
Organisations worldwide are implementing drastic cost-saving measures, such as pay and staff cuts, to counteract the current global economic slump.
However, many still overlook one of the more costly areas within their operations: communications. A common problem is that of using mobile phones when relatively inexpensive two-way radio technology can be substituted
According to Nik Patel, Business Manager for Motorola CGISS Middle East and Africa, many companies are ringing up unnecessarily high communications bills because they view two-way radio as an antiquated technology that lacks functionality and has no place in today's hi-tech world. To prove this point, Motorola commissioned a survey by BMI-TechKnowledge to investigate the levels of awareness and identify the cost of talking among some large industry players.
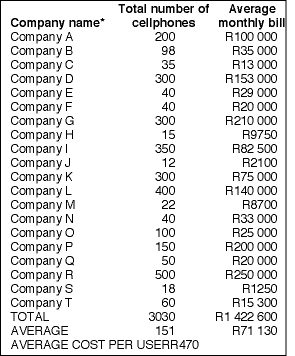
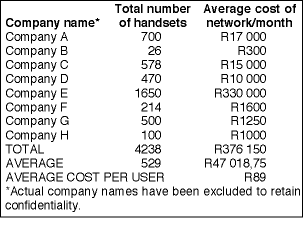
"Of the 20 nonuser companies interviewed, only a third had done a cost comparison between two-way radio and cellular telephony. The number of cellular phones per company averaged 151," remarks Patel. "If you then look at the average monthly cellular costs, it amounts to R71 130 per company (an average cost of R470 per user). Compare this to the companies using two-way radios (where the average number of two-way radios was 529 per company) that had an average monthly cost of R47 000, which works out to R89 per user per month."
Referring to the tables, we see that Company R (Table 1), for example, has 500 cellphone users and pays an average of R250 000 per month. Company G (Table 2) has 500 two-way radio users and pays R1250, thus saving R248 750 per month.
Company O (Table 1) has 100 cellphone users, which costs R25 000 on average each month. Compared to Company H (Table 2), which has 100 two-way radio users and pays an average of R1000 per month, Company O pays an additional R24 000 each month. So, the more users you have, the greater the saving with two-way radio technology.
The reason two-way radio is such a cost-effective communication tool is the fact that users pay a once-off fee for setting up the network, which can include base stations, repeaters, accessories and handsets.
After this, they only pay an annual licence fee which depends on the number of frequencies used, repeater sites and number of handsets. So while the initial outlay may be higher than that for cellphones, the real saving comes from the absence of monthly call charges. Two-way radio users do not pay for the cost of a call, whereas cellular users pay a monthly contract fee and a fixed rate per unit per call."
While two-way radios do limit communications to pre-determined talk groups, and therefore do not allow users access to people who are not on the network, they are the ideal communications technology for group communication on site. Unlike cellular phones, the average range of a two-way radio is 2 km for a portable and 20 km for a mobile radio operating on line-of-site. However, this can be extended significantly using repeaters to create a local area network.
"We are not advocating the replacement of all cellular phones with two-way radios because they are two very specific technologies," says Patel. "We are saying that in certain environments two-way radios are a more effective, efficient and economical alternative.
"With features such as emergency signalling that sends a help signal to a pre-defined person or group of people; a lone worker function, which causes the radio to enter emergency mode if the user fails to respond to a warning signal; alphanumeric phonebooks, call forward, voice messaging and missed call alerts, the two-way radios available today have far more functionality than their cumbersome predecessors," he concludes.
For further details contact Nik Patel, Business Manager, Motorola CGISS on tel: (011) 800 7800.

© Technews Publishing (Pty) Ltd. | All Rights Reserved.