
Intelligent, ‘human-critical’ networks built on 5G technology stand to make every aspect of our lives smarter, safer and more sustainable. They will combine high data rate, instantaneous communications with low-latency network performance and massive connectivity, enabling new applications for everything from eHealth and autonomous vehicles to smart cities, smart homes and the Internet of Things (IoT).
The more we depend on networks, the more we need to make sure they’re protected. The next generation of networks will have to be more secure than any that has come before. Instead of being applied ‘to’ network services after the fact, security will need to be ‘built in’ from the start – with the entire network acting as one giant, unified sensor to keep infrastructure and services safe.
Security must keep up with network services
With 5G, there will be more networks doing more complex things and delivering more kinds of services than we’re used to. ‘Slicing’ will become the norm: virtualisation that allows network resources to be shared with third parties, with guaranteed quality of service (QoS) and isolation. Having end-to-end slices that terminate in private networks will increase the attack surface service providers need to protect: beyond securing the network as a whole, they will have to protect every individual slice, each with its own distinct requirements.
Another change that will require providers to fundamentally shift how they think about security is the nature of the services themselves. Today’s network services tend not to change once they’ve been designed, and they operate more or less in isolation from each other. They’re static and siloed. But slice-based 5G network services will be incredibly dynamic, responding to evolving conditions in real time.
For example, imagine a remote worksite with autonomous vehicles transporting people or materials from place to place. To keep passengers safe, those vehicles need to be able to respond very quickly to shifting conditions – whether that’s avoiding a herd of animals on the road or adjusting for weather-related hazards like flooding or black ice. Some of this will happen inside the vehicle and some of it will happen in the network. Vehicles’ onboard sensors and processors will combine with the network and control mechanisms in a single, end-to-end ecosystem. Security has to extend across this entire ecosystem and be as flexible and adaptive as the services it’s protecting.

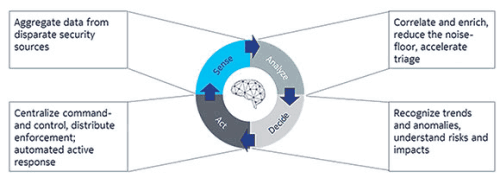

Analytics and automation are vital
What does flexible, adaptive, end-to-end security look like in a 5G scenario, and how can service providers build it in from the start?
The first prerequisite is visibility from the device up through the network and into the cloud. Without the ability to collect, correlate and analyse data from end to end, security threats could easily be missed. In a way, with 5G the entire network becomes a sensor (or, really, a series of sensors), drawing data from various systems and devices to provide a complete, comprehensive, real-time view for maximum security.
5G security operations also need to be predictive and automated. That means using machine learning, multidimensional analytics and threat intelligence to correlate data from multiple domains and sources, catch anomalies, provide contextual intelligence about threats, weigh business risks and recommend (or enact) mitigation steps.
Analytics are important because many threats are designed to stay undetected for as long as possible, under the radar of the network security operation centre or hiding in the information noise of minor, relatively harmless attacks. Machine learning and artificial intelligence (AI) can discover these kinds of ‘lurking’ malicious activities and trigger countermeasures.
Embedding security in the network
While firewalls and other defences will still be important to help stop hackers before they access the network, attacks will inevitably get through. This is especially true in 5G because the network will not have conventional boundaries: it will be an open ecosystem in which all kinds of unmanaged third-party devices are connected.
Strong security should be provided within the network to protect data and infrastructure. Integrated security workflow automation and orchestration are key to this, transitioning from static defences to agile, adaptive, accurate threat responses.
Ultimately, these security capabilities add up to a set of required applications: active monitoring and workflow orchestration, privileged access management and analytics of user behaviour, certification and management of digital identities of network entities, machine learning of traffic patterns for threat detection, automated incident responses, and more.
Designing for security
Service providers want to engage the market and monetise the investments they’re making in their networks to deliver on the new 5G use cases. As they do, they will need end-to-end security performance – at scale, from the edge to the core – to defend against advanced, persistent threats. The new 5G security approach integrates and automates 5G network security by treating the entire network as a sensor. Data taken from existing systems is used to give a much greater level of information. For that, security must be provided at four key layers.
At the base level, security must be in place for both the service network and the cloud infrastructure. Moving up the stack, the entire infrastructure – spanning software, virtual machines, hardware and devices – also needs to be ‘trustable’. Automated security management and orchestration provide frictionless security across all these dynamically changing elements, and all sensitive data must be secure, providing access control, privacy and regulatory compliance.
Finally, to proactively detect and respond to security threats, security-related intelligence must be shared across all the parts of the network, among suppliers, partners and customers.
At Nokia, we’re working with standardisation bodies, partners and customers to build integrated 5G end-to-end security that applies across all the layers of the network. We also have an advanced security testing and verification laboratory to address the critical security needs of end-to-end networks.
The job of security teams in the 5G era will be to limit how and where hackers can attack networks and services. They’ll also need to be more accurate in determining which threats are real and which can be ignored, and speed up mitigation when a defensive response is needed. We’re committed to providing to provide a robust 5G infrastructure that is resilient for these new apps and services.

© Technews Publishing (Pty) Ltd. | All Rights Reserved.