
Third-generation solutions allow for expansion and integrated remote control of smaller sites.
Designing and deploying an integrated security system for mid-size companies is often like fitting a square peg in a round hole. Traditional integrated security systems were either designed for smaller, single-building installations or larger, multilocation corporate campuses. The systems were either hard-wired, single-facility systems or high-end, expensive client-server-based systems.
But the maturation of IP-based security systems is revolutionising the options mid-size companies have for installing and scaling their security systems as business expansion and acquisitions dictate, while containing operating costs at the same time. These new systems are based on 3G - third-generation - system architectures borrowed from the IT world.
Three keys to design
This paradigm shift in security offerings with today's IP-based security systems is made possible by incorporating three key elements into the design of products: application scalability, geographic independence and web-based architecture. These elements directly address the costs to install, administer and maintain a fully integrated system.
Application scalability, simply put, is the integration of a broad mix of security management applications into a single system. Common applications include video, visitor management, access control; alarm monitoring, intercom and temperature monitoring. Applications can be added at any time to meet the specific needs of the site.
Geographic independence is the ability to expand the product from a single system to a global network of systems regardless of where the components are located. This is especially important for businesses that grow by acquisition or that are expanding offices in remote locations. A critical feature for these customers is a system that allows the management of a mixed card population, avoiding the need to re-issue access credentials.
The third element of the product design is a Web-based architecture. Web-based architecture allows an application to use a common Web browser to deliver an easily understood and rich user interface. This means that not only are systems easier to learn because they behave like common Internet websites, but their use often does not require the installation of special software - the web browser is already there.
Some newer systems take these elements one step further by providing a solid-state implementation, meaning that they have no moving parts and thus have MTBF (mean time between failures) far in excess of systems that require traditional PC servers. Network-based solid-state systems that require more memory than conveniently fits can use network attached storage, available these days for very reasonable prices.
Scalability and complexity
As expected, when a business grows and the scale of a security system increases, the price and size of the system will also increase. These new 3G systems allow mid-sized businesses to expand their integrated security platform at their own pace, without having to 'over-buy' up front to enable future expansion.
In the scalability and complexity matrix (Figure 1) you can see that there are many security systems available to meet the differing levels of complexity and scalability. However, two significant problems are evident when looking at today's offerings.
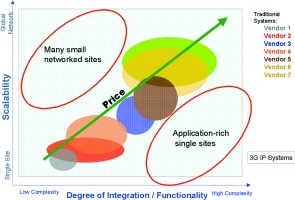
First, as a mid-sized company grows and moves up either axis, or both axes, it is forced to switch security systems. Second, in many cases, there is no simple solution available to meet the company's specific mix of scale and complexity. For instance, if a company grows by adding a number of small sales offices, it would have to buy a high-end system in order to acquire the features to integrate these individually simple small sites under one access control management system. Today's evolved 3G systems use communication over the Internet to drive down the cost of integrating multiple sites.
Mid-size company market drivers
Mid-sized companies will recognise the largest set of benefits of 3G IP-based systems. Mid-sized businesses differ greatly, though most tend to have annual revenues of between $20 million and $1 billion and employ between 100 and 1000 people. These businesses tend to go through the most changes via growth and divestitures.
Let us think about that. The security needs of a 100-person business and a 500-person business are very different. The infrastructure requirements of a $10 million company vs a $1 billion company are worlds apart. Due to their differences, these types of businesses have the greatest need for the flexibility and scalability that is inherent in IP-based systems. While statistically diverse, mid-sized companies have some common security needs that are driving today's security market.
Most commonly, mid-sized companies need to incorporate disparate facilities and sites into the enterprise security structure. Many mid-sized companies maintain small, dispersed facilities that do not have integrated security protection and are thus lacking the convenience and cost advantages of an integrated security system. These companies are looking to extend the enterprise security umbrella to include these locations to help manage liability and threat levels and to facilitate audit and control. However, the economics of small, integrated systems prevent their installation in multiple facilities.
A second market driver is greater management control over security. A substantial number of mid-sized companies are using smaller systems but require integration features that exceed those that are provided by low- to mid-priced security products.
Along with this increased control is the need to integrate new technologies, such as VoIP, into the physical security function. Mid-sized companies are increasing IT spending at a rapid pace; however, for the most part they are not actually increasing IT or security staff. Instead, they are looking for solutions that tightly integrate IT functions and that capitalise on their IT infrastructure to keep operating costs at a minimum.
The third market driver is, of course, cost. Many mid-sized companies have very specific high-end security requirements, but lack the budgets to implement top-shelf systems with their high installation and ongoing cost requirements. These companies are looking for systems that can reduce installation, maintenance and operation costs. IP-based systems offer lower total cost of ownership by sharing resources with IT yet integrating existing physical infrastructure such as readers and monitoring points.
Guidelines for purchasing security as a solution
The combination of these market drivers and the new technologies these emerging 3G systems require has transitioned the security purchase from a product purchase to a solution purchase. The following are a few of the key questions that mid-market companies should ask when selecting a 3G security solution.
* Does the vendor's applications roadmap align with your long-term goals?
* Is the integration of applications built into a product or pieced together from acquisitions?
* Can the dealer/integrator work with security, operations and IT in order to understand IT needs and installation requirements?
* Does the system provide security and authentication technology to safely connect remote sites over public Internet connections without requiring additional expensive IT equipment?
* Does the vendor's product support the standards your IT department will require (TCP/IP, XML, ODBC)?
* Do monitoring workstations only require a standard web browser (no application client software installation)?
* Is the security system hardware completely solid-state with no moving parts which lower MTBF?
The interaction of the security solution with existing and planned IT infrastructure is an increasingly important criterion that must be considered when purchasing a security solution. It is critical that security plans are aligned with IT expansion. One of the simplest ways to ensure that the solution will interact smoothly with IT systems is to select a vendor who has a history in both physical security and IT development. This IT integration requires a close consideration of both vendors and product attributes, to ensure that a solution will fit into a company's long-term IT planning.
Today's solutions offer mid-sized companies the opportunity to achieve the high level of security that they require, whether it be the tight integration of security applications, centralised management of multiple sites, tying together security with IT systems, or any number of customised configurations. With 3G systems, companies of all shapes and sizes no longer need to shop for the product that is closest to their needs. Instead they can select a security solution that meets their current and future needs.
The way forward
To address the above problems and many more, S2 Security Corporation, headquartered in Wellesley, Massachusetts, has developed the (3G) S2 NetBox.
The S2 NetBox is the first physical security management system to integrate access control, alarm monitoring, video, intercom and temperature monitoring applications in a small-form factor network appliance. The S2 NetBox utilises a new system architecture that moves advanced physical security capabilities to the network edge, eliminating the need for a separate PC-based server. This architecture makes it possible to deploy systems that scale from single facilities to multisite organisations - all over an IP network. See Figure 2.
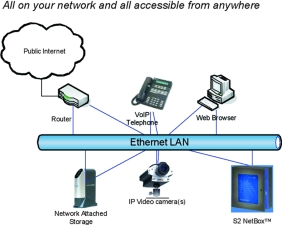
Unlike other integrated security systems, the S2 NetBox uses existing LAN, WAN, and Internet connectivity in place of proprietary wiring. Users interact with the S2 NetBox through a web browser, making it unnecessary to install or maintain software on any PC server or client - a feature we call 'zero-footprint software install'. The network connectivity and browser-based user interface (See Figure 2) of NetBox make the system completely independent of geography, enabling users and system integrators to perform monitoring, control and maintenance from any computer at any location with a network connection. Because the browser interface looks and operates like a website, users become proficient with little training. And of course, as it was designed from the ground up as a network appliance it incorporates all of the data security techniques, such as SSL, SHA-1 MAC encoding, etc, required to make it a good and secure network citizen.
For more information contact Phil Mailes, S2 Security Corporation, 0944 1483 852181, [email protected], www.s2sys.com

© Technews Publishing (Pty) Ltd. | All Rights Reserved.