
An e-mail invitation to an iTunes update gets iPad users’ PCs into backdoor trouble.
Success stories are cybercriminals’ go to sources of victims and the iPad craze could not have been left out of this picture. According to some reports, Apple sold 150 000 iPads in the first 60 hours of presale availability, with almost 100 000 of these coveted devices being pre-ordered in the first 10 hours. The figures make it clear as daylight why malware creators were so keen on crashing this promising party.
The invitation to the 'contagious fiesta' comes via the e-mail: an unsolicited message instructs iPad users to download on their PCs the latest version of the iTunes software as a preliminary step to an update of their iPad software.
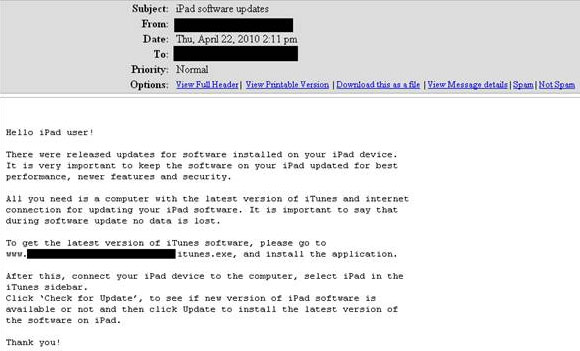
To carry conviction, the e-mail emphasises that users should keep their iPad software updated 'for best performance, newer features and security'.
It goes on to clarify the multistep procedure by pointing out that in order for the update to be performed the latest version of iTunes should first be downloaded from the Internet. A direct link to the download location is conveniently provided. As a proof of cybercrime finesse, the webpage the users are directed to is a perfect imitation of the one they would use for legitimate iTunes software downloads.
Unfortunately for these users, following the malicious link means opening up a direct line to their sensitive data as instead of the promised iTunes update they get malware on their systems.
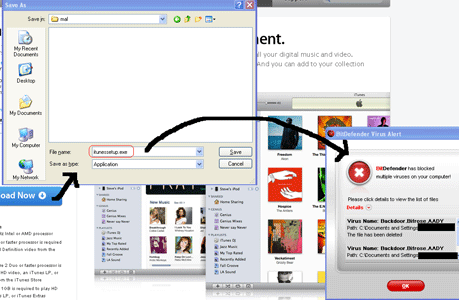
Identified by BitDefender as Backdoor.Bifrose.AADY, the piece of malicious code inadvertently downloaded injects itself in to the explorer.exe process and opens up a backdoor that allows unauthorised access to and control over the affected system.
Moreover, Backdoor.Bifrose.AADY attempts to read the keys and serial numbers of the various software installed on the affected computer, while also logging the passwords to the victim’s ICQ, Messenger, POP3 mail accounts, and protected storage.
It is important to say that Mac users remain unaffected by this piece of malware.
For more information contact Alina Anton, senior PR and marketing coordinator, EMEA & APAC Business Unit, BitDefender, +40 212 063 470, [email protected], www.bitdefender.com

© Technews Publishing (Pty) Ltd. | All Rights Reserved.