
Today’s security and facility managers are faced with increasingly complex technology to manage than even five years ago. Advances in information technology, particularly networking and digital capabilities, video technology and biometrics among others, have been difficult to keep pace with.
The effort to incorporate these advances into a complete facility or Enterprise security system is made more difficult by the fact that no one company manufactures all the components required in any one system. This is similar to desktop PCs. You may purchase a model that is a recognised brand, but open it up and you have components from many manufacturers. Unfortunately, in the security market, few manufacturers have the capability to put all of the components together into a seamlessly integrated platform that can be run through a single user interface from a manager's desktop.
Historically, interfacing systems was accomplished through hardware means with relays and black boxes. Later, dissimilar databases were stitched together to share information periodically. Today's requirements for detailed and realtime information and response have made these technologies obsolete. A modern robust security system needs to be able to incorporate all of the types of commonly used electronic system components (as shown in Figure 1) into one manageable, cost-effective and reliable system.
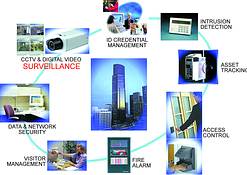
True seamless integration is accomplished by three major elements in a system:
1. A single database for all information storage. While data such as that from a human resources system may be imported into the security database, reliable integration requires the use of one database. Realtime data transfer between dissimilar databases is rarely flawless. Transferring data from a secondary system to the security database ensures the right information is available realtime when critical events occur.
2. A single user interface for all operations. Using different software from different companies and gluing together different user interfaces does not promote smooth operation or reliability. The key to seamless operation is the linking of critical events to a variety of information and response options. A single user interface is the key to making these complex functions easy for security officers to respond to and manage.
3. Open architecture. Most large security companies try to box in customers by requiring that they use proprietary hardware. This may seem safe in the beginning when you are surrounded by nods and promises from sales people, but ask anyone with a system more that 6-8 years old and they are probably experiencing some legacy woes in trying to migrate to new technology. No matter what the talk, if the system you are considering cannot work with more than one brand of network panel or digital video server, you are likely to get stuck in the future.
Understand that there are no widely used open standards in the security industry. Most open standards used are adapted from IT standards. That means, you need a leading edge system, designed on the latest platform technology and updated, typically twice yearly, in order to take advantage of all the IT advances as they become available. Most security companies only offer substantial upgrades every 18-24 months. Do not get caught with a slow mover.
Synergies
Once you have found an open system, only half the task is complete. The system cannot merely be open but must be designed and developed to embrace disparate technologies and bring them together in a sensible, practical way.
A suitable system embodies the 'Total security knowledge management solution' concept. That means not only are the major systems identified above truly integrated, but also that the whole is greater than the sum of the parts.
The best example of this is digital video management. Video is the most difficult technology to integrate into an access control and alarm monitoring system, but also perhaps the most valuable. The ability to record and preserve video footage of any suspicious activity is critically important in today's security conscious and litigious business environment. With a fully integrated video management solution, intrusion events and other access activity can be linked with video footage taken at the alarm location, without requiring any operator intervention. Imagine calling up an alarm from an alarm monitoring system, viewing the associated video, and then exporting the video and e-mailing it to the appropriate authorities - all from one system!
Other sophisticated integration includes access control combined with visitor management and asset management. Visitor management electronically manages visitors and visits to a facility. Using a front desk PC, receptionists could pre-schedule visits, assign visitors to specific employees, sign in visitors when they arrive, capture their photos, track them through the facility, sign them out and run a visit history report. Asset management could be seamlessly integrated into an access control system to manage and monitor physical assets throughout a facility. This would allow the tracking of an asset's current owner, the asset's history, the reader at which the asset was most recently and who currently has the asset. Asset alarms can be linked with the video such that when an asset is presented at a checkpoint, the system can record a video clip of the person at that reader.
Additionally, if a solution is based upon open architecture there is the ability to further integrate IT technology that has not traditionally been associated with security. Open IT programs allow security operations to integrate with the latest in digital certificate technology and LDAP compliant directories. This capability has important ramifications for network security and the use of smartcard technology. Here are some hypothetical scenarios that illustrate the kinds of integration opportunities that could be offered:
* When a cardholder account is created in an access control system, it would automatically create a Windows account for that person. The Windows account name would be derived from the cardholder name within the access control systems database. The access control system account and the Windows account are then linked to the same person.
* When a user's Windows 2000 or XP account is created, it would automatically create a cardholder account, badge, and access rights within the access control systems database. The access control system account and the Windows account are then linked to the same person.
* When a user's Windows or other Active Directory/LDAP account is disabled, it deactivates the cardholder's access badge in the access control system. The converse is also true, thus if a person is terminated their rights to enter a campus or building and access the corporate network are instantly revoked from a single point, ie, a check box with the cardholder record.
* If an employee presents their access badge at an entrance reader, therefore gaining access into the building, they are allowed to logon to their computer. If the system does not see any access activity, computer logon is denied.
Credential centre versus ID management
This high level of true integration and IT influence is radically changing certain elements of access control systems. For example, what used to be simply a traditional badging capability (ID management) is now a sophisticated central manger for all aspects of an employee's credentials (credential management) including ID badge, biometric information, PC log-on authority, asset management and smart card management, all from a single point!
Ease of use
Tight integration should allow for almost unheard of ease-of-use. Security operators are often less computer literate than the administrators who purchase or manage the system, but competent integration should make operations of even advanced tasks much simpler. For example some manufacturers have employed a 'two click' rule when developing their applications. This means that all viewing, interrogation and responses in the systems can be accessed and initiated through a maximum of two mouse clicks, thus the operator is unlikely to get lost in a hierarchy of menus. As there are multiple applications (modules) accessing a single database utilising a single graphical user interface, such a system is inherently more reliable than several separate standalone systems trying to carry out the same task.
Routes to market
When selecting a manufacturer be sure to visit their premises and evaluate their operations, and the deployment vehicle they choose to install systems. If the manufacturer is also an installer, be aware that you may be locking yourself into a single source of supply, which, in the long run, may be more expensive. If the manufacturer chooses to go to market via resellers, be sure that you evaluate the manufacturers accreditation procedures for their channel partners. Are resellers merely selected for the volume of business they can produce? Do they purchase off the page from a distribution house? Or are they evaluated for the value they can add to the product in the marketplace and the support they can offer? A good test is to verify that the manufacturer has a fully equipped training facility and that the resellers must be factory trained before they have access to the product.
Product selection
When considering the deployment of such a system evaluate the deployment vehicle, how many trained engineers do they have, what is their geographic distribution, how many similar systems have they installed and most importantly as we have been talking about integration and IT technology how IT concentric is that company?
Do not just stop here though, ensure that you visit a live reference site that is using the proposed solution in earnest and obtain the views of an existing end-user as to the reliability of the system, the ease-of-use and the support provided for it is all too easy to witness a 5 minute demonstration of a piece of software with some 'sexy' features without identifying some underlying flaws, which the salesperson is obviously not going to declare.
Conclusion
Whether you require one or many add-on modules, a fully integrated system can deliver a solution that best fits your growing security needs, all packaged in a single integrated system, with one database to manage and one user interface to learn. Additionally the reduction in duplication of servers, configuration and monitoring workstations, databases and user interfaces etc drastically reduces the total cost of ownership.
For more information contact Phil Mailes, Lenel Systems International, 0944 148 381 5230.

© Technews Publishing (Pty) Ltd. | All Rights Reserved.