
Despite the technology innovations that have occurred within the past 20 years, there are occasions when a security system may not actually meet the needs of customers.
Unfortunately, many customers discover this only after they have purchased and installed an inadequate system. At that point it is too late, because they have already made a substantial investment in hardware, software, labour, and training. Too often, customers are drawn in by what they see in a product demonstration, without understanding or focusing on the system's underlying architecture or design. The system looks good on a superficial level. Quite often a small system is installed and seems to perform well initially. But as the customer's needs change and the system grows, there are greater stresses placed on the system. It is then that hidden design flaws and limitations become much more apparent.
This article identifies the requirements for designing a modern security management system.
Distributed network design and the role of the access controller
Distributed network architecture means that each hardware component of the system is designed with its own processing and decision-making capabilities. Additionally, these intelligent system controllers are designed as a plug compatible network module. The access panel (access controller) is such a device and is the fundamental piece of hardware in a security management system.
In a well-designed security management system, the access controller is a self-contained, intelligent device, with its own local processing power and sufficient capacity to store a full database of cardholder and other information required to make realtime access decisions. Furthermore, the controllers should be good 'network citizens' and not add additional superfluous traffic onto a customers existing network.
The controller is the most reliable piece of hardware in a security management system, with a dedicated communication channel to its downstream devices (readers, alarm input and output points). There are potentially a very large number of downstream events generated in a system. If communication between the controller and the upstream devices (host computer for example) is unavailable (off-line), the controller needs to be able to store all the downstream events received, whilst offline, without losing or overwriting them, until communication has been restored. The controller must be intelligent enough to not only store such information, but to prioritise it as well. For example, events generated at certain critical alarm points might be of an extremely high priority, and would have to be transmitted to the host computer and displayed in the central station monitoring facility ahead of other alarms and events.
Host-controller communications
When the host computer communicates with the controller, it can send information either in single data record transaction or in a block of data as a single transaction. A well-designed communication protocol between the controller and the host system uses asynchronous, full-duplex communication, and sends and receives data to/from the controller in large data blocks optimised for network packet size. Using an asynchronous, full-duplex protocol, the host and controller can exchange blocks of data simultaneously without waiting for each other's responses.
Hardware-based design philosophy
Most security management system vendors were for many years involved in the manufacture of their own hardware. Along the way, they developed a culture in which their system design continued to emphasise hardware functionality and features. Those companies viewed software as a necessary evil, something they had to provide - for a nominal fee - in addition to the 'box.' This mentality was appropriate years ago, when systems were fairly simple and non-integrated. But modern systems are much more complex. They are more likely to be sold as either 'integration-ready' or integrated solutions, incorporating access control, credential management, visitor management, digital video, biometrics, smartcards and other diverse functionality (Figure 1).

It is the software
The basic functionality of an access control system is very simple. On a fundamental hardware level, all systems do pretty much the same thing. They have one central host computer (one or many communication servers), one or many access controllers, and many downstream devices with hundreds or even thousands of input and output alarm points. The host computer stores information for system administration, and downloads device configurations, cardholder records, etc. The controller makes access decisions, and uploads event information from the downstream readers and alarm points for monitoring of alarms and events. This basic functionality of hardware/firmware is the same for every manufacturer, and there is very little room for innovation or breakthroughs in new development. For this reason, a number of forward-thinking companies today have outsourced the manufacture of their controllers. What differentiates these controllers? The application software each uses.
The application software is the glue that holds a complex system together and makes it work. This has been true in all other realms of computing and electronics. Once a hardware technology is in place, it is the application of that technology, through software, that realises the potential and delivers the benefits.
Well-written application software is designed using modern object-oriented technology. This means that many lines of repetitive code are replaced with a reusable software object which becomes the building block of the application. Programs are smaller in size due to re-usability of objects. Well written application also use off the shelf libraries of standard objects and the latest technologies and tools available.
Open architecture and seamless integration
Open architecture is one of the most important requirements in designing a system that works for the customer.
Just what is open architecture? Open architecture implies that every major software and hardware component of the system, every communication protocol, and every interface is designed according to industry standards that allow easy integration with other systems and components (see Figure 2).
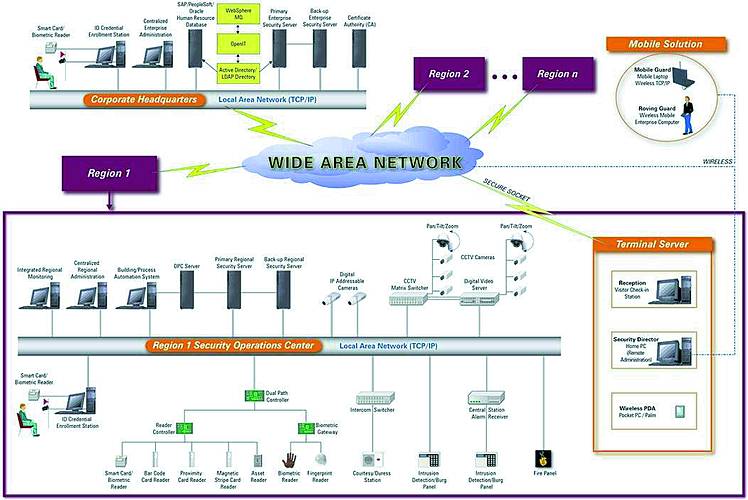
A well-designed security management system is based on an open design that relies on current de facto industry standards in software design, operating systems, networking, and databases for seamless integration with the corporate infrastructure. In terms of software, the system must support multiple database standards, such as SQL Server, Oracle and DB2. It must support multiple protocols, such as TCP/IP for network communication, XML for data exchange between different applications, SSL for secure communication, and LDAP for interfacing to directories and directory services.
The system should also provide a standard way of integrating with the outside world with other systems and devices. For example, the system must provide standard application programming interfaces (APIs) for ease of integration with different devices such as access control panels, digital video recorders, IP cameras, fire panels, intrusion controllers, intercoms, etc.
Customers have enjoyed the benefits of open systems in the computing environment for years. They want their security management systems to also be designed around accepted technology standards, so that they will not become legacy systems.
For more information contact Phil Mailes, Lenel Systems International, 0944 148 381 5230.

© Technews Publishing (Pty) Ltd. | All Rights Reserved.