
The introduction of IP-based security products has brought about a new, exciting opportunity for security companies. This new technology can be intimidating to an installer who is accustomed to traditional security equipment. However, installers can easily succeed by selecting a supplier that offers the right set of programs to help guide them through learning, selling and support techniques for IP systems. Moreover, just as leveraging technology can reduce a customers’ total cost of ownership, IP-technology reduces the cost and improves the effectiveness and efficiency of support programmes –for both the supplier and the installer. It has opened up a wealth of new tools to help installation companies sell new products.
In fact, partner programmes are evolving from being time, materials and cost intensive, to being efficient and effective at reducing the cost barriers that traditionally prevent a company from bringing on a new product line. The following article presents a few of the new programs and techniques that an installer can begin to expect to see offered from their IP-security distributor.
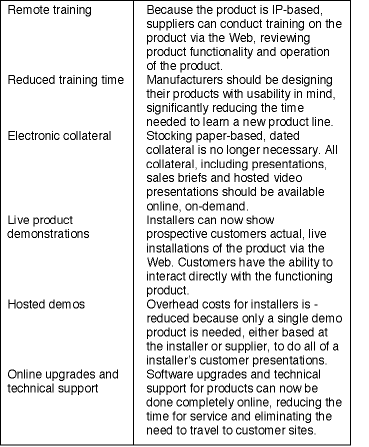
Remote training
An effective support programme should always start with the pre-sales effort by engaging the sales, applications and installation teams. An onsite visit from the supplier should be performed to review the product's significant features and advantages, as well as teach the sales team how to install and use the product for demos. However, a common problem encountered is that an installation company cannot get all of their personnel together at one time.
One of the significant advantages of working with an IP-based security product is that today's suppliers can now offer remote training. With only access to the web, both the supplier and the installer's team can log into the product together and conduct training over a speakerphone. It is in essence an instant Webinar with a supplier representative and one or more of the installer personnel actually interacting with the product through their Web browser. If the installer has the IP security product on site, then they can examine the hardware at the same time both parties are reviewing features and how to set them up.
Reduced training time
The most valuable aspect of the training on new technology may be its brevity. The enabling technology of the IP-based security systems greatly reduces the complexity and amount of time required for training. This is not at all by accident. Initial training for traditional security systems required lengthy, complex sessions to be able to understand and support it because the interface to every system is very different. With IP-based systems, every new product or feature design is crafted with usability in mind.
In these new systems, the fact that security installers no longer have time or resources to devote to ramping up new product lines has been considered. Successful manufacturers understand this and have designed their system with this consideration in mind. For example, technical training on today's typical Windows-based system usually takes two to three days to start with and requires additional training modules later on. This is because the structure of the software requires the learning of many complex and non-intuitive menus and hardware configuration schemes.
These courses require taking the staff out of the field and incurring significant expenses, as well as lost service revenue. Furthermore, many installation technicians require additional training to become proficient with Windows operating systems and database management systems. This is known as the ''90s syndrome', as everyone working in the field in the 1990s remembers the vast amount of training that was suddenly thrust upon technicians to become proficient with new Windows operating systems, software applications and networking and hardware. Many security manufacturers actually built profit centres around ramping up their dealer partners! Back in the '90s competition was not nearly as stiff as today and margins were better, so dealers could tolerate the costs and downtime. That is simply not the case anymore!
In contrast, many IP-based products employ familiar Web-based user interfaces common to e-mail and websites. Generally, users work with these products through a Web browser and the systems act just like a website with point and click navigation. Today, most people use the web so familiarisation with how to operate the 'head-end' is much simpler. In fact, there is no head-end PC software installation at all. Installers should expect the software to come already installed in the panel. Finally, field hardware is often plug-and-play so training time is dramatically reduced and can usually be accomplished in just half a day.
Electronic sales collateral
After training is completed a supplier should be providing installers with electronic outlines and PowerPoint presentations geared at providing demos and training their own customers. These can all be made available online, to be printed on-demand, or customised for the individual dealers. Additionally, hosted video programs on the manufacturers website can provide dealers and customers with professional Web casts that enable them to learn more about products at their convenience.
Live product demonstrations
Another significant innovation is live product demonstration support. Instead of carting around sample equipment, setting it up, and showing customers what a real system would look like, Web-enabled technology allows sales representatives to take customers to real, functioning sites (all over the Web) anywhere in the world to see how real customers are implementing the solutions.
This process may be done with supplier and installer personnel in the same room with the customer, but does not have to be. The supplier can be in one city, the installer and the customer in another and the live system or systems in still another. And, the customer will see just as effective, or perhaps even a better demo experience, as if they had travelled to the factory. In many cases, the customer can actually get to 'drive' the software themselves. Geography simply does not matter.
Vendor hosted demos
New technology has brought about the ability to give installers the ability to host these live demos. With a base demo system set up in either the supplier's headquarters or the installer's sales branch, any sales representative can show their customers the advantages of true remote management. This type of demo is available 24 hours a day and gives the installation company the ability to conduct countless demos in this fashion without needing to keep multiple demo systems in stock to bring to customer sites, if at all. In fact, many of the demo systems that installers purchase are actually installed to secure their own premises. These functioning systems are then used as the demo system to be able to show their customers what the actual hardware looks like and how the system functions.
System upgrades and technical support
Once a sale has been made, software upgrades have also become much more efficient. The existing process is for a supplier to send out a CD when an upgrade is requested and the installer will schedule the upgrade with the customer, go to the customer's site, install the demo and return to the office. This is normally a half a day service call, plus travel time.
Conversely, with an IP-based system, the technician - wherever he may be - simply logs onto the supplier's secured installer website from any PC, downloads the upgrade file to his desktop, then remotely logs into the customer's system and backs up, patches and updates the system in a process that can take less than 30 minutes.
Technical support
When an installer requires the support from the supplier for a particularly vexing problem, there are immediate options to get problems fixed. For example, instead of backing up databases to CD then sending them to the supplier and waiting another day for the manufacturer to analyse it, or worse waiting for the supplier to send someone out to the customer, the option exists for customers to temporarily allow access to the supplier tech support rep who logs in over the Internet. In fact, the customer, supplier and installer can all log in together and share a conference call to discuss the configuration and troubleshoot the problem. This allows for service calls to be measured in hours not days.
The demands on security installation companies to sell IP-based products have increased with the need to learn new technology and be able to convey the benefits of that technology to their customers. But this new technology has also opened the door to new installer support programs that suppliers should be offering to help their installers succeed. By teaming with the right supplier, a security installer will realise the same benefits of reduced costs, reduced time and increased margins that they are touting to their customers.
About the author: Nichola Allan is the technical manager of G2 Security which specialise in introducing innovative security products to South Africa. Nichola can be contacted via e-mail at [email protected] or by phone on 011 467 6339.

© Technews Publishing (Pty) Ltd. | All Rights Reserved.