

Axis Communications explains storage and bandwidth considerations for surveillance.
Network bandwidth and storage requirements are important considerations when designing a video surveillance system. The factors include the number of cameras, the image resolution used, the compression type and ratio, frame rates and scene complexity. This article provides some guidelines on designing a system, along with information on storage solutions and various system configurations.
Network video products use network bandwidth and storage space based on their configuration. As mentioned earlier, this depends on the following:
* Number of cameras.
* Whether recording will be continuous or event-based.
* Number of hours per day the camera will be recording.
* Frames per second.
* Image resolution.
* Video compression type: Motion JPEG, MPEG-4, H.264.
* Scenery: Image complexity (e.g. grey wall or a forest), lighting conditions and amount of motion (office environment or crowded train stations).
* How long data must be stored.
Bandwidth needs
In a small surveillance system involving eight to 10 cameras, a basic 100-megabit (Mbit) network switch can be used without having to consider bandwidth limitations. Most companies can implement a surveillance system of this size using their existing network.
When implementing 10 or more cameras, the network load can be estimated using a few rules of thumb:
* A camera that is configured to deliver high-quality images at high frame rates will use approx. 2 to 3 Mbit/s of the available network bandwidth.
* With more than 12 to 15 cameras, consider using a switch with a gigabit backbone. If a gigabit-supporting switch is used, the server that runs the video management software should have a gigabit network adaptor installed.
Technologies that enable the management of bandwidth consumption include the use of VLANs on a switched network, quality of service (QoS) and event-based recordings.
Calculating storage needs
As mentioned earlier, the type of video compression used is one of the factors affecting storage requirements. The H.264 compression format is by far the most efficient video compression technique available today. Without compromising image quality, an H.264 encoder can reduce the size of a digital video file by more than 80% compared with the Motion JPEG format and as much as 50% more than with the MPEG-4 (Part 2) standard. This means much less network bandwidth and storage space are required for an H.264 video file.
Sample storage calculations for all three compression formats are provided in the tables below. Because of a number of variables that affect average bit rate levels, calculations are not so clear cut for H.264 and MPEG-4. With Motion JPEG, there is a clear formula because Motion JPEG consists of one individual file for each image. Storage requirements for Motion JPEG recordings vary depending on the frame rate, resolution and level of compression.
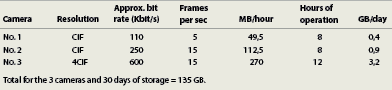
H.264 calculation
Approximate bit rate/8(bits in a byte) x 3600s = KB per hour/1000 = MB per hour
MB per hour x hours of operation per day/1000 = GB per day
GB per day x requested period of storage = Storage need
(See Table 1).
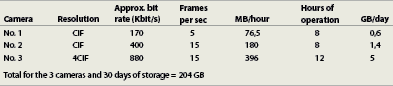
MPEG-4 calculation
Approximate bit rate/8(bits in a byte) x 3600s = KB per hour/1000 = MB per hour
MB per hour x hours of operation per day/1000 = GB per day
GB per day x requested period of storage = Storage need
Note: The formula does not take into account the amount of motion, which is an important factor that can influence the size of storage required.
(See Table 2).
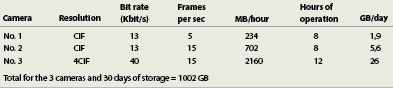
Motion JPEG calculation
Image size x frames per second x 3600s = KB per hour/1000 = MB per hour
MB per hour x hours of operation per day/1000 = GB per day
GB per day x requested period of storage = Storage need
(See Table 3).
A helpful tool in estimating requirements for bandwidth and storage is the AXIS Design Tool, found at www.axis.com/products/video/design_tool/.
Server-based storage
Depending on a PC server’s central processing unit (CPU), network card and internal RAM (Random Access Memory), a server can handle a certain number of cameras, frames per second and size of images. Most PCs can hold between two and four hard disks, and each disk can be up to approx. 300 GB. In a small to medium-sized installation, the PC that runs the video management software is also used for video recording. This is called a direct-attached storage.
With the AXIS Camera Station video management software, for instance, one hard disk is suitable for storing recordings from six to eight cameras. With more than 12 to 15 cameras, at least two hard disks should be used to split the load. For 50 or more cameras, the use of a second server is recommended.
NAS and SAN
When the amount of stored data and management requirements exceed the limitations of a direct-attached storage, a network-attached storage (NAS) or storage area network (SAN) allows for increased storage space, flexibility and recoverability.
NAS provides a single storage device that is directly attached to a LAN and offers shared storage to all clients on the network. A NAS device is simple to install and easy to administer, providing a low-cost storage solution. However, it provides limited throughput for incoming data because it has only one network connection, which can become problematic in high-performance systems.
SANs are high-speed, special-purpose networks for storage, typically connected to one or more servers via fibre. Users can access any of the storage devices on the SAN through the servers, and the storage is scalable to hundreds of terabytes. Centralised storage reduces administration and provides a high performance, flexible storage system for use in multi-server environments. Fibre Channel technology is commonly used to provide data transfers at four gigabits per second and to allow large amounts of data to be stored with a high level of redundancy.

Redundant storage
SAN systems build redundancy into the storage device. Redundancy in a storage system allows video, or any other data, to be saved simultaneously in more than one location. This provides a backup for recovering video if a portion of the storage system becomes unreadable. There are a number of options for providing this added storage layer in an IP-Surveillance system, including a Redundant Array of Independent Disks (RAID), data replication, server clustering and multiple video recipients.
RAID
RAID is a method of arranging standard, off-the-shelf hard drives such that the operating system sees them as one large hard disk. A RAID setup spans data over multiple hard disk drives with enough redundancy so that data can be recovered if one disk fails. There are different levels of RAID, ranging from practically no redundancy to a full-mirrored solution in which there is no disruption and no loss of data in the event of a hard disk failure.
Data replication
This is a common feature in many network operating systems. File servers in a network are configured to replicate data among each other, providing a backup if one server fails.
Server clustering
A common server clustering method is to have two servers work with the same storage device, such as a RAID system. When one server fails, the other identically configured server takes over. These servers can even share the same IP address, which makes the so-called “fail-over” completely transparent for users.
Multiple video recipients
A common method to ensure disaster recovery and off-site storage in network video is to simultaneously send the video to two different servers in separate locations. These servers can be equipped with RAID, work in clusters, or replicate their data with servers even further away. This is an especially useful approach when surveillance systems are in hazardous or not easily accessible areas, such as in mass-transit installations or industrial facilities.
System configurations
Small system (1 to 30 cameras)
A small system usually consists of one server running a surveillance application that records the video to a local hard disk. The video is viewed and managed by the same server. Although most viewing and management will be done at the server, a client (local or remote) can be connected for the same purpose.
Medium system (25 to 100 cameras)
A typical, medium-sized installation has a server with additional storage attached to it. The storage is usually configured with RAID in order to increase performance and reliability. The video is normally viewed and managed from a client rather than from the recording server itself.
Large centralised system (50 to +1000 cameras)
A large-sized installation requires high performance and reliability in order to manage the large amount of data and bandwidth. This requires multiple servers with dedicated tasks. A master server controls the system and decides what kind of video is stored at what storage server. As there are dedicated storage servers, it is possible to do load balancing. In such a setup, it is also possible to scale up the system by adding more storage servers when needed and do maintenance without bringing down the entire system.
Large distributed system (25 to +1000 cameras)
When multiple sites require surveillance with centralised management, distributed recording systems may be used. Each site records and stores the video from local cameras. The master controller can view and manage recordings at each site.
| Tel: | +27 11 548 6780 |
| Email: | [email protected] |
| www: | www.axis.com |
| Articles: | More information and articles about Axis Communications SA |

© Technews Publishing (Pty) Ltd. | All Rights Reserved.