
The key to big cost savings – or an invitation to big problems – have you considered the implications of using the public Internet to access and manage your security system?
Until recently, securing multiple sites within only a few miles vicinity with a single system required expensive leased telephone lines. Aside from the cost, often excessive for relatively short distances, the service was subject to interruption at the hands of the telephone company, or errant backhoe operators. Now, due to the adoption of the World Wide Web, we no longer consider such things; the Internet connects any place to any other place, regardless of distance, for a much lower monthly cost. If something were to go wrong with the Internet, chances are pretty good that the network will heal itself and your data will get through - probably without you even knowing that there was a problem.
Unfortunately, due to the availability and accessibility of this media, there is a catch: using the Internet to carry data can leave your systems vulnerable to malicious attacks by people you will never see. Fortunately, by taking some simple precautions, you can protect your system from most attacks and send the hackers looking for a victim at some other IP address.
The problem
The problem with using the public Internet for connecting anything, whether a PC at home or security system components at work, is the public part of the equation. Those old leased telephone lines might have been expensive and a little unreliable at times, but they were private. The Internet, in contrast, is publicly accessible. Where physical effort such as climbing a telegraph pole or digging (literally) was required to hack your old leased line, your Internet connection is vulnerable to anyone with some network knowledge, a computer, time on his hands, and the desire to cause trouble.
The consequences of your IP video cameras being viewed and controlled or your access control panels being hijacked by a hacker halfway around the world are significant. Failing to secure your data pathways is not just bad policy, it is irresponsible.
Solutions
Sending data securely over the Internet has several cost-effective solutions with the chosen one dictated by the application requirements.
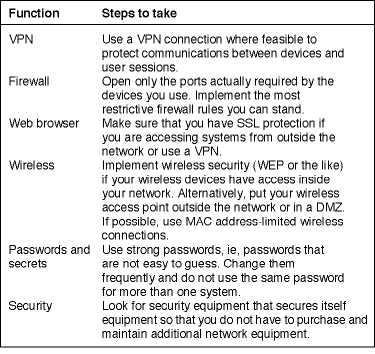
A VPN, or virtual private network is one common way to secure data over the Internet. The virtual part means that data is made private, as is the case in a private network, while still using the Internet to transport the data from end to end. VPNs create a 'tunnel' through the Internet by encrypting the data they transfer in a way that only the legitimate end points understand. Should this data be intercepted nothing is revealed. Tricking systems into accepting rogue commands, without the use of special equipment and knowledge of the encryption key, or secret, is not possible.
The real beauty of a VPN is that it is transparent to the devices connected to it; generally a piece of hardware running VPN software does the work. VPN-enabled routers used to be quite expensive, but consumer demand and mass adoption have led to low cost products from manufacturers such as Linksys, Netgear and D-Link. By far most of the equipment one encounters in the security industry, including network-capable equipment, has no facility for data protection. This includes access control panels, IP video cameras and the like. Therefore, VPNs form a convenient approach to the problem of protecting data and most large companies already have some sort of private network capability.
VPNs do, however, have a couple of downsides. First, they are not trivial to set up; unlike most routers that are completely plug-and-play, some knowledge of networking and data security is required to set up a VPN. Additionally, the encryption and decryption required to protect the data slows the data transfer rate. This is especially true of less expensive, consumer-oriented equipment. In the final analysis, though, the cost savings related to using the public Internet to connect equipment generally makes the investment in VPN equipment and setup worthwhile.
Another type of solution is available from some manufacturers: equipment that secures its own data communication. At least one manufacturer has access control panels that include data authentication capability. These panels include a message authentication code, or MAC, that is based in part on a secret known only to the panel and the system communicating with it. A unique MAC is sent with every message and the message recipient (which also knows the secret) calculates the MAC again and compares it to the one in the message. If they match, then the message is authentic, that is, accurate and from the expected sender.
Message authentication has the benefit that it does not require any special equipment; any network connection over a LAN or the Internet will do. Set-up is also easy; if the 'factory secret' is used, then there is no special set-up required. The limitation of this approach is that products must be designed with message authentication in mind, and the arithmetic calculations required to generate and verify MACs require faster processors than those found in some of the older products on the market. Nonetheless, expect to see more devices that are safe to connect to the Internet in the future.
Securing your browser
Most Internet-connected devices offer user interfaces that operate with web browsers. Securing communications with web browsers was accomplished early in the life of the Web, driven by the desire to use the Internet to carry consumer transactions, and uses a technology called Secure Sockets Layer (SSL). Without SSL, the data you enter in your browser is sent as is - in clear text - across the network. That means that user names, passwords, PINs and other sensitive data can be read if the message is intercepted.
SSL capability is built into your web browser. You will see the icon of a padlock in the display when SSL is in use, indicating that your communication is secure. Unfortunately, though, SSL requires more complexity and processor power than is available in many security devices. Also, users can become confused when their browsers display messages about certificates that are not digitally signed correctly, a common occurrence when SSL is used.
If both the browser and the device are on the same VPN, then SSL may not be required because the communication path is already secure. On the other hand, most hacking of corporate networks comes from the inside, and for complete safety an SSL-protected link is the best practice.
Utilising a firewall
One relatively easy way to increase the security of your network is to open only the ports that are required for the devices you are using. The default setting for most inexpensive routers is to block all ports inbound and open all ports outbound, therefore protecting your network from outsiders while letting you have open access to outside sites. This protection is part of the function of a network firewall. In order to access your security devices from outside the network, you will have to open ports in the firewall to permit the inbound traffic through. To an extent, though, the more ports you open, the more risk you accept.
Using the port forwarding functionality, available with most routers, to send traffic for the device you intend it to go to, only through those ports, is the best approach to making your security equipment accessible from outside your network in a secure way. If you have to open ports for unprotected functions such as telnet sessions, remember to close the ports once the activity that caused you to open them is complete.
Companies with better-initiated network infrastructures often have more sophisticated firewall equipment that can restrict communication between devices even further. In general, the more restrictive you can make a firewall rule, the safer it is for your data and for other applications on the same network.
Be wary of wireless
Wireless IP connections are incredibly convenient for connecting network devices. That said, of the most notable culprits in the world of unprotected data are the wireless devices. How often have you been able to see unprotected wireless access points in a hotel, office, or even at home from your laptop or PDA? These unprotected wireless access points are effectively a network point that connects directly into the LAN. Worse yet, an employee who - even innocently - connects an inexpensive wireless access point to a corporate network may not be detected for some time even though a giant hole in data security has been opened.
Some companies put their wireless access points on the unsecured side of their networks, which has the drawback of limiting the data that can be accessed. For others, though, it is essential to turn on some form of wireless security. The downside of using wireless security is that a code must be entered into every wireless device that participates, causing some administrative overhead. Additionally, the encryption required to protect the data, often leads to a decrease in the data rate. The consequences of failing to secure the wireless network, though, make it worthwhile.
Proceed, but with care
The ability to connect security devices using the Internet is fantastic in terms of its low cost and high productivity. As manufacturers build devices intended for deployment this way, there will be new and better ways to secure communications. Evolution happens. Technology from the IT world eventually makes its way into the physical security world.
Coming behind the first generation host-based systems in which all wiring was proprietary, and the second generation of client/server-based systems that use networks for interconnection of workstation clients to central servers is a new third generation (3G) that follows the current trend in mainstream computing that connects almost all processing to the network and manages it through a browser.
The way forward
To address the above problems and many more, S2 Security Corporation, headquartered in Wellesley, Massachusetts have developed the (3G) S2 NetBox.
The S2 NetBox is the first physical security management system to integrate access control, alarm monitoring, video, intercom and temperature monitoring applications in a small-form factor network appliance. The S2 NetBox utilises a new system architecture that moves advanced physical security capabilities to the network edge, eliminating the need for a separate PC-based server. This architecture makes it possible to deploy systems that scale from single facilities to multi-site organisations - all over an IP network.
For more information contact Phil Mailes, S2 Security Corporation, [email protected]

© Technews Publishing (Pty) Ltd. | All Rights Reserved.