
A new report by McAfee, a division of Intel Security, examines the controversy and confusion surrounding advanced evasion techniques (AETs), and the role that they play in advanced persistent threats (APTs).
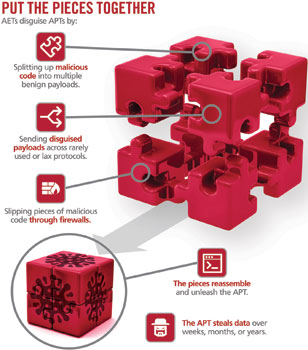
AETs are methods of disguise used to penetrate target networks undetected and deliver malicious payloads. They were first discovered in 2010 by network security specialist Stonesoft, which was acquired by McAfee in May 2013. Using AETs, an attacker can split apart an exploit into pieces, bypass a firewall or IPS appliance, and once inside the network, reassemble the code to unleash malware and continue an APT attack.
A Vanson Bourne study, commissioned by McAfee, surveyed 800 CIOs and security managers from South Africa, United States, United Kingdom, Germany, France, Australia and Brazil, and showed that there are misunderstandings, misinterpretation, and ineffective safeguards in use by the security experts charged with protecting sensitive data.
Recent high profile data breaches have demonstrated that criminal activity can still evade detection for long periods of time. Survey respondents acknowledged this and of the 13% of organisations in South Africa that suffered a network breach last year, 46% were the victim of known or suspected AETs. Global figures reflect one in five (22%). Nearly 40% of those breached believe that AETs played a key role. On average, SA companies who experienced a breach in the last 12 months reported a cost to their organisation of upwards of $500 000.
“Hackers already know about advanced evasion techniques and are using them on a daily basis,” said Carlo Bolzonello, McAfee engagement manager, EMEA. “What we’re hoping to do is educate businesses so they can know what to look for, and understand what’s needed to defend against them.”
“We are no longer dealing with the random drive-by scanner that is just looking for obvious entryways into your network. In today’s interconnected world, we are dealing with adversaries who spend weeks or months studying your public facing network footprint, looking for that one small sliver of light which will allow them to gain a foothold into your networks,” said John Masserini, vice president and chief security officer, MIAX Options. “Advanced evasion techniques are that sliver of light. When deployed, McAfee’s Next Generation Firewall technology adds an extra layer of depth to protect against such threats, making that sliver of light that much harder to find.”
Why current firewall tests hide the existence of AETs
42% of decision-makers in South Africa and nearly 40% globally do not believe they have methods to detect and track AETs within their organisation, and almost two thirds said that the biggest challenge when trying to implement technology against AETs is convincing the board they are a real and serious threat.
“Many organisations are so intent of identifying new malware that they are falling asleep at the wheel toward advanced evasion techniques that can enable malware to circumvent their security defences,” said Jon Oltsik, senior principal analyst, Enterprise Strategy Group. “AETs pose a great threat because most security solutions can’t detect or stop them. Security professionals and executive managers need to wake up as this is a real and growing threat.”
Of the estimated 800 million known AETs, less than 1% is detected by other vendors’ firewalls. The prevalence of these techniques has risen significantly since 2010 with millions of combinations and modifications of network based AETs having been identified to date.
Professor Andrew Blyth of the University of South Wales has studied the prevalence and impact of AETs for many years. “The simple truth is that advanced evasion techniques (AETs) are a fact of life. It’s shocking that the majority of CIOs and security professionals severely underestimated that there are 329 246 AETs, when in fact the total of known AETs is approximately 2500 times that number or more than 800 million AETs and growing,” said Blyth.
The reason these techniques are under-reported and not well understood is that in some paid tests, vendors are given the chance to correct for them. As such, only the specific techniques identified are corrected for, and not the broader techniques that are rapidly updated and adapted by criminal organisations.
“The need for companies to develop situational awareness is a key aspect in detecting these threats while validating that security tools acquired can prevent or detect these threats,” concludes Bolzonello.
Respondents whose organisations had experienced a network breach in the past twelve months estimate the average cost to the business to be $931 006. Australia, which reported a lower number of breaches at 15%, indicated a much higher average cost per breach at $1,5 million. The cost to South African respondents is on average $500 000. The hit to the financial services sector was the hardest, with estimated cost to be over $2 million per breach globally.
To download a copy of the full report, please visit http://www.mcafee.com/us/resources/reports/rp-security-industry-dirty-little-secret.pdf
© Technews Publishing (Pty) Ltd. | All Rights Reserved.