

Best practices for secured access control in stadia
Patrick Ronan is currently the lead drafter of the legislative task team responsible for the drafting of the `Safety at Sports and Recreational Events Bill', which falls under the auspices of Sports and Recreation SA (previously known as the Department of Sport and Recreation). This draft legislation flows, in part, from our Government's desire, armed with the final report and recommendations of the Justice Ngoepe Commission of Inquiry into the Ellis Park soccer disaster of April 2001, to ensure that our citizens, especially our youth, are not exposed to unnecessary safety and security risks when attending sporting and recreational events. The draft legislation was also actuated, in part, by SA's successful bid process to host the 2010 FIFA World Cup. The draft legislation - which is not yet in the public domain - has been circulated to identified state, provincial and local authority as well as certain private sector safety and security stakeholders for input and comment during the legislative drafting process. Ronan believes that this type of legislative drafting process by Sport and Recreation SA (operationally headed by Prof Denver Hendriks) is a very positive and progressive approach by a government department. It has provided relevant public stakeholders with an insight into what will be a landmark piece of legislation at a stage prior to when one normally has sight of such legislation ie, when it is first published in the Government Gazette for general public comment.
Proper secured access control to sports stadia and recreational venues, the subject matter of this article, will be one of the specific areas of focus in the new legislation. Significant shortfalls in this critical aspect of major event safety and security were highlighted in the Ngoepe Commission of Inquiry.
Ronan spoke to Lynne Larsen about certain best practices for secured access control in stadia. This is what he had to say:
From a safety and security perspective, South Africa's internationally recognised ability to stage incident free major sporting events is a well documented fact. The safe and secure hosting of the 1995 IRB Rugby World Cup, the 1996 CAF African Cup of Nations, the 1999 IAAF All Africa Games and the ICC Cricket World Cup ('CWC') SA 2003 bear clear testimony to this (the pictures that accompany this article are of the security at this event). This ability, in part, is drawn from the 'hard-nosed' safety and security lessons learnt from our unfortunate pre-1994 socio-political history. When South Africans from both the state and private security sectors put their minds to it, we are right up there in terms of, in particular, secured access control, to major political, socio-economic, sporting and recreational events. Ronan states that incident free nature, from a safety and security perspective, of these and other major events such as the Commonwealth Heads of Government Summit of 1998, the UN Conference against Racism in 2001 and the UN World Summit on Sustainable Development in 2002, has created a significant amount of positive international media interest and comment. The planning and roll-out of the safety and security operation and secured access control procedures mounted by the State Security Services, and in particular the SAPS, during the UN World Summit on Sustainable Development, were world-class, a fact publicly acknowledged by the UN General Secretary, Kofi Annan, in his report on the conference.
Ronan believes that the 2003 Cricket World Cup was the most successful local example to date of an integrated approach to safety and security delivery at a major event by the State and the private sector. "It has certainly laid the basis of a solid platform upon which the safety and security planning and delivery for 2010 can be based." The safety and security operation during CWC was jointly co-ordinated by a multidiscipline state and private sector security directorate (which was chaired by Ronan), and whose members included director Ben van Deventer, a major event safety and security specialist of the South African Police Services; Randall Howard, the general secretary of SATAWU and EXCO member of COSATU; Mzwandile Simon, a leading trade unionist in the security sector, Peter Birch, a security and financial consultant and Rory Steyn, a major event close protection specialist.

According to Ronan, the single most important success factor of the safety and security operation which was mounted during CWC was the joint planning approach, integrated teamwork and harnassing of the respective safety and security strengths of the members of the security directorate. Ronan states that the safety and security blueprint (masterplan) for CWC was the most comprehensive safety and security plan locally developed for a major event to date. It was, inter alia, underpinned by tried and tested local state and private sector safety and security concepts, international benchmarked major event safety and security standards, a thorough domestic and international environment risk assessment, all of which was specifically tailored for South African conditions. Ronan states that a similar safety and security concept and integrated approach formed the platform upon which he based his approach when authoring Chapter 9 of the SA 2010 Bid Book (which dealt with proposed safety and security delivery for the 2010 event). This particular component of the Bid Book, together with information technology, received special mention and favourable comment from FIFA when they were assessing the various bids to host the 2010 event. A careful perusal of SA's 2010 Bid Book will reveal that safety and security was a common integrated thread throughout our Bid documentation, notably in secured access control related documentation relating to match ticketing, tournament accreditation, information technology (automated turnstiles and accreditation) and stadium design.

The basics of secured access control
There are a number of basic issues that one has to have in place before one even starts looking at the nitty gritty of the electronic hardware, software and other electronic screening apparatus used in secured access control delivery at major events.
The first aspect is proper legislation, based on sound and practical policy formulation, designed to specifically support, from a legislative perspective, the safety and security operation mounted during a major event. The reason why this aspect is receiving current Government attention is that there is currently very little in the way of legislation that supports police and/or private security and/or the event organiser in terms of enforcing proper policies and procedures relating to secured access control. There was an old piece of legislation that we used during CWC - the Control of Access to Public Premises and Vehicles Act, 1985 (Act No. 53 of 1985). While the application of the said legislation, following on from statutory declarations by the Minister for Safety and Security, did assist as far as the screening and searching of spectators by registered private security officers at access control points outside host stadia was concerned, it did not sufficiently cover other significant aspects relating to the enforcement of proper access control.

People often ask - why the need for such legislation? The trite answer is that those persons responsible for safety and security planning and delivery at major events have now, for example, to take into account changed world safety and security environment post 9/11. Notwithstanding SA's leading political profile in the world non-aligned movement, there are still risks. From a sporting perspective we have international teams, individual sportspersons and officials that tour and visit our country who hail from countries that have been closely aligned to the US, in the unfortunate aftermath of post 9/11. For example the stringent access control procedures applied to all persons entering stadia during CWC were welcomed by many of the tournament teams, their officials and supporters. You will recall that the Gulf War was already in full swing by the time the semi-finals stage of the CWC were being held.
In essence, legislation must set proper standards and must make it compulsory for, by way of example, different levels of access control procedures to be in place at a stadium of venue, dependent on the level of risk profile of the event to be hosted there. The risk profiling for an event - eg, low, medium or high - should be based on certain historical and current criteria which will have bearing on the projected safety and security at an event.
As mentioned earlier, sound access control policy formulation should underpin such legislation, even if enforcement of certain aspects of the legislation may have discretionary elements, such as legislation in the United States which deals with the prevention of 'ambush marketing' at major events. Another example of policy formulation is that relating to prohibited and restricted items ie, those items which spectators at an event may not lawfully bring into a host stadium or venue. Prohibited items are obviously items that are not allowable by law in any event such as narcotics, dangerous weapons, teargas, unlicensed firearms and ammunition. Restricted items, on the other hand, are those which spectators may lawfully be in possession of in everyday life but for the purposes of that particular event, those items may not be taken in to a stadium or venue. Examples of restricted items may be laser emitting gadgets, gas canisters, alcohol and the old South African flag.
Comprehensive and timeous safety and security planning is critical if safety and security delivery is to run smoothly during an event. For example the safety and security blueprint for CWC was almost three years in the planning. A key component of such planning is the running of pilot projects, which test proposed safety and security concepts, such as access control, prior to a major event. The running of a host international test tournament prior to the hosting of a soccer World Cup, in order to test the relative preparedness of a successful bid country, is a key requirement of FIFA. Take CWC for a practical example, timeous planning for the event allowed the organisers the luxury of testing of more stringent spectator access control procedures, foreign to many, on the general public. During the 2002 international cricket tours of SA - the Australian, the Sri Lankan and Pakistan tours, we were in the fortunate position to test, inter alia, our safety and security access control systems at certain host stadia which were earmarked as host stadia for CWC. This process allowed the event organisers to 'tweak' policy as far as access control procedure was concerned in order to ensure that whilst CWC would be secure it would still be 'people friendly'. It also served as a public awareness and education campaign as far as CWC was concerned - by the time the event arrived, spectators knew what they were and were not entitled to bring into stadia at access control points. This certainly assisted in speeding up access into host stadia during the event.
Which brings me to my next key aspect of proper access control - communication. Practical examples of the communication of access control protocols as far as the hosting of events are concerned is the running of properly planned and budgeted for communications campaigns prior to the hosting of events. Such campaigns, which should ideally be run across a broad spectrum of print, radio and TV media, can educate spectators as to what they are not allowed to take in a stadium, what the access routes to a stadium or venue are, whether there are spectator channelling procedures in place, the fact that they will be subjected to magnetometer screening, that their belongings will be screened by X-ray or searched, the fact that spectators should arrive early for an event to avoid delays at access and what the preferred means and access routes of transportation to the stadium are, etc.

Explanations of why access control policies and procedures have been introduced should also be communicated by event organisers to the public in terms of such communications campaigns. This ensures better for better buy-in and acceptance from the general public to such measures. Other methods of communication of conditions of access to stadia or venues involve the use of the rear of event or match tickets, the Internet and signage. Proper information signage, strategically placed throughout the precinct of a stadium, has proven to be a useful pre-emptive tool in reducing frustration at access control points. Signage positioned in a spectator parking area informing spectators that they cannot, for example, access a stadium or venue whilst in possession of a large cool box or alcohol will reduce frustrations at access control points.
The concentric circles of security theory
Access control procedures at a high risk international event, be it sporting or otherwise, which will attract a capacity crowd - should ideally see the application of the so-called 'concentric circles of security' in the precinct surrounding a host stadium or venue. This protocol, drawn from the successful experiences of safety and security operations mounted by the organisers and host countries of, for example, the Summer Olympic Games in Sydney (2000) has been successfully tailored to local conditions and has been successfully applied to major local events by, in particular, the SAPS.

This stadium or venue precinct access control policy basically involves the application of a filtering mechanism as spectators and event staff approach a stadium/venue. By its very nature the system can only be used in circumstances where there is a no sale of event ticket policy applied at the stadium/venue on the day of the event. The successful application of such a policy will, inter alia, ensure that by the time members of the public are immediately outside of the event venue, they are effectively in a 'sterile zone' as far as safety and security is concerned. What this effectively means is that everyone within the said sterile zone firstly has business at that stadium or venue on that day and secondly that both they and their belongings have been screened ie, they do not have any prohibited or restricted items in their possession.
A practical example of how the 'concentric circles of security theory' operates is as follows. Spectators approaching a stadium from various directions in its outer precinct pass a first checkpoint. At this checkpoint, ideally situated between the parking areas and the stadium, it will be ensured by private security officials that the person wishing to proceed further into the stadium precinct is the holder of a match ticket for the day or the holder of valid event staff accreditation. At a second inner circle access control point the match ticket or event accreditation is again checked and a thorough screening of the person and their belongings takes place. This process is normally effected by properly equipped private security officers, with police officials in attendance. Walk-through and handheld magnetometers and conveyor-belt type X-ray machines are used in support of this screening process. The sensitivity of such electronic security apparatus is periodically reset and calibrated during the event day to ensure consistency in the screening process. Once persons have cleared this particular checkpoint, they enter a so-called 'sterile zone', which often correlates with a traffic-free zone (TFZ), an area in close proximity to a stadium where only specially accredited and screened vehicles are allowed to travel.

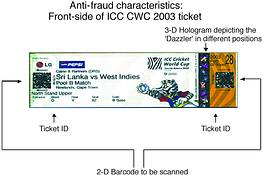
The most inner concentric circle is normally comprised of the match ticketing/turnstile access control system situated at the inner perimeter of the stadium precinct where the spectators/event staff have to pass in order to gain access into the stadium itself. Measures deployed here could include the use of encrypted two-dimensional bar-coded match tickets used in conjunction with an automated access control turnstile which again is linked, on an online, realtime basis, to the venue operations centre (VOC) of a stadium.
Proper match/event ticketing protocols are another key component of effective access control to stadia or venues. For example, the use of an encrypted two-dimensional bar-coded match ticket (which already incorporates physical security mechanisms such as special security paper, invisible ink, holograms and special serial numbers) in conjunction with an automated access and egress control turnstile with an anti-pass-back electronic control mechanism, as was the case during CWC, creates an environment in which match ticket fraud, forgery and uttering is a non-issue. The electronic linking of such systems to the stadium VOC provides on-line realtime safety information to the safety and security decision makers housed there. Practical examples of such access control related safety information include the ability to accurately monitor the safe certified capacity of stadia (to ensure that there is no overcrowding) and the ability, in an emergency and if linked to a centrally administered electronic ticket booking system, to identify whether the holder or at the very least the purchaser of a match ticket is inside a stadium or not, including what time such a person entered and left the stadia on an event day.

Typically, a match ticket used in conjunction with a system of this nature would be inserted into the built-in electronic two-dimensional code reader in the automated turnstile. The ticket would be scanned by the internal hardware and verified by the system software in a matter of seconds. The system, after verifying the integrity of the ticket, would for instance also verify whether the ticket holder is at the correct event, at the correct stadium, at the correct time and on the correct date. If these criteria are met, the turnstile will then automatically turn over. If there is a problem with the ticket, supervisor level security officials are present at ticket access points in order to determine if it has been damaged in any way or if it is in fact not valid. This is effected on-site at a nearby office equipped with a network linked match ticket system workstation manned by senior officials of the match ticketing service supplier. If for instance the damaged ticket is found to be valid by way of a verification of the holders or purchasers details via the unique ticket serial number, a new ticket is immediately issued and the damaged one destroyed. Gone too are the days of 'tough luck' if your ticket has genuinely been lost or misplaced. At a push of a button it can be determined if in fact the lost ticket has been used and if so whether the reserved seat is occupied or not. If not (or stadium security has accosted the unlawful holder of the lost ticket sitting in your seat) a new ticket is immediately issued to the original holder after an electronic cancelling of the original ticket.
Looking ahead, I am sure that in the not-too-distant future centrally administered electronic match ticketing sales systems could have portals to official 'undesirable persons' databases (databases containing data concerning persons who have been officially or judicially banned from the attendance of particular sporting events) to ensure that direct prior ticket sales to such individuals are not possible.
Proper accreditation systems, underpinned by an integrated and secured electronic security platform and centrally administered by independent administrators, are yet another important component of world-class access control of persons to major events. Zoned accreditation systems incorporating various levels of access to pre-screened (criminal record classified) event officials and personnel are the cornerstone of any effective accredited access control system. Ideally the accreditation cards, which should incorporate physical security mechanisms similar to those described above as far as match tickets are concerned, should be electronically linked to a stadium wide zoned access control system via embedded smart 'chips' or similar. When such systems are used in conjunction with biometrically supported or standalone digital CCTV surveillance and recording systems (see below), secured accredited access control systems become a reality.
Probably the single most effective access control system support mechanism currently available is the deployment of multizone digital CCTV surveillance and recording systems at stadia and venues and their immediate precincts. They have, world-wide, consistently proven to possess effective pre-emptive, deterrent and evidential recording qualities as far as proper crowd management and control at an event is concerned. As stated above they are also an effective accredited access control support mechanism. There can be no doubt that when electronic biometric technology becomes a mature technology and such systems are incorporated within software driven and controlled CCTV systems, world-class secured access control delivery at major events will be reliant upon the deployment of such systems. One could appreciate how valuable a powerful multiple facial feature recognition system, hooked up to a multizone CCTV system monitoring spectator access control points would be to stadium security stakeholders on the look out for database logged undesirable persons. No sports stadium or recreational venue should operate without such security technology."
Vehicular access control is yet another vital access control component of proper safety and security delivery at high-risk events. Access to the inner precinct of stadia at high risk events should ideally only be allowed to pre-accredited and screened vehicles belonging to heads of state, teams, players (if individual sport), entertainers, essential team/player/entertainer support staff, senior event/match officials, caterers and emergency vehicles. Where such escorted vehicles are not subjected to screening on point of departure, vehicles (such as catering vehicles) are subjected to a thorough screening at SAPS manned facilities known as remote search parks, which are normally deployed between one and two kilometres from, for example, a sports stadium. At the remote search park, the credentials and accreditation of the driver and any passengers are verified and they are screened by way of magnetometers. Both the vehicle and its load are subjected to a thorough screening by means electro-mechanical (including large conveyor belt type screening equipment) and sniffer dogs. The screened vehicle, load and the accredited occupants are then escorted to the stadium by a motorcycle equipped state security official.
While the above secured access control measures are not exhaustive of those which are indicative of world-class safety and security delivery at a major sporting event, they do provide one with an insight into generally acceptable benchmarks now and in the future. From a South African perspective and whilst there have been notable exceptions and 'pockets of excellence,' patrons of major sporting and recreational events have been subjected to 'lip service' as far as proper safety and security delivery at such events is concerned. In certain instances proper safety and security measures are virtually non-existent at such events, with organisers and stadium/venue owners relying 'on a wing and a prayer' and 'shoestring' budgets as far as safety and security arrangements are concerned. 41 of our citizens, many of them minors, should not have died at a world-class sporting facility such as Ellis Park. Likewise 48 of our citizens should not have been fatally injured during the spectator stampede occasioned by alleged 'factional' fighting between spectators. What of those killed at Loftus Versveld not that many years ago when a spectator stand collapsed. Ronan believes there is a strong school of thought that supports a view that the implementation of effective access control measures such as those described above most probably would have averted the tragedies referred to above.
There is an obligation on event organisers, stadium owners and national controlling bodies of sport and recreational bodies to put certain reasonable measures in place to ensure the safety and security of their paying patrons who attend their events. This is particularly the case when one is dealing with capacity crowds at a high risk event - the higher the risk profile of an event, the more stringent the safety and security measures one would expect to be in place. The recent initiatives by Government to regulate this often neglected aspect of the hosting of sports and recreational events is a welcome move in the right direction. It will certainly strengthen our country's hand in the preparations, lead-up to and hosting of the 2010 event to say nothing of our intentions to host the 2011 Rugby World Cup and other major international events in the interim. South Africa must remain a desirable destination for the hosting of such events.
Patrick Ronan, a lawyer by profession, is a major event safety and security, risk management and security legislation specialist. A former Department of Justice official and contracted CEO of the statutory regulatory authority for the private security industry, he is currently a director of Imvula gCn, a leading Johannesburg-based safety and security consultancy practice.

© Technews Publishing (Pty) Ltd. | All Rights Reserved.