
The Dark Web is a hive of illicit activity. From illegal guns and drug dealing, to the Ransomware-as-a-Service programs, buyers and sellers can use this medium to trade and exchange both knowledge and products. That is, of course, until the long arm of the law swoops in and shuts them down.
The take-down of such Dark Web market places, Hansa Market and Alpha Bay, by law enforcement agencies in the US and Europe, made headline news not so long ago and served as the latest example of how this cat and mouse game works. It was not long, though, before threat actors shifted to new channels to evade authorities. It quickly appeared that they could use the increasingly popular mobile messaging app, Telegram, to continue their trade.
Hacking forums have long been a popular platform and an important means of communication among threat actors as they allow them to publish job offers, market their products and even consult with each other.
Sometimes, large operations and campaigns that cannot be carried out by one person necessitate the formation of a team to share the workload. In other cases, malwares and tools which have been crafted for malignant reasons are traded or sold to affiliates in order to generate revenue without the need for the developer to be involved in the attack itself. Threads in hacking forums are filled with similar examples and more, showcasing their significant role in fifth generation of the cyber threat landscape.
In the past few years, however, with law enforcement agencies having a better understanding of the challenges they face out in the wild, the grip on some of these forums has become tighter. Security researchers have been able to trace several threat actors by their activity on such websites, and authorities have managed to take down forums.
While there are still numerous websites operating under the same premise in both the Clearnet and Darknet, the previous examples indicate just how vulnerable these sites can be. Indeed, their users seem to have reached the same conclusion too, as well, as a migration to a more secretive and easily-accessible platform is currently taking place.
Migration to Telegram
Telegram, an encrypted instant-messaging application, introduced in 2013, experienced a meteoric rise in subscribers (five million new users in just 24 hours) following a server crash on the WhatsApp messaging platform. Similar to WhatsApp, Telegram users can chat to individuals as well as groups. What sets it apart, among other features, however, is the pride it places on its enhanced security capabilities. As a result, some of its hosted chat groups have become a useful alternative to the secretive forums on the Dark Web.
Telegram’s hosted chat groups, known as ‘channels’, can be used to broadcast messages to an unlimited number of subscribers, and, while their entire messaging history can be viewed, any response to the public messages is held privately. The discretion these channels thus provide goes a long way to help disguise their malice. Any threat actor with a shady offer or conversation to start can enjoy private and end-to-end encrypted chats instead of the exposed threads that are seen in online forums.
If, in the past, several steps were required to ensure an anonymous connection to TOR, today any Telegram user can easily and quickly join channels with a single tap on their phone and start to receive notifications of clandestine conversations and offers directly to their smartphone, all while keeping their identity completely hidden.
Telegram channels
A region in which these shady channels are flourishing is Russia and some have already attracted thousands of subscribers. Such examples are ‘Dark Jobs’, ‘Dark Work’ and ‘Black Markets’, though there are also many more.

As the names suggest, messages within the ‘Dark Jobs’ channel usually contain dark job offers that are colour coded. If a job posted in this channel is dangerous and likely to entail legal risks, it is marked as ‘black’, whereas less threatening jobs are marked as ‘gray’ or ‘white’.
The channels are not restricted to recruiters and job-hunters, though, but also advertisements for the sale of stolen documents or hacking tools. This is especially worrying, considering the accessibility of the channels and the promises of high salaries made to those who might otherwise refrain or have no way to reach these markets.
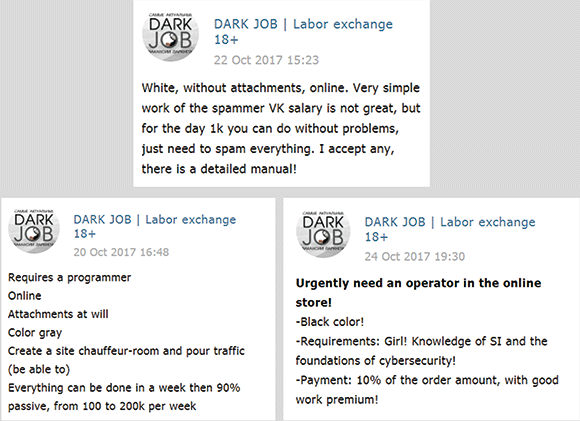
Ad copy that is often used in such messages to attract people into taking these kind of jobs are: “Are you tired of living in your mother’s basement?”; “Girls like guys with money”, and other imprudent sentences. The quick profit offered by these advertisements may well convince channel members to take the lucrative, albeit sketchy, shortcut instead of the strenuous career path.
As a result, this poses a risk of growth in cybercrime rates as these positions are not only openly marketed, but are also available to inexperienced users, making dangerous tools now within anyone’s reach.
Employees
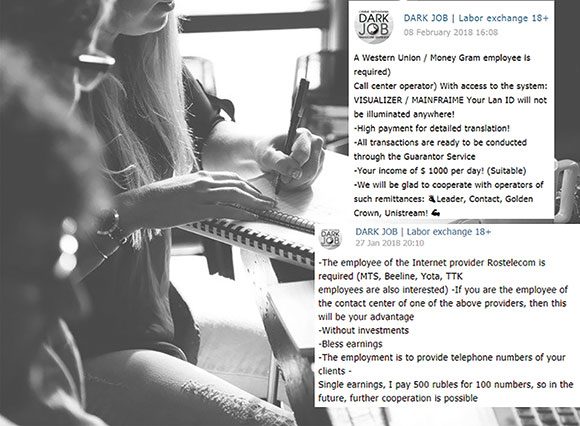
The most interesting messages are perhaps those looking for employees of certain companies or banks. Threat actors might take advantage of these employees in order to obtain insider information and sensitive data that is unavailable to the public. This inside information could then be used for personal purposes or sold, or to conduct a cyber-attack from inside the company.
This would thus eliminate the efficiency of some security solutions. After all, having someone ‘on the inside’ is a very powerful tool. Just like in the real world, in the world of cybercrime it can often be not what you know but who you know.
Cellular operators’ employees are highly sought after and one of the excerpts explains why. Staff in such companies can be used to acquire a large amount of phone numbers. Other posts suggest that they can be used to collect personal information and call log data of a customer.
Another eye-catching job posting is one that is looking for employees of Western Union or Money Gram that have access to certain systems. Allegedly, the employees will be paid $1000 per day for their efforts.
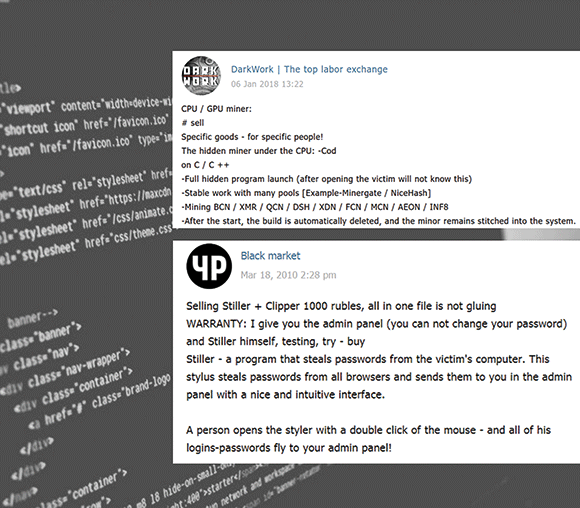
Hacking tools and services
“Wanted for a dark project: Cryptor running on all systems from Windows XP to 10. Bypassing the top AV especially Avast and Defender.”
This and many other messages are a perfect example of how someone with no prior experience in malware development can run an entire operation by leveraging Telegram channels. In this case, whoever is behind the advertisement is outsourcing an entire project and is in charge of only the payment.
Novice users can also come across messages promoting stealthy crypto-miners that will run without the victims’ knowledge in exchange for 600 rubles (about R120), or even infostealers that collect documents, screenshots and passwords in exchange for 1000 rubles (about R200). This is reminiscent of closed and hidden forums in the Dark Web where users published Ransomware-as-a-Service among other malware families.
Official documents
Other illegitimate services in some of Telegram’s more crooked channels, include forging legal documents. As you can imagine, Photoshop experts and freelance designers are in high demand in these markets.

Counterfeit documents include IDs, passports, banking documents and more. The author of one of the posts even claimed to have connections inside the Russian Traffic Police Department and to be able to issue or update driving licences of all categories. Scans of passports from all over the world are also available to those ‘who want to take out a loan’ and are in need of documents for verification purposes. These transactions and others often employ the services of a third-party (guarantor) to ensure that the deal goes smoothly between the buyer and seller and that everything is in order.
[To see something similar in South Africa, watch https://www.youtube.com/watch?v=25cDkmyoItA (short URL: securitysa.com/*emfr1]
Global phenomenon
Russia is not the only country in which those channels are gaining popularity though; having observed similar channels in other languages, our analysis points to this method becoming a global trend.
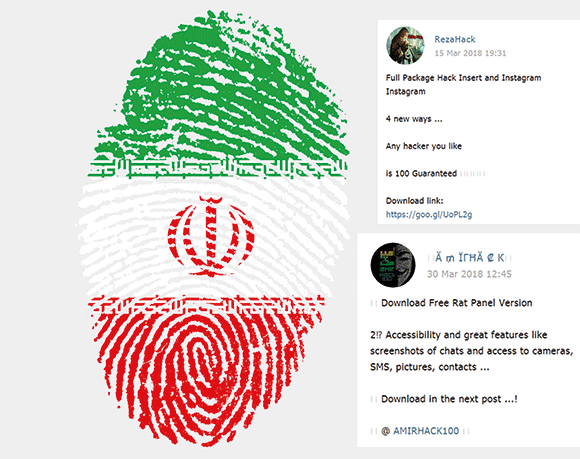
Some channels in the Arab world and in Iran, such as an Iranian channel by the name ‘AmirHack’, have more than 100 000 subscribers. These channels, however, seem to be more focused on the distribution of hacking tools and compromised accounts than their Russian counterparts. The screenshot (Figure 1) shows how two channels marketed a RAT panel as well as a tool to hack into Instagram accounts.
Conclusion
The convenience of Telegram channels allows for threat actors and those aiming to take part in cybercrimes to communicate in a more secure and easily accessible manner. Sadly, although messaging applications have become an integral part of modern life and improved over the years to ensure the security of their users’ information, they are also being taken advantage of by those fleeing from prying eyes, and the law.
Through the use of such tools, access to malware has never been easier, personal documents and certificates can be spread to unknown destinations and companies can be threatened by their own employees. Indeed, even with the limited skillset required, the number of threat actors is on the rise and it is no wonder that the number of cyber-attacks on both organisations and individuals is growing.
This article was provided by Check Point Software Technologies.

© Technews Publishing (Pty) Ltd. | All Rights Reserved.