
The March 2010 edition of Hi-Tech Security Solutions featured Part 1 on Blueprinting your Integrated People Management Solutions (IPMS). Part 2 follows.
In the March article, it was highlighted that a crucial step in understanding the bigger picture is understanding the company’s true requirements and ensuring that the solution implementation meets the company’s business objectives.
By soliciting vendors prior to performing a blueprint, business requirements and resulting technology selection is driven by what the vendor’s products strengths are and not by what the business really wants the technology’s strengths to be.
So, how do you get it right first time and on budget? The diagram shows an example of a modern IPMS framework that should be considered during your blueprinting process.
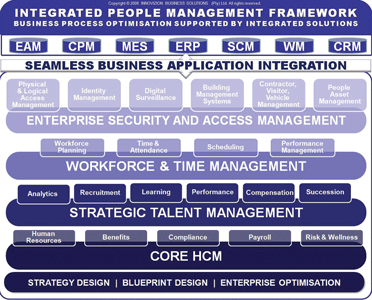
In most companies, many of the functions listed in this framework operate as silos. Small enterprises can cope with these islands of information. Medium to large enterprises however, have specific departments dealing with these functions.
For example, there is a security/risk department that needs security information about their employees. There is a manufacturing department that needs people asset management, time and attendance, contractor, visitor and vehicle management. There is a logistics and warehousing department that needs digital surveillance and performance management. There are retail stores that need workforce planning, scheduling and single-sign-on for the POS sale operations. The list goes on – not even to mention the human resources department.
These business functions need an integrated approach to enable process owners to manage costs and drive profitability effectively. Therefore, understanding, documenting and then managing your business processes across these functions becomes important. This is core to the blueprinting process. It enables process owners to understand up-stream and down-stream effects across departments and identify ways to benefit from the information generated by them.
Once the business processes are defined and business benefits are understood, business requirements are defined and prioritised.
Typical questions from management would be: 'How much will we save?' and 'How much will it cost?' Defining the benefits up front is important in order to motivate the required changes. Getting the requirements clear and complete also helps getting the costing side right resulting in more accurate budgets.
'Must-haves' vs. 'nice-to-haves' plays a big part in clarifying the requirements. For example, the HR manager might think to have an access control solution that seamlessly links to a criminal record check is of low priority. The security manager might see this as high priority based on certain legal requirements and/or industry specific standards. If these are not discussed and agreed up front, the company might miss critical requirements.
Blueprinting your IPMS also has benefits in the detail design and implementation phase of the project. It reduces the chances of:
* Technology not fitting the business requirements.
* Adapting business processes to fit with the technology, rather than vice-versa.
* The project team encountering resistance from the business users.
The last part of the blueprint focuses on the technology side, where the systems architecture is defined. This includes hardware, software and networking requirements. Based on the business processes and business requirements, a systems architecture model is developed. For an IPMS, typical aspects to consider include secure Single Sign-On, centralised vs. decentralised data management, biometric template distribution and total and seamless integration to other business applications.
For more information contact innoVIZION Business Solutions, +27 (0)11 463 0123, [email protected], www.innovizion.co.za

© Technews Publishing (Pty) Ltd. | All Rights Reserved.