
Highly intensive spam waves hit two popular social networks with a frequency of over 500 messages in 10 minutes.
BitDefender notes that it is spam time, again. With the minor difference that the numbers are higher, both in point of arrows shot and in that of targets potentially hit. It is a spamming spree that has got big enough to cause concern, the more so as it comes packed with malware.
These are twin campaigns born under the same theme: an alleged password change. Whether on Facebook or on MySpace, users are informed of the fact that the passwords to their respective accounts have been changed. Consequently, they are invited to open the zip files attached to the messages so as to find out their newly assigned passwords.
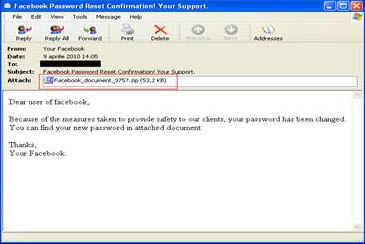
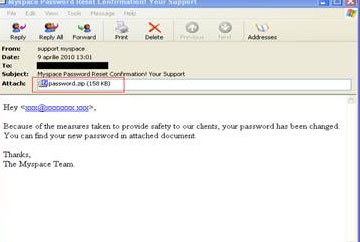
'One click away', the well-known catch phrase, may stir up unusually dramatic feelings if the recipients of these e-mails actually open the attachments, as, in both cases, the surprise is store for them is a piece of malware.
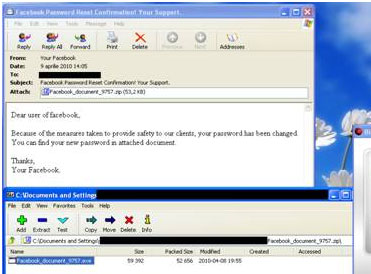
Instead of the promised password, the zip file that reaches Facebook users’ inboxes hides Trojan.Oficla.J. This piece of malware contains malicious or potentially unwanted software which it drops and installs on the system. It installs a backdoor which allows remote, clandestine access to the infected system. This backdoor may then be used by cybercriminals to upload and install additional malicious or potentially unwanted software on the system.
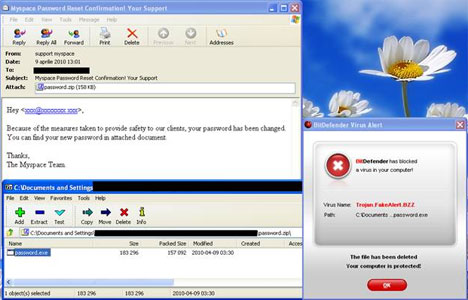
MySpace users will receive another piece of malware: a rogue avtivirus.
The behavior of Trojan.Fakealert.BZZis comparable to that of other rogue antivirus:, the browser window automatically minimises and a warning message is simultaneously displayed. This message notifies the user about several alleged computer infections and it points out the necessity of installing a security solution.
By clicking either the OK or the Cancel buttons of the various pop-up windows appearing on the screen, the user activates a false demonstration that unfolds in the restored browser window. This demonstration imitates an on-going scanning process that detects oodles of malware in the system, while other fake pop-up windows attempt to trick the user into downloading the malicious program posing as the antivirus.
With each so-called scan, more and more notices of false detections place the user under the pressure of registering the rogue antivirus. Once installed, it modifies or irremediably damages the content of several system files and it conveys numerous pop-ups on sham system problems and fake infections, while also persistently asking the user to buy or renew a license.
For more information contact BitDefender, +27 (0)11 789 6181, [email protected], www.bitdefender.co.za

© Technews Publishing (Pty) Ltd. | All Rights Reserved.