
Smart building systems, open systems architecture and enterprise integration are regular phrases bandied around the corporate world to encapsulate the integration of various systems into a single interface.
There are a wide variety of offered solutions and most state that they will and can integrate legacy systems into one management system providing 'effective management', 'risk mitigation', 'energy savings', 'cost effectiveness', 'improved results' and many other claims. However, where are the pitfalls and what should you really be looking for when considering the hype and the badging of these technologies into one common interface?
A management system is a means of integrating and converging various sub-systems and technologies into one single platform. Three historical streams have been progressively converging into one common platform:
* Security management - combining cameras (IP and analogue), DVRs and NVRs with access control, security systems, fire and safety platforms.
* Building management - BMS - combining HVAC, electrical, lighting, UPS, lifts and escalators etc.
* Facilities management - combining maintenance, administration, assets, cleaning, etc.
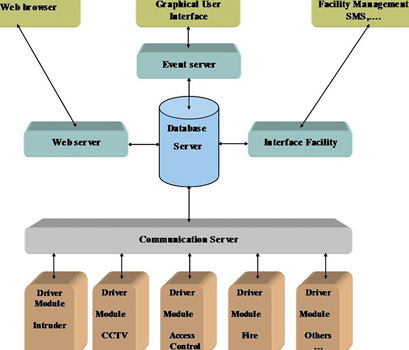
Terms such as SCADA (supervisory control and data acquisition) or PLC ([programmable logic controllers) or RTU (remote terminal unit) or even HMI (human machine interface) are all really some form of management system interfacing to component platforms involved in one or more of the above. Therefore, how does one know and understand what the management system provides and why might it be different from the various competitors in the market place?
The first step must be to establish what is to be achieved. One client may require the integration of different CCTV platforms and some 12 different access control systems into one coordinated managed system. This is across more than 200 buildings. The solution is to either take a basic remote site interface that may be universally available, to utilise a 'standard protocol' or to approach each vendor company and ask for the relevant native drivers. The practical application of this route will be determined by the cost of the driver development and as we have seen with several suppliers the offered cost of the driver development amazingly outweighs the cost of a new replacement system.
It is sometimes difficult for the layperson and/or decision maker to understand what is being referred to in the above statements. Therefore, the following should simplify and provide direction in the questions before committing a large budget spend to a product or system that might significantly restrict choices in the future. In the case of the previous example with 200 buildings it could well be better for each CCTV system and access control to operate into their own management layer on site, with a remote transmission device for central control room management. However, should a user be looking for more than this and the integration of say lighting and electrical systems then the benefits of a full management system would come into play; this would all be price dependent upon consideration of what he needs to achieve.

Having decided to run with a management system the rule is to allow each separate device to perform its relevant functionality individually and to interface key triggers to the management system. This provides standalone control and an element of redundancy in case of a problem with any component. The central control management software interface will then manage each of these systems as an additional layer to confirm, display the event and provide a course of action. This control room interface often uses a variety of open system communication protocols such as IP, Modbus, BACnet, LonWorks, SNMP etc; these are standard protocols but you need to be aware that they are also developed into proprietary packages. The core to this issue is where we have seen the driver controlling the system device only able to operate the basic functionalities of the system. A simple example is the Modbus protocol which provides an open system standard, therefore using this protocol will provide a simple language to convey a standard instruction to the allocated receiving system. The critical point is to know that all of the required functionality for that system is contained within the open standard of the protocol or if there are hidden functions that have been made proprietary. For instance the open part of the protocol may allow simple controls but may prevent you from the advanced aspects of controlling the system thus reducing an expensive system to a limited capacity. The solution is to ensure that you have written confirmation of the full functionality of the system you require within the driver that you will be given. This is why your preference should be to create a native system driver from the original protocols to give you this full functionality with optional upgrades as and when they become available. This relies upon being able to source these protocols from companies that are all in competition with each other and herein lies the core problem as Company A will not necessarily be given the protocols from a best of breed product from Company B.

The scalability of a true open architecture management system should allow you to choose the levels of integration you require. Integration does not have to be an expensive choice; it is completely scalable and modular/granular so you therefore do not need to be locked into one single brand. In some cases initial use of your chosen management system will be for CCTV and access with perhaps fire and safety later, developing into greater integration as and when needs and budgets become available. The integration should be through whatever communication protocol you desire and should enable you to choose the best of breed products without being forced to go with an in-house range. In this way you can plan your integration and see the immediate return on investment according to the systems you want to integrate.
For more information contact Vision Catcher, 0861 VCATCH (822824), [email protected], www.visioncatcher.co.za

© Technews Publishing (Pty) Ltd. | All Rights Reserved.