
222OHSS57 Percentage of ICS computers on which malicious objects from various categories were blocked.
Industrial control systems at risk as the share of computers attacked with miners, spyware and malicious scripts on the rise, says Kaspersky ICS CERT.
During the second half of 2021, almost 40% of all industrial control systems (ICS) globally were attacked by malicious software at least once. Even though the overall number of attacks has seen a slight decrease when compared to H1 2021, the ICS threat landscape in the second half of the year became highly diversified, with the percentage of ICS computers on which miners were blocked grew by 0,5%, spyware up 0,7% and malicious scripts growing at 1,4 times the rate seen at the beginning of 2020.
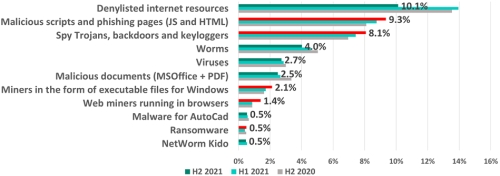
According to Kaspersky ICS CERT, the percentage of ICS computers on which malicious objects were blocked in 2021 increased by 1% from 2020, rising from 38,6% to 39,6%. However, if the situation is examined by each 6-month period, the landscape looks better, with H2 2021, seeing this figure drop by 1,4% for the first time in one and a half years.
Overall, Kaspersky security solutions blocked over 20 000 malware variants during the second half of 2021. Although this figure did not change much compared to the previous six months, a detailed analysis of detected malware shows that the proportion of ICS computers attacked with spyware, malicious scripts and miners grew.
Malicious scripts are rising steadily year over the year. In H2 2021, the percentage of ICS computers attacked by them increased by 1,4 times from the beginning of 2020 and was up by 0,5% compared to the previous half of 2021. Cybercriminals use malicious scripts to achieve various goals ranging from data collection to loading other malware, such as spyware or cryptocurrency miners.
Significantly, as threat actors use scripts more and more, they are also increasingly using spyware and cryptocurrency miners. The former is mostly used to steal victims’ credentials or money and the percentage of ICS computers attacked with spyware is up by 1,4% since H1 2020. Spyware continues to grow and is up in use for the third six-month period in a row. The share of ICS computers attacked by miners has more than doubled since H1 2020.
“Industrial control systems possess sensitive data and are responsible for the functioning of the most important sectors. A low-risk attack for IT infrastructure can still be a significant threat for operational technology (OT). While overall, the threat types that find their way to ICS computers have remained relatively the same, we have seen a constant increase in the share of ICS computers facing malicious scripts and phishing pages, along with Trojans, spyware and miners which would be normally delivered by the malicious scripts. Crypto miners are generally overlooked as a significant threat, which is not a good approach. While the influence of miners on the office network may be insignificant, in the course of their work and distribution, they can lead to the denial of service for some components of the automated control system,” comments Kirill Kruglov, security expert at Kaspersky.
To learn more about threats to ICS and industrial enterprises in 2022, check out the ICS threat predictions for 2022 at https://securelist.com/threats-to-ics-and-industrial-enterprises-in-2022/104957/

© Technews Publishing (Pty) Ltd. | All Rights Reserved.