
Network video is also referred to as IP video because it uses Internet Protocol (IP) to carry data.
IP basics
Each device on a LAN (local area network) must have a unique address, commonly called the 'IP address'. An IP address consists of four numbers in the range 0-255 separated by a dot, for example: 192.36.253.80. Most often you will be working on a network where the first three groups of digits are common to all devices connected to the same segment, so all units on the same segment will have an address beginning with 192.36.253.
The most common protocol used is TCP/IP, which is the carrier for higher-level protocols such as HTTP used to browse web pages. Different protocols are typically associated with a port: a device has one address but multiple ports, rather like extension numbers on a PABX.
Common protocols and their port numbers used for network video (see Table 1).
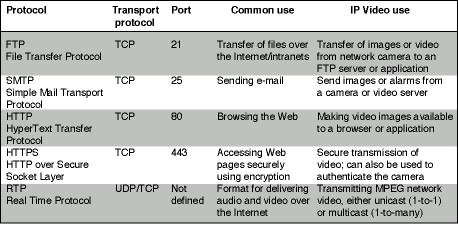
IP uses two transport protocols: Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). TCP provides a reliable, connection-based transmission channel that ensures data sent from one end is received on the other. UDP, on the other hand, is a connectionless protocol that does not guarantee the delivery of data sent, thus leaving the whole control mechanism and error-checking to the application itself.
Transmission methods for network video
There are different methods for transmitting data on a computer network:
* Unicast: one-to-one communication between sender and recipient.
* Multicast: one-to-many communication between a single sender and multiple receivers. Multicast technologies reduce network traffic when many receivers want to view the same source simultaneously, by delivering a single stream of information to hundreds of recipients. The video stream only needs to be sent once. Multicasting is commonly used in conjunction with RTP transmissions.
* Broadcast: one-to-everybody transmission. On a LAN, broadcasts are normally restricted to a specific network segment and are not in practical use for network video transmissions.
Network security
There are several ways to provide security on a network. Everything, from the data sent over the network to the use and accessibility of the network, can be controlled and secured.
Secure transmission
Providing secure transmission of data is like using a courier to carry a sensitive document from one person to another in a locked and sealed briefcase. When the courier arrives at the sender, he is asked to prove his identity. Once this is done, the sender decides if he is the one he claims to be, and if he can be trusted. If all is in order, the locked and sealed briefcase is handed over to him, and he delivers it to the receiver. At the receiver, the same identification procedure takes place, and the seal is verified as 'unbroken'. Once the courier leaves, the receiver unlocks the briefcase and takes out the document to read it.
A secure communication is created in a similar same way in a three-steps procedure:
* Authentication is for the user or device to identify himself to the network and the remote end by providing some kind of identity to the network/system, like a username and password or an X509 (SSL) certificate.
* Authorisation follows having this authentication accepted by verifying whether the device is the one it claims to be. The provided identity is verified against a database or list of correct and approved identities. Once authorisation is completed, the device is fully connected and operational in the system.
* Privacy: The final step is to apply the level of privacy required by encrypting the communication to prevent others from accessing the data. Encryption can lead to a substantial decrease in performance, depending on the implementation and encryption used.
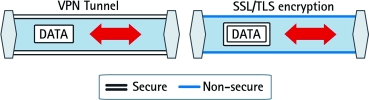
Privacy can be achieved in several ways. Two of the more commonly used methods are VPN and SSL/TSL (also known as HTTPS):
* VPN (virtual private network): A VPN creates a secure tunnel between the points within the VPN. Only devices with the correct key will be able to work within the VPN. Network devices between the client and the server will not be able to access the data. With a VPN, different sites can be connected together over the Internet in a safe and secure way.
* SSL/TLS: Another way to accomplish security is to apply encryption to the data itself: there is no secure tunnel as in the VPN solution but rather the data sent is secured. There are several different encryption techniques available, including SSL, WEP and WPA (WEP and WPA are used in wireless networks). When using SSL, also known as HTTPS, the device or computer will install a certificate into the unit, which can be issued locally by the user or by a third-party body such as Verisign.
Protecting single devices
Security also means protecting single devices against intrusions, such as unauthorised users trying to gain access to the unit, or viruses and similar unwanted items. PC or servers can be secured with user names and passwords, which should be at least six characters long (the longer the better), combining numbers and figures (mixing lower and upper cases). On a PC, tools like finger scanners and smartcards can be used to increase security and speed up the login process.
To protect against viruses, worms and other unwanted items, it is recommended that a good virus scanner with up-to-date filters be installed on all computers. Operating systems should be regularly updated with service packs and fixes from the manufacturer.
When connecting a LAN to the Internet, it is important to use a firewall to block or restrict traffic to and from the Internet, to filter information passing through the firewall, or to restrict access to certain remote sites.
More about network technologies and devices
Hubs, switches and routers
Hubs are essentially used as connection boxes to allow several pieces of equipment to share a single Ethernet connection. Usually 5-24 devices can be connected to one hub. If more devices are used, another hub can be added. To speed up the network, you can use switched hubs, switches or routers that allow several data packets to be transmitted simultaneously.
Bridges
If more than 255 devices (the typical network address range) are connected to the same network, the network needs to be divided into segments with a router between segments. Alternatively, a bridge can be used. Some switches have built-in router functions. For example, suppose an airport with two buildings using 170 cameras each needs to be connected to the same security centre several kilometres away. To be able to access all the cameras simultaneously, you would divide the cameras into two networks and connect them together with a bridge.
NAT routers
All devices connecting directly to the Internet must have a unique public IP address. Public IP addresses are sold by Internet Service Providers (ISPs). A Network Address Translator (NAT) can separate a LAN, with private internal addresses, from the Internet. A NAT can be a dedicated box or a program running on a computer.
Gateways
Gateways provide a convenient way to create a local network. A gateway works as a combined router, switch and NAT.
DHCP servers
It takes time to administer the IP addresses for large numbers of devices on a network. A DHCP server can reduce administration time and the number of IP addresses needed. A DHCP server automatically issues network devices with IP addresses when they connect to the network.
Domain name servers
In larger networks a domain name server (DNS) is included. This associates human-friendly names with corresponding IP addresses, and allows devices to resolve the friendly name. For example, a network camera monitoring a door is more easily remembered and accessed by the word 'door' than it is by its IP address. The DNS server will return an IP address such as 192.36.253.80 when given the friendly name 'door'.
For more information contact Roy Alves, Axis Africa, 011 548 6780, [email protected]

© Technews Publishing (Pty) Ltd. | All Rights Reserved.