

One year after the Snowden affair, the ICT community continues facing increasing challenges to effectively protect information and data. A lot has been revealed about the programmes conducted by governments, and it is not just the NSA, using sophisticated techniques to spy on data flowing through private and public networks. The awareness of it has opened the eyes of many security officers, CIOs, company executives as well as anonymous people concerned about their privacy.
This article is not about Snowden and the NSA, it is about what security risks threaten organisations when their members, managers and employees, use modern mobile services to communicate over legacy networks and which strategies could help to mitigate those risks.
The mobility market
Traditional IT services have been gradually made mobile. This ranges from the very basic ones such as voice or email up to more sophisticated ones like unified communications, instant messaging, video conferencing, collaboration, corporate data access, etc.
The rapid growth of the smartphone industry coupled with the investments made by carriers on the networking side and the wide range of over-the-top (OTT) (independent third-party services) and social networking services have changed not only the user habits but the way the market behaves as well. In most cases the adoption of new technologies just happened too quickly, without the possibility to implement proper security strategies or to understand the new risk factors.
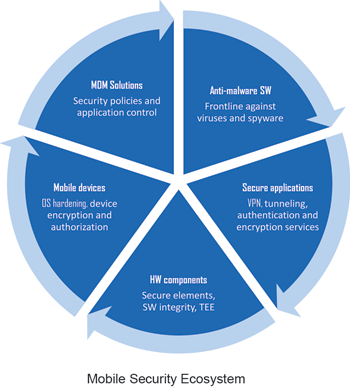
A number of new actors have entered the mobile security ecosystem. We have seen Mobile Device Management (MDM) solutions spread widely in recent years. They add protection and control over the mobile device and help setting up security policies for their usage, access and application containerisation.
Traditional PC anti-virus and anti-malware companies have moved to the mobile space, reacting to the increasing number of spyware and malware that is being detected in smartphones. Similarly, mobile OS and device vendors have set a stronger focus in security by introducing OS hardening options and HW and middleware based security mechanisms, such as the so-called Trusted Execution Environment (TEE).
Finally, a number of applications and products have arisen to protect specific enterprise grade services like remote authentication and authorisation, tunnelling, secure email services and protection of application data at rest.
Threats and risks
Despite these new technologies and security options, basic and essential communication services still operate without any type of protection. Simply think about phone calls, SMS, instant messaging services, just to mention a few. These are widely used services that in the majority of organisations are not protected at all and for which most of the security products mentioned above don’t provide any type of protection.
It is quite common for security-sensitive segments like financial institutions, law firms, global companies in energy and securities, etc., and of course the public sector, to employ some of the protection mechanisms already described. However, they still make phone calls through regular channels, send SMS and even use third-party services of dubious security. When consulting sensitive target groups about their mobile security strategies it is often surprising to see that they may have built very strong concrete walls but they haven’t locked the front door.
Let’s start with OTT services. Many mobile OTT services are used by professionals with their corporate devices. Some of these services are used within the organisation for internal and external communication, consequently exposing confidential data and content, as well as for private reasons.
This represents a double risk. Firstly, all data and information transmitted through those services might be accessible and even retained by third parties. Furthermore, the company providing and operating the service might be subject to regulations in their country of registration that require the transmitted data to be accessible to local authorities. Even if the service is claimed as “secure” and includes encryption and security mechanisms for data protection, these regulations may grant its access to a lawful authority and, implicitly, the possibility for an unlawful one to access the data as well. Secondly, OTT services rely on third-party SW developed by companies or people you don’t know and you may not trust. Behind a harmless application there could be harmful code that an organisation won’t be able to assess or verify. In summary, don’t allow the usage of services or applications you don’t trust and have verified with the vendor or service provider.
A second area that threatens mobile communications is the access and transmission network. Telecom service providers obtain an operating licence that is bounded to certain conditions and regulations in this matter and generally allows lawful authorities to intercept essential services like telephone calls, SMS and metadata for data services such as websites visited, E-mail traffic, etc. Lawful interception is a legal and legitimate interception function important for law enforcement agencies to prevent and investigate illicit activities, terrorism or organised crime. It is mentioned here as a potential threat because it constitutes a mechanism that is present and exposes your data and communications to third parties. When roaming in foreign countries one should be aware that local authorities may have access to exactly the same data as in the home network.
Beyond lawful interception, access and transmission networks could be exploited by malicious hackers to eavesdrop your communications. It is well known that the cryptography used in 2G cellular networks has already been broken. 3G/4G networks are better, but still they must be compatible with 2G and there are mechanisms to force a device to operate in 2G mode for a phone call, for example, or to impersonate the 3G network provider because mutual authentication might not be enforced and the device must support it due to interoperability reasons.
On the backbone side, your data is not always properly protected in any way. Employees of a service provider may have access to more privacy-relevant information than we may think (location information, SMS data, call records, etc.). External attacks could be performed against telecom cables and satellite links, some of which might be initiated by governmental agencies, with and without the collaboration of carriers. As indicated, the topic is extensive, but we shall simply be aware that the data we send through a carrier or service provider cannot be considered private; it might be accessible to multiple parties in different ways and we shall add our own protection layer onto it. Same applies to WiFi access networks, public or private.
Security strategies
Before implementing a mobile security strategy, the potential threats have to be identified and security goals defined. Once this is done, the next step is the design of a security concept for the target organisation, in particular for the mobility services that produce, carry or store sensitive information. Considering that mobile equipment shall be used over multiple networks and different environments, i.e. it is “mobile”, the data and information in transit shall be protected at a higher layer above the network.
How to protect basic and essential mobile communication services such as telephony, SMS, messaging, document transfer, etc.? These services deliberately exchange information with external entities or agents. This communication may carry confidential data, such as the company strategy spoken during phone conversation, a message containing an access code to a corporate resource or simply a contract that must be reviewed by a legal department. You must protect this content according to your security goals.
The security level and technology employed will depend on the type of information to be protected and its classification. Encryption and cryptography is the solution, but only when designed, implemented and deployed correctly. The biggest concern on cryptographic and encryption systems is not the mathematics but a wrong implementation or design. Authentication, authorisation, confidentiality and integrity protection represent the key aspects any secure communication system shall offer and enforce. The right balance between user friendliness, usability and protection must be carefully chosen. For machine-to-machine communication this selection is easy, but when humans are involved in the equation the usability aspect must not be ignored; I have witnessed very strong and costly security products locked in the drawers of government officials and politicians because they were simply unusable and not practical, which led to the fact that the majority of phone calls were simply made as usual through the standard channels.
Qtalk – a secure mobile communication solution
A solution to add protection to mobile communication services is provided by the Swiss company Qnective. The company is specialised in securing communications for both the public and private sectors using COTS devices. With a long tradition in cryptography and operating in a politically neutral country, very sensitive and respectful with privacy rights, Qnective offers a secure mobile communication platform implementing strong end-to-end encryption techniques to protect the most basic and sensitive services in everyday use.
The platform, called Qtalk, has the aim of providing a high-quality, efficient, user-friendly and cost-effective solution that helps every organisation securing confidential and sensitive data when using mobile services over uncontrolled networks. The double-layer encryption technology embedded into Qtalk protects multiple communication services, including voice, messaging and document transfer, not only externally, but inside the organisation as well.
Specific security functions have been introduced to avoid any unauthorised access to user data or credentials. Several techniques are employed in our products to reach that goal: End-to-end encryption channels, perfect forward secrecy in the communication, protection against replay and dictionary attacks and integration of strong crypto algorithms which can be verified and customised per organisation represent some of them. As specialists in encryption of real-time mobile services, we take special care of our secure VoIP implementation balancing voice quality in wireless networks and bandwidth efficiency without revealing call information from the ciphertext. Therefore, we use an optimised constant bit rate with dynamic re-keying and reduced data overhead thanks to our proprietary communication layer.
Qtalk can be combined with hardware based crypto modules for strong protection of key material and certificates. Depending on the security needs and deployment model, this architecture offers a very modular and flexible approach that can be tailored to the specific needs of every organisation, in addition to customisation options for the cryptographic algorithms used by the product. This way, it reduces the cost of ownership and its maintenance and operating complexity compared to more traditional solutions. Furthermore, the product is easier to maintain, support and evolve and facilitates the migration of devices without incurring any additional costs. Qtalk is a cross-platform solution supporting a wide variety of COTS devices and desktop computers, covering all modern communication needs, developed entirely in Switzerland and fully deployable on customer premises.
For more information contact Qnective, [email protected], www.qnective.com

© Technews Publishing (Pty) Ltd. | All Rights Reserved.