that the installation has a common presentation system for both building management and security functions. It should provide a single workstation environment for the design, configuration, management graphical user interface, and alarm handling for both HVAC and security solutions.
A common presentation system keeps operators focused, reduces training time and cost, and cuts overall cost of ownership. An alarm and event presentation system should bring together information from all different protocols and controllers attached to the system and present them in a single, consistent interface for user interaction.
A security solution should manage and present varied alarm and event data in a consistent way, permitting many different solutions to be managed by fewer operators, with less training. Without doubt, consistent alarm presentation improves response to events.
The user management system should be purpose-designed for typical security operators and be intuitive and easy-to-use, taking into account the differing levels of skill among operators, and allowing the operator presentation to be tailored to fit the needs of the specific user.
Only a limited amount of user intervention should be needed to establish devices on the network and configuration should be intuitive and simple. When you add a device to your device list, the rest of the set-up process should be primarily automated.
The right security solution should enable comprehensive access control and well designed functions that permit intruder detection monitoring to be established where needed. The open protocol and multiple secondary protocol connections should mean that interfaces to such systems as fire detection systems through Modbus are easy to achieve.
Bottom line - an improved ability to coordinate operations and optimise complete building performance including security. Further examples of the advantages include setting correct temperatures, lighting levels and security levels based on who enters or leaves areas or buildings based on integrated security detectors. In case of intrusion alarm, the system can use the BMS to turn on the lights in the relevant areas and take other action to heighten security and alert officials.
Window contacts can be used for multiple purposes - for security during off-hours and for zone control of heating, ventilation, cooling and lighting when the building is in use.
Security benefits
Having the intrusion alarm system integrated with individual zone control in every room enables building owners to track what has actually happened by utilising the alarm log on all PIR detectors, regardless of whether they belong to the security or the BMS system.
The communication system can run on the building's administrative TCP/IP network, so there is no need for separate communication bus cables and protocols. This simplifies daily operation and provides flexibility for future building changes and expansion. Workstations can be easily connected to any network socket, and Web interfaces can be set up on the users' PCs wherever there is a network connection.
Without doubt, intelligent buildings are the future, but companies investigating upgrading their security systems should not be put off by believing that they can only implement these systems in new buildings. Old buildings can also be made much more effective, with the right solution.
For more information contact Riaan Olivier, Schneider Electric South Africa, +27 (0) 11 254 6400, [email protected]
| Tel: | +27 11 254 6400 |
| Email: | [email protected] |
| www: | www.se.com/za/en/ |
| Articles: | More information and articles about Schneider Electric South Africa |

© Technews Publishing (Pty) Ltd. | All Rights Reserved.