

The surveillance strategy that is appropriate for any operation will consist of a number of functions or activities. These functions are important not only in defining what you are going to do, but also in setting up an appropriate departmental structure, clear job definitions and responsibilities, and appropriate manpower and training in order to carry out the objectives of the system.
The types of surveillance functions will require different levels of expertise. Activities therefore need to be consistent with formal levels of expertise within the department. A general principle is also to have a system of audit checks to verify the quality of surveillance. This is typically accomplished through a series of levels or tiers of surveillance. These tiers are also consistent with the levels of skill development and may provide a career path for operators entering the surveillance function. Some of the possible functions are described under general headings below.
Basic surveillance functions
* Camera patrolling: This is the detection of intruders or the presence of people in areas where they should not be. Camera patrolling can also led to the inspection of sites to detect incidents and the detection of events (eg diamond spillage).
* Remote escorts: Surveillance of personnel walking through or working in an area. This could be aimed at detection (eg theft while in an area), or protection (eg remote escorting of tourists through known crime spots).
* Picture comparison: Verification of the identity of personnel requiring access to areas.
* Camera checks: Checks that cameras and system are working.
* Direct incident detection: Live surveillance aimed specifically at the detection of incidents where people are in working areas or to detect scenes in public areas. This could include theft of articles, nightclub violence, or visual searches.
* Incident handling: When an incident is detected, responsibilities need to be allocated for continued tracking of the parties to the incident while also arranging and controlling a police or security response to the incident. It is difficult for a single operator to do both of these simultaneously and ideally there needs to be some kind of 'handover'.
* Verify compliance to rules/work procedures (eg casino table procedures/diamond sorting). This is an essential part of the casino environment, but companies like DeBeers have also implemented 'rules-based systems' that provide a structured basis to guide people's actions in high-risk areas.
* Monitoring of high risk situations in the production environment: Certain high risk activities are likely to occur within any environment. When these occur, more intensive surveillance should be directed at them. This could include things like cash (or goods) in transit transfers, occasions when working with objects such as gold, high value casino chips, or volatile public situations). This kind of surveillance may require expertise knowledge in the critical area.
* Alarm inspection: Live inspection of alarms generated through motion or infrared detection. These usually display on monitors automatically, either through blank screen technology or on allocated monitors.
* Recording of suspicious behaviour: Behaviour that seems out of place or inappropriate, but does not clearly show an incident should be recorded for follow up by more senior personnel.
Advanced surveillance functions
* Dedicated surveillance on specific suspects: This can be referred to as directed, focussed or targeted surveillance. It involves the tracking and in-depth surveillance of suspects including their behaviour, movement and contacts. Often such surveillance is driven by intelligence or profiling information. This can occur both in work and public environments.
* Coaching/training: Coaching of other operators, particularly junior personnel on surveillance techniques and situational awareness of what is happening in those sites.
* Profiling of individuals: This involves profiling individuals' behaviour, characteristics and even lifestyle to identify anomalies or signs of involvement in criminal dealings. Key to this is having an acceptable and ethical set of criteria for profiling. With such profiling, changes or out of the ordinary behaviour can be examined more closely to see if these are related to incident conditions.
* Profiling of situations: Situational profiling can reflect two major themes. The first of these is to establish normal benchmarks of performance or behaviour. This then allows one to recognise anomalies or breaks in the normal process. Secondly, profiling of unusual events within a specific location provides the basis to assess the risk within these situations. A number of occurrences or events, for example, may lead to the identification of a theme or consistent elements. One would like to establish things like whom is involved, when and what time it happens, and actions that occur. This may lead to identifying hotspots or directing surveillance on certain people when they are in those situations.
* Crime profiling: The more one knows about techniques and methods of a particular kind of theft, the better one is prepared to detect it. Crime profiling involves building up these signs for different criminal incidents to make it simpler to detect the crimes when they occur.
Auditing functions
* Review and auditing: This auditing generally occurs at a higher level than the initial operator viewing. This is because such an audit function requires greater expertise in order to pick up incident conditions. Typically, the increased expertise, the time available to repeat viewing of suspicious scenes and the option of slow motion replays will lead to a appreciable rate of detection of incidents during review that are not initially picked up. However, review has a critical quality control function in the following areas:
• verifying views of first tier viewing (what is covered and not covered)
• verifying integrity of first tier viewing (quantity and quality of detection)
• inspecting camera views not covered live by first tier.
* Alarm reviews: This is the systematic offline review of alarms generated by the system. This is sometimes addressed through a video management system that logs the alarms and initial few seconds of video to allow evaluation of the causes of the alarm. Whether such reviews are done manually or through automated systems, causes of alarms need to be addressed as part of a programme to reduce alarms to manageable levels.
Specialist functions
* Reconciling risk profiling across areas/time and people: Trend and pattern analysis of information from multiple sources to identify risk areas and people.
* Maintenance of individual profiling database and identification of investigation needs.
* Identification of targets: Identification of targets for dedicated surveillance and developing strategies for syndicate detection.
* Crime pattern reports: Analysis of incidents and implications for surveillance strategy and planning.
* Evidence handling: Handling and preparation of case for detected incidents.
These functions or activities can be allocated into a 'tier' system based on requirements of the organisation. As indicated, the functions themselves, and the way they are organised into 'tiers' will vary from operation to operation. Indeed, some operations may only have a single tier position, although a number of activities would have to be sacrificed as part of this. Table 1 provides a guideline for this allocation.
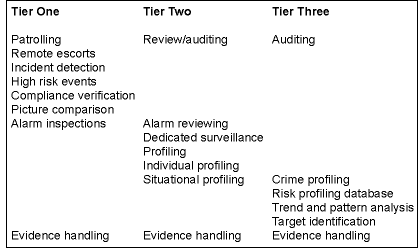
Full implementation of all functions outlined above requires a strong commitment of resources. For most operations, priorities and the nature of surveillance will determine what gets covered. It is probably better, however, to do less things well than to try and cover too many options with insufficient resources so they cannot be addressed effectively. The use of business applications and process enhancement is also an area that can be addressed but is not included in the table.
This is why the early definition of a surveillance strategy needs to consider how the CCTV system is going to be used so resources, people, and the work infrastructure and procedures can be aligned effectively in order to achieve the required objectives.

© Technews Publishing (Pty) Ltd. | All Rights Reserved.