
At some point, everyone talks about security. The question is, do you have a picture in mind when you think about security? For most people, security is only hardware, which includes a camera system, an alarm system, beams, a guard, or even a dog on the property. Close to 90% of all RFQs, tenders, or quotes for security are only for security hardware, but hardware is only one security component. Many other factors must be in place to call it security and for the solutions to function efficiently.
You are not wrong if you think about these items, but that is precisely what they are; items, mere building blocks of the security bigger picture.
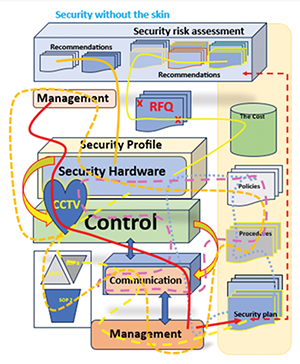
When you think about a human being, you automatically think about arms, legs, a head, a torso, etc. But if you think about it a little more, you will know that there is much more to a human being than a body. Security is the same.
Let us say we take a human body and pull the skin off. If you have never seen this before, I can assure you that it is not a pretty picture, but this allows you to see everything that is kept inside by the skin. In Figure 1, we have ‘pulled security’s skin back’. It might look disorganised, but we used different colours to differentiate between the various definitions.
Starting at the beginning
When it comes to security, we start with a security risk assessment. You should follow this process before making any security-related decisions or purchasing any security hardware or software. Essentially, this process tells you how to eliminate your security risks.
You will see in the illustration that you will get recommendations from the security risk assessment. From there, you will get the RFQ process and the costing calculations. The hardware is sourced once the assessment is done and the recommendations are approved. Keep in mind that each section within this illustration has its own connections to make everything function at an optimal level.
All the lines going from one segment to the next can be compared to the arteries in the human body. These lines signify data, connections, information flow, and the like. If there is one mistake that most people make when it comes to security, it is to skip the first and most crucial step, a security risk assessment.
When you look at the crime stats, you can see that most security structures are based on guesswork. No facts or research support security decisions.
The second biggest mistake everyone seems to make is forgetting about the network. A security network is a collection of network cables linked together or connected to an electronic device that allows security data to flow from one point to another. Today, wireless connections are often used instead of cables, but the network is still a critical component.
There are two security networks. One is depicted in the illustration, and the other is visible inside the sections control, management, security profile, etc., where everything is connected and intertwined to make it work.
In the illustration, you will note that management is connected to all the other aspects of the security structure. Management has different components, including control, hardware, the security plan, communication, processes, policies, etc. Control and communication are directly linked, as there cannot be any control without communication. In line with this, you will note that management and communication, along with policies and procedures, are related.
The security plan is directly linked to the risk assessment as the solutions are derived from identifying the security risks.
A best guess approach
Now, when you look at the illustration and remove the risk assessment part, which is the case with most security structures, you will note that there is no research and no information on what the solutions could be based on.
The risk assessment and recommendations are the research required to establish which security solutions will work to eliminate the risks. The risk assessment is where everything starts; it provides the guidelines on understanding and approaching security and what hardware will eliminate the opportunity for crime.
Also, when you take control out of the security equation, you will see that everything else will fall apart and that there are just too many loose ends.
Most security companies and structures have no standard operating procedures (SOPs). For more than 30 years, people have used the good old copy-and-paste method for SOPs. People do not even know the difference between the three types of SOPs that are used today.
Without a SOP, you do not have a security plan or any form of control or communication. Removing the policies and procedures further causes the entire system to crash and burn as policies speak to the hardware, which speaks to the control which is connected to communication and management.
We have done multiple assessments where several of these components were absent, which was evident in the security structure’s output value. When even a single item of the security structure is missing, your security will fail.
There is a reason we say that a golden thread runs through the entire security structure. Everything is linked; one security section cannot work without another preceding it. You cannot remove one section without affecting all the others. It is like an intricately woven tapestry. If you cut a single thread, the entire tapestry will unravel in time.
As mentioned, each of these illustrated sections has multiple facets that must work together to function. For example, all the different types of hardware, from the cameras, the property line, the access control measures to the alarm system, and everything in between, also need to be able to communicate.
Furthermore, when all the hardware communicates, the information must go somewhere. This is the control.
Command and control
In some organisations, it is called a control room. The control must ensure that the information is filtered to the correct people to take action where needed. This forms part of the policies, procedures, and, ultimately, the security plan. It is important to remember that you must have SOPs in place to have control. This comes from control and management, which form part of communication, management, instructions, policies, etc.
Can you see all the connections? Can you see that you cannot simply remove something and expect the system to continue functioning? Be that as it may, we seem to achieve the impossible in South Africa. We remove several of these sections and expect security to work. As you can see, when you look at the crime statistics of our beautiful country, it does not work.
When we conduct a security risk assessment, we always hope to find all the sections present. However, this is hardly ever the case. What does it mean to be in control of your security? I can explain it in detail, but it will be a 300-page document.
In short, being in control means that you know what is happening where at any given time, and that you can act when action is required.
What does communication mean?
Communication is not just one email or a phone call. It goes much further than that. Every aspect of security needs to be able to communicate, whether it is communication between hardware and software, hardware and a human being, human and human, it does not matter.
Without communication, you will not have any policies or procedures, which essentially means that you will not have a security plan.
If you want to know whether your security is on par, take the illustration, follow it step by step, and identify the items present within your security structure. This will give you a good indication of where you are in terms of adequate security measures.
Furthermore, aspects such as the master copy, control registers, maintenance, and so on are also part of control and management. Although it has not been included in the illustration, ensuring that it is part of your structure is vital. About 12 vital control registers must be in place, but hardly ever are. Also, training is essential and forms part of management, control, and procedures.
Seeing the heart of security
You will see that we included a heart in our diagram. It is not there for decorative purposes, and the location of the heart is also essential. The heart represents the control room, in other words, the information centre. This is where everything is brought together. Whether you have a big corporate company, a small business, or a home, it still needs a heart. It requires an information centre where all the data and information are filtered into and out again to the right channels.
CCTV cameras represent the eyes, and the PTZ cameras are the neck of the ‘security body’. So many companies try to run their security structures without a heart, and this never works. Just like the human body cannot function without a heart, a security structure cannot function without a control or control room.
Every aspect of security runs through the heart, which is why it is the most critical aspect of security.
The human body, like security, requires a brain to function. This is where artificial intelligence (AI) comes in. AI, like everything else, must be controlled and understood. Uncontrollable AI can complicate security; this topic will be discussed further in a future article.
To put the vast network of a security structure into perspective, the illustration contains about the amount of information similar to the size of a needlepoint on an A0 piece of paper. The rest of the paper must still be completed.
In the middle of security, two forces are vital in any security structure, whether talking about a small property, business entity, or large corporation. These forces are the security managers responsible for balancing the security structure.
| Tel: | +27 87 148 8615 |
| Email: | [email protected] |
| www: | www.alwinco.co.za |
| Articles: | More information and articles about Alwinco |

© Technews Publishing (Pty) Ltd. | All Rights Reserved.