

In the physical security arena, information and the speed at which it is delivered is key. It is this guiding principle that sees the huge growth in global PSIM deployments. Where information is key, access to information is vital, and nowhere is this more pronounced than in security. During critical events, it is essential that operators have fast and reliable access to relevant security assets, and pertinent information. Failure to deliver this information is not an option.
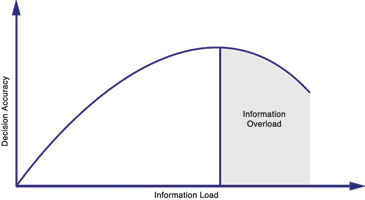
In any PSIM deployment, the day-to-day information load is relatively minimal. The challenge is the response to a sudden surge in this load, caused by a critical event or disaster scenario, comprised of multiple events happening at the same time. It is in these scenarios that a PSIM solution will need to provide the highest level of assurance that all information required will be available when needed. In addition, the solution will need to remain highly responsive, providing essential intelligence and data analysis, to enable security operators to react and respond immediately.
What is Service Oriented Architecture?
Service Oriented Architecture (SOA) simply put is a series of methodologies adopted to create separate software modules which, while interoperable, are independent to one another. This is referred to as ‘Loose Coupling’ and is essential to an enterprise level SOA based solution.
Each service within a SOA deployment should have a single functional responsibility; such as reporting, authentication or communications. It is this separation of functional units that drives the benefits of SOA. Loose coupled services allow developers to increase flexibility across networks and infrastructure boundaries, expanding capacity, distributing load and removing bottlenecks.
Secured published endpoints, share the functionality of each service across the deployment, and with linked systems such as accounting or reporting. This enables greater PSIM integration with business systems and processes.
How does SOA help PSIM?
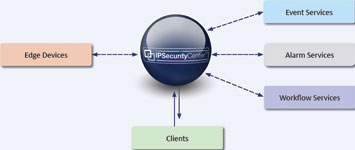
SOA enables a PSIM application to process event data in real time, as well as update operators and security personnel with the information they need both in the control room and in the field.
The use of independent stateless services provided by SOA brings new levels of availability, performance and capacity, while also improving disaster recovery of the PSIM solution. These are built into the application architecture, so are intrinsic before considerations are made at the platform or infrastructure level. This same stateless nature reduces the cost of growth, maintenance, and future HA/DR concerns, reducing the overall Total Cost of Ownership (TCO) of a PSIM deployment.
Delivering value with Service Oriented Architecture (SOA)
The availability of data and the response to it and are essential to a successful security operation. Information should be available to operators in real time. However, as deployments and security operations grow, too much information can lead to information overload. This dramatically reduces the effectiveness of security resources.
The follow up to an incident needs to be tightly aligned to standard operating procedure (SOP) while remaining unobstructed, allowing delivery of mission-critical information and analysis to security personnel, without the need for manual intervention. Security operators need to react as soon as possible to events and the slightest delay can seriously impact the outcomes. Waiting for a PSIM system to catch up is not an option.
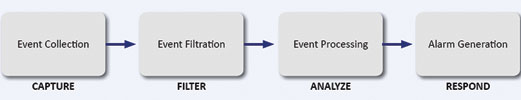
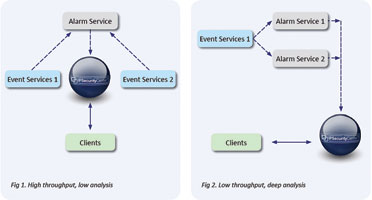
Identifying four key areas that form the PSIM event pipeline, and addressing each individually, refining and optimising the way a PSIM behaves in each area, providing complete situational awareness, in the fastest possible time.
These are:
1. Event collection.
2. Event filtration.
3. Intelligent analysis.
4. Alarm/response generation.
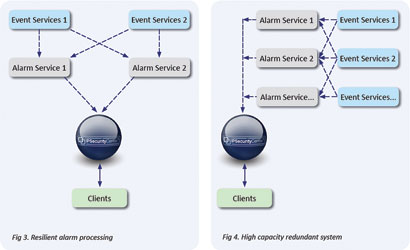
Subsequently, each area is independently scalable, allowing PSIM solutions to scale only where additional capacity is required. This dramatically increases the cost effectiveness of upgrades required by growth in the security deployment.
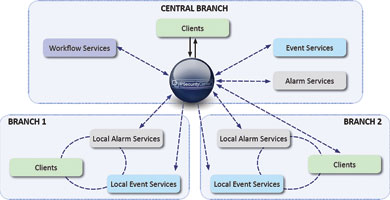
In this SOA environment, each of the services is a completely stateless entity. This means multiples of each service can be added to a deployment to support operational requirements. For example, where High Availability & Disaster Recovery (HA/DR) is needed, it can be added without having to upgrade the whole solution. Services can be added or removed from a deployment, even dynamically, allowing for 100% uptime during maintenance or dynamic increases in resource availability during those critical ‘Burst’ demands on the systems seen during major incidents.
Solid SOA by design
A PSIM vendor who adopts true SOA understands that each service needs to be optimised for performance in its area of functional responsibility within the larger system. This is not however, where the only benefits of SOA end. A PSIM event pipeline is only as good as the weakest link in the chain, so it is essential to apply the same innovation and attention to detail in the links between its services.
Events throughout a true SOA PSIM deployment should traverse services in its architecture via messaging queues. These queues ensure that the first message delivered to a service, is the first message processed. Most software developers simply select a queuing technology, and apply it throughout their solution. All messaging technologies are not equal.
Some are geared for speed, some for reliability, and some for flexibility. A well-architected SOA solution should utilise the most appropriate technology at each communication boundary, making best use of each to allow the solution to process events smarter, faster and unobstructed.
It is essential that each queue is wrapped with intelligence to ensure that no event is lost, every event is processed, analysed and logged as necessary to provide the best security response in real time. These wrapped ‘Intelligent Queues’ rely on the messaging system that underlines its SOA implementation, thus ensuring every event and message ends up in the right place at the right time.
Even bad messages are collected, stored and logged, within ‘Poisoned Message Queues’, allowing for the analysis and reporting of bad messages within a system. In any system that does not provide this functionality operations would be brought to a standstill as services failed to cope with the corrupted, or ‘Poisoned’, messages. This also brings about an increase in security, as any messages that do not conform to precisely the structure and content expected are isolated and stored, therefore unable to have any performance effect on the overall PSIM solution.
Cost effectiveness and TCO reduction
SOA not only offers a more robust solution, but also a more cost-effective one. Whether at the small scale, or enterprise level, the benefits of SOA to the Total Cost of Ownership (TCO) of a PSIM deployment can be realised. These benefits reduce the cost of solutions for both integrators and end users alike.
The key benefit here is that each service can be deployed on hardware tailored to suit its needs. This significantly reduces the cost of hardware as over-specified, under utilised hardware becomes a thing of the past. Excess capacity, can optionally be utilised by instances of other services, to realise the full return of investment on hardware and infrastructure.
Small-scale deployment
Each service in a SOA should be kept as light as possible, minimising resource overhead against performance. A good PSIM vendor should be constantly refining the performance and resource consumption of its event and alarm handling services in order to reduce the footprint on expensive underlying hardware infrastructure.
SOA offers small security operations the ability to minimise infrastructure requirements by deploying multiple services on the same hardware. Depending on customer requirements this can be deployed on as little as a single server.
As the requirements grow, SOA allows the infrastructure to grow proportionally with it, moving out services to their own dedicated hardware, as demand on the system dictates. This separate hardware need only satisfy the specification requirements for the specific service being loaded onto it, rather than requiring multiple expensive core servers for each growth cycle, as is so typical with most non SOA PSIM deployments.
Medium to enterprise deployments
In larger deployments where capacity goes beyond individual units, the cost of scaling is significantly reduced with SOA. Where some deployments require additional core servers to extend capacity, SOA only requires additional service nodes where additional provision is required. Additional nodes are tailored to requirement, investing only in the necessary hardware to provide the capacity needed.
Of course in security, planning is always for a major event, not the day-to-day operation of a system, and this is where SOA really shines in the large deployment scenario. Multiple services can be deployed within each hardware region, and dynamically activated, increasing capacity in functional areas of the software to suit demand as it occurs.
Are all PSIM solutions based on SOA?
Many PSIM providers claim to have developed their solutions utilising SOA. Despite this, few have brought to realisation the benefits of SOA to their customer’s solutions. Simply developing software as separate modules, and publishing them as ‘services’ does not necessarily mean that the developer’s architecture is truly service oriented.
In a true SOA product, services are independent, capable of operation without dependency. Services are scalable, additional services can be added to a system, providing immediate increase in capacity, processing power and/or redundancy.
Without a SOA, a PSIM system will not provide sufficient capacity at each stage of the PSIM event pipeline cause huge spikes in demand for processing capacity. Simply put, the system will most likely become unstable during times of high stress, ironically just when there is the greatest need for a PSIM solution.
For more information contact CNL Software EMEA, +44 1483 480088, [email protected], www.cnlsoftware.com

© Technews Publishing (Pty) Ltd. | All Rights Reserved.