

Total cost of ownership (TCO) is a well-established concept in many industries, not the least in IT, as a way for strategic buyers to move beyond looking at the upfront price to understanding all costs associated with procuring, deploying and operating a system.
In a previous article (https://www.axis.com/blog/secure-insights/tco-security-systems/), we presented a model for TCO in IP security and how that applied to a hypothetical project. The project was an enterprise 1500-camera city surveillance deployment. In this example, the costs for the project were divided equally between product related costs and ‘other’ costs – such as labour – not related to the specific price of the products purchased.
How TCO can help buyers
Over the past year, from working with the TCO approach at Axis, we can see two clear benefits for adopting TCO when buying products:
1.) The TCO allows you to look closely at your long-term commitment with the system and identify areas of improvement. For example, if the TCO shows that labour costs in operation make up a large share of the costs, perhaps it would be worthwhile to look at automating certain processes.
2.) The TCO creates a better foundation for comparing proposals from sellers and making a more informed decision. Instead of focusing only on negotiating the upfront price, you can see how to reduce your total cost of ownership, and challenge vendors about other costs that the system will incur – costs that are probably as big as or even bigger than the initial price. For example, in the article Total Cost of Ownership: Factors to Consider from 2015 (https://software.intel.com/en-us/articles/total-cost-of-ownership-factors-to-consider), Intel stipulates that 70% – 80% of the cost of an IT system comes in the support phase.
Using TCO for better business decisions
To understand the usefulness of TCO, let us look at a simple example. A buyer is considering two different systems: vendor A and vendor B. Vendor A is a premium supplier, with a higher upfront price but more long-term reliability, while vendor B is a lower-cost option with less focus quality and operation. In the left graph (Figure 1), only price is part of the picture, and clearly, B offers a lower price.
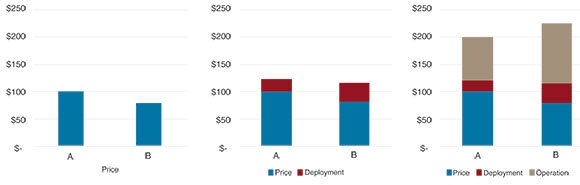
In the middle graph, deployment costs such as installation, training and project management have been added. Let’s assume that A can demonstrate that its system can be installed faster and requires less training. For example, vendor A offers more advanced design and installation tools that speed up deployment. Or vendor A’s products come out-of-the-box ready to mount, while vendor B’s products are shipped in pieces that need assembly. The total costs are now similar for A and B, with a slight cost advantage for B. But it still only shows costs that occur during the first year.
In the graph to the right, we look beyond year 1, across the whole expected lifespan of the system. We add operation costs, maintenance, failure and other ongoing costs. Let’s assume that A provides credible argumentation that system A requires less maintenance, has a higher uptime, and lower power consumption. For example, vendor A could prove that the products are field-tested to work in the customer’s environment, or provide case studies that demonstrate low failure rates. Now, the TCO shows that vendor B is more expensive over the lifetime of the system.
In the white paper ‘Unpacking best value from 2012’, (http://www.vestedway.com/wp-content/uploads/2012/11/TCO-Best-Value-White-Paper.pdf), the authors present a case from SKF, which uses a similar model to explain the cost difference between competing solutions.
The evolution of TCO
Over the past years, the TCO concept has evolved and matured. As more factors are brought into the scope of the TCO, it becomes even more useful as a methodology for understanding the complete investment associated with a system.
Of particular interest to the security industry is the discussion around cost of risk. In the 2012 white paper mentioned above, the authors argue that costs associated with various risks are real and should be factored into any TCO decision. An illustrative example, quoted in the paper, is the toy company Mattel, which was fined $2.3 million for importing products from Chinese suppliers that violated US standards. In addition to the fine, Mattel had to recall 20 million products, not to mention the costs associated with the loss of consumer trust.
Risks to consider
Risk management is of course a science in itself and your company needs to find its own method to assess the probability of various scenarios and the potential negative impact of those. But regardless of methodology, we would argue that the cost of risk should be considered as part of the TCO and thus impact the buying decision.
Here are a selection of risk areas that should be of particular interest to you when considering a purchase:
• Risk of losing critical business data. For example, if you have a camera system for loss prevention integrated with point-of-sales systems, you expect to get reliable video for each transaction. If the system goes down and you have no video for your transactions, what are the costs?
• Risk of cyberattacks. What would be the cost to you if your system is attacked, leading to system downtime, loss of data, and, perhaps most damaging, lost customer trust?
• Risk to your brand. What would be the cost to you if it turns out your supplier is not meeting sustainability standards, whether in environmental, social, economic or ethical aspects? How would that impact your brand?
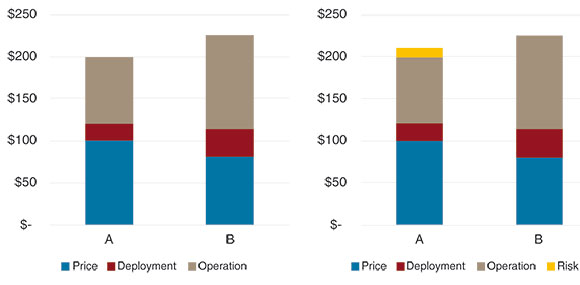
Let’s assume that the buyer in our previous case has made a risk assessment and further qualified vendor A and B from a risk perspective. In this case, vendor B is considered a greater risk for the buyer and the cost for that is added to the model in Figure 2 above. Now, the arguments for vendor A are even stronger.
Five things to consider
Working with TCOs might seem complex, but it doesn’t have to be. We recommend starting small, with factors that you can quantify and that you believe are important, and then expand over time. Here are five steps to get started:
1. Scrutinise price. Take a close look at what is actually included in the price. Does one product require mounting accessories, while the other is out-of-the-box ready? Does one camera model need additional lights, while the other has enough light sensitivity to manage without?
2. Look at key factors in deployment. How easy or difficult is it to install the system? How easy is it to integrate with your existing systems? How much training will your staff need?
3. Look at key factors of operation: How much time will you need to spend on maintenance? What are the typical failure rates? Be on the lookout for costs appearing in other parts of the system – for example, an IP camera system will likely require you to expand your network and storage, so products with high bandwidth requirements will increase your costs. And what about costs for power consumption?
4. Look at ‘hidden’ costs. For example, how easy will it be to change and adapt your system in the future? How much time will your staff spend on using the system? Are there freight or warehouse costs?
5. Look at cost of risk. What are the key risks with the systems? Even if you can’t fully quantify the cost of the risks, at least identify the risks and weigh them carefully into your business decision.
Additional benefits of TCO
In this article, we argue for the importance and usefulness of TCO as a tool for strategic buying, a fact that has been proven in many industries.
The TCO method has another great benefit: it provides a foundation for a discussion around the value, or the return on investment (ROI), of the system. In a future article we will look closer at the relation between TCO and ROI, and how to estimate value.
This article is available at https://www.axis.com/blog/secure-insights/tco-evolvement/ (short URL: securitysa.com/*axis2).
For more details on the TCO and ROI methodology and for a closer look at some case stories, please download the Axis white paper ‘Maximizing the ROI of your IP security system’ at www.axis.com/global/en/solutions-by-industry/total-cost-of-ownership/download-white-paper (short URL: securitysa.com/*axis1)
For more information contact Axis Communications, +27 (0)11 548 6780, sasha.bonheim@axis.com, www.axis.com
| Tel: | +27 11 548 6780 |
| Email: | marcel.bruyns@axis.com |
| www: | www.axis.com |
| Articles: | More information and articles about Axis Communications SA |

© Technews Publishing (Pty) Ltd. | All Rights Reserved.