

CCTV systems have been around for decades and we have seen huge technological advances in the offered facilities during this period. These advances have gained momentum in recent times with the convergence of legacy analogue systems with the digital realm. One of my favourite sayings is “so what does that do for me”, or in this case “so what does that do for the user”. In order to fully explore this statement it is best to analyse the fundamentals of why a CCTV system is installed and used in the first place. Let us list some of these:
1. To observe manufacturing processes. This is probably the most under-developed market for CCTV systems. This is notably because legacy systems have to date been of limited or no use.
2. To observe activities in a retail environment. In this instance, CCTV operators would be trained to spot suspicious shopper activities and body language. Such installations have many high-speed dome cameras and the operators continuously manipulate the camera viewing area while observing shoppers. The success of these systems depends on the diligence of the operators in ensuring that crime is at least controlled to minimise losses and to collate evidence for the purpose of prosecution.
3. To observe cashier activities in a retail environment. This is where a well-developed POS (point-Of-sale) system is crucial to be successful. In this case, real-time and post-event analysis takes place.
4. To observe people activities in an inner city environment. The same rules apply as in 2 above as continuous real-time observation takes place. In both cases the area under observation is huge and it is impossible for the cameras to view everything. Operator diligence is crucial to system success. In this case most incidents take place over a longer time enabling operators to capture most of the associated activities for post-mortem analysis and to steer the appropriate reaction forces to the scene.
5. To observe people in a banking environment. Mostly, static cameras are installed and continuously recorded without any real-time observation taking place. The images are only viewed after an incident is reported. Off-site alarm verification surveillance monitoring is critical.
6. To observe a perimeter boundary and buildings. This market is huge and is the most mature of all CCTV system installations. We will not discuss it further here.
7. To observe mining processes. Such systems can be sub-divided into two categories, the mining process itself, including securing the mined product; secondly, securing the perimeter and buildings (including the processing plants). The latter case is the same as noted in point 6 above. However, I am convinced that the mining process has a great need for properly engineered electronic security systems.
Currently installed systems
Mining environments such as diamonds, gold and platinum normally have hundreds of CCTV cameras installed throughout the plant. These cameras are specifically installed to observe the many processes within the plant and are mostly installed in an overt manner. Covert cameras are installed on a temporary and portable basis and will not be covered here. The control room operators observe the general movement of plant and people, invariably with limited success. For such a system to be fully exploited, one would need an operator viewing each camera on a 24/7 basis. As we know this is impossible and fatigue is such that after 30 minutes the operator will probably not observe a jumbo jet slipping past the camera view.
Intelligent video management systems have now reached the maturity to deal with this problem and can integrate to virtually any source of event data. Complex rules can be built which take into account related, but disparate events which indicate impending failure or warrant further investigation.

Intelligent systems
It is a well-known fact that any well-developed business administration system has many tools that allow a trend analysis of transactions to pinpoint fraud, operator input errors and much more. The POS systems mentioned above have proved to be of immeasurable value to circumvent or to prove fraudulent transactions that take place. If one has to apply these same rules to an electronic security system then interesting facts emerge. Let us look at the following, in this case specifically pertaining to a mining environment (please note that for security reasons I have made very general statements):
1. Any mining environment has many process control elements such as weight measurements, conveyor belt control mechanisms (normal control and emergency stop), ore transportation systems, ore concentration or extraction processes and finally the product measuring and transport systems.
2. The mines in all cases have access control card readers installed throughout the plant to restrict people movement.
3. The mines in all cases have extended alarm systems that do not only monitor the plant process operation but also the unauthorised opening of distribution boxes, PLCs and many other control systems.
In a truly intelligent electronic security system, all the events that are already captured in the above noted sub systems should be critically analysed to do a proper trend analysis. This will not only extract pertinent process control data but more specifically security risks. For example, the emergency stoppage of a conveyor belt may be an orchestrated event to create an environment whereby the mined product may be removed by hand during the resultant spillage recovery operation.
The operators within the plant as well as the security staff that are on duty at the time are often not considered. A well-defined trend analysis could quite conceivably extract the fact that it is always the same staff on duty when this transpires. To analyse this trend on a manual basis is nigh impossible. We accept that the risk associated with this particular exception differs, dependent on the mining environment as the concentration of the mined product may be so small that the risk is minimal. However, it is still noted because it may play a role within the context of the bigger picture.
The unauthorised opening of control boxes is normally investigated but authorised opening or dismantling of the same boxes should also be investigated for trends as mentioned above. Plant failures such as motors, pumps etc, are seldom considered; video motion detection should be verified against all other events that take place; both overactive alarms and under-active alarms should be considered.
The weight measurements noted above are seldom compared against the measurement of the final product. In order to do so, on a manual basis, is impossible due to extended time factors that have to be considered from the moment the ore processing starts to the end of the process. However, many sophisticated systems can be installed along this process and invaluable events may be extracted from these systems to capture and highlight a trend in an exception reporting format. It is quite conceivable that a trend analysis will pinpoint a problem long before the end of the ore processing time has been reached. This is primarily the purpose of installing such a system.
The systems noted above are not available as off the shelf products as a huge amount of customisation is required to ensure success. Of importance is the following:
1. Ensuring that whatever system is installed has already been developed and installed successfully. This will ensure that the required system is not merely vapourware or pie-in-the-sky systems that still need to be developed.
2. That all of the current installed systems can in fact be interfaced to create the necessary event extraction from external software controlled systems. This will necessitate that software development kits (SDKs) and application programming interfaces (APIs) must be available to allow ease of interfacing. If this is not available then the software integrator must have the necessary skills to extract the data by other means.
3. That a software development integrator is chosen with the necessary skills and past performance track record.
4. That a project team be appointed to not only represent the supplier, but of equal importance, the client. In the latter case, someone with an intimate knowledge of the plant process must be appointed to provide input to allow the definition and creation of a rules base. This noted rules base will then form the basis of the analysis through a filter process.
5. That the system will need to be fine-tuned during use as everyone on the team will find methods of improving the system performance. It is for this reason that software maintenance forms part of the complete solution.
Case study
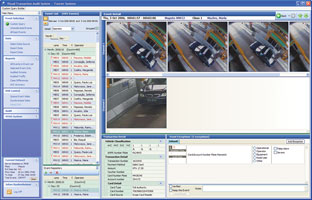
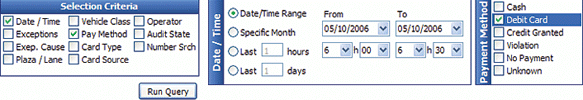
Some screenshots of a video-based toll road auditing application are shown. We grant the fact that this is not a system deployed in a mining environment, but many of the same rules and concepts apply. In this case every transaction is stored and linked to associated data, including operator, event inputs from axle-counting and other road-side devices, vehicle number plate recognition, transaction detail, video motion detection, date and time etc.
A rule-based data processing engine generates events for any detected anomalies. The system extracts off-line images for each of these events while a powerful easy-to-use query tool allows the user to drill down to the pertinent exceptions. This enables management rapidly to view each anomaly and either to close it off after auditing the event for higher management check-up, or to print it via a customised and automated report writer. In the latter case an operator disciplinary investigation is possible. This particular system interlinks directly to the DVR or NVR system to allow immediate review of the recording. Manual searching through a massive video image database is thus circumvented.
Without such a rapid event viewing system, clients seldom verify events that take place as it is a laborious or virtually impossible task.
For more information contact Jan de Beer, MultiVid, +27 (0)11 894 7127, [email protected], www.multivid.co.za

© Technews Publishing (Pty) Ltd. | All Rights Reserved.