

Andre Mundell discusses various aspects included in a comprehensive security risk assessment.
Security risk assessment, this is a term that is not really understood by people in the private or corporate sectors. You need to understand this term before you will grasp the full scope of a security risk assessment. The risk assessment is that little bit extra that you do in order to find out what your actual risks are.
A security risk assessment is a realistic, thorough and intelligent approach to security as a preventative measure against crime. It gives a comprehensive mechanism that ultimately gives clients the compass of what they are up against in terms of security risk. A security risk assessment provides total control of your security if done correctly.
Security is not an alarm system or guard at your gate. Security is vital information which answers questions connected to a layered set of objectives. This information is gathered through the following:
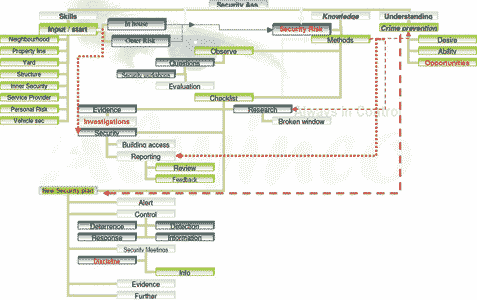
Level 1 – Outside neighborhood within 1 km radius
Assessing the greenbelt of the neighborhood or suburb, checking if there is a river, bridge, easy hiding places or squatter camps in the area. This also includes roads, available routes to your property and also possible escape routes from your property. Parks, bus stops, vacant lots and makeshift shelters close to your premises. Assessing the neighborhood also involves research on which criminals have been active in that area!
Level 2 – Property line, fencing, walls and driveway assessment
This level is commonly known as the first line of protection because it is ideally where you want to stop a potential criminal. You don’t want to find him lurking around your driveway or inside your property.
Level 3 – Area between yard, fence or walls, and the buildings – parking, garden, courtyard and backyard
Once a criminal has breached Level 2, your aim is to stop him from entering the building. This level would include the parking and courtyard areas, which are often overlooked by security companies. This level also includes your front garden and back yard. These are also the areas where criminals will sit and scope out the premises to establish how to proceed.
Level 4 – Outer structure of house, buildings and or office structure
This involves the actual building, including stairwells, balconies, patios etc. If a criminal gets this far, something is seriously wrong with the security measures you have in place.
Level 5 – Inner security of house, buildings and or office structure
This involves the actual building, including stairwells, balconies, patios etc. If a criminal gets this far, something is seriously wrong with the security measures you have in place.
Levels 6 and 7 apply to Corporate Environments only.
Level 6 – Assessment of existing appointed security service provider
The security service provider is the security company currently employed by the client. This assessment is split in two parts.
The first part is the alarm and armed response. We look at what alarm they have installed, also what hardware they have onsite. Then we look at how long it takes to respond to an activation, where does the armed response vehicles standoff between signals, are their vehicles in the neighbourhood and various other aspects?
The second and in most cases the most important part is the guards. We take a look at things like the contract the client has with this security company, and we then do an analysis on the guards themselves. We look at aspects like their training, are they registered with PSIRA, is the guard in contact with his control room, what the guards does in case of a robbery/break-in, are the guards informed and held to their set out SOPs (standard operating procedures), and other important factors?
Level 7 – Corporate management, personal risk and security
On this level we look at the corporate management, or the MD’s personal security. We look at aspects like his driving skills, where does he live, what is his home’s security like? In most cases we do personal assessment on the MD’s home as well. We look at the vulnerabilities of himself as well as his family because his family can be used against him by criminals to force him to change his mind in certain situations. We make sure that the MD is safe on all levels and various other aspects.
Level 8 – Security plan
On this level we take all existing information from the assessment into consideration and discuss options with manufacturers and or importers. We also consider the living environment and then produce a security plan, which put you in control of your security.
Level 9 – Ongoing research, as and when needed
We do ongoing research for a company with whom we have a retainer contract. That means that we are basically that company’s security office. So for the remainder of the contract we do continuous assessments of various aspects of their security and hence the ongoing research is done. In this level it is an on-going process.
1. A full security risk assessment (on-going).
2. A security plan (on-going).
3. Ongoing security research (products and threats).
4. Ongoing risk management advice to decision makers at board to accommodate changing scenarios.
5. Monthly meetings with security companies.
6. Security service levels.
7. Security standard operating procedure.
8. Annual or bi-annual security surveys/audits.
9. SAPS communication.
10. Security workshops.
11. Investigations.
12. Request quotations (RFQ) applicable from security service providers on behalf of client.
13. Advice on hiring and appointing of contractors.
14. Monthly security management reports.
For more information contact Alwinco, +27 (0)71 319 4735, aviljoen@alwinco.co.za, www.alwinco.co.za
This is the second article in the series from Alwinco discussing the various aspects of a comprehensive risk assessment.

© Technews Publishing (Pty) Ltd. | All Rights Reserved.